One of my hobbies is reading and listening to audiobooks. To add some variety to the site I list the books I read each year and provide mini reviews. This is an exercise for to help me remember more of what I read, to suck less at writing, and evaluate…
1 CommentAbraxas.io Posts
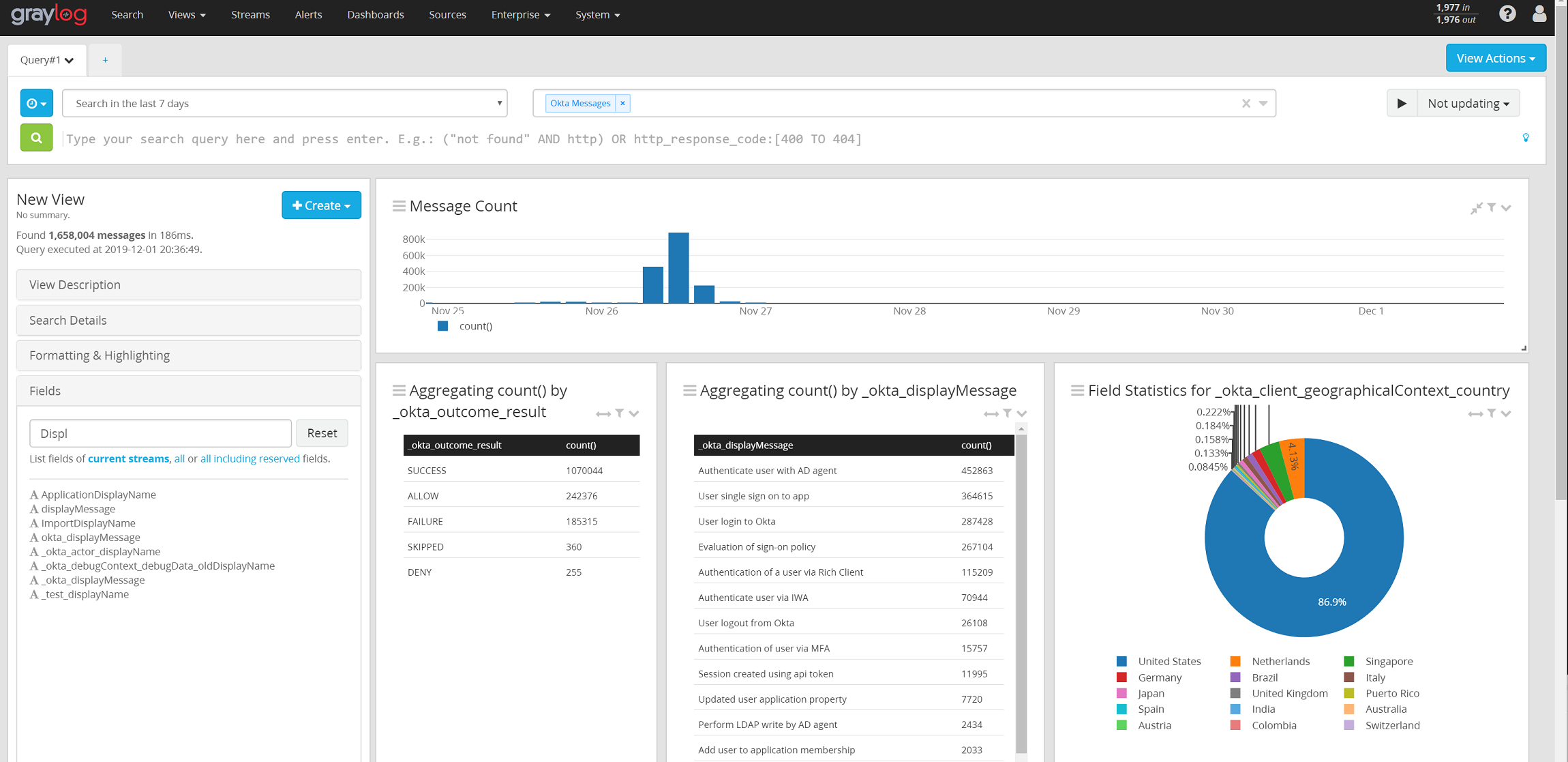
Graylog & Okta – Integration Walkthrough
Okta is a Single Sign-On identity provider with a lot of nice features to do advanced identity management. This post covers how to integrate the System Log from Okta, which contains all of it’s audit events, and connect it to a Graylog system. This is part of a series of…
10 CommentsRITSEC CTF 2019
RITSEC 2019 happened this past weekend (11/17/2019) and a friend and I decided to have a go at it. The following is a writeup of most of the solutions we came up with except a few I didn’t document 🙁 PWN This was our weakest category with only one solve.…
Leave a CommentIntroducing Neith
A project I’ve worked on for the past month is now online – Introducing Project Neith! About a year ago I while surfing the web, I came across a tool called ‘PowerShell UniversalDashboard’ made by Adam Driscoll. (https://github.com/adamdriscoll) It makes creating webapps with PowerShell not only possible, but very easy.…
Leave a CommentBook and Review List – 2019
I wanted to add a bit of a personal flair to the site. One of my hobbies is reading and listening to audiobooks so I figured I’d throw down mini-reviews of each book I read throughout the year and leave them here. This is mostly an exercise for me to…
1 CommentBook and review list – 2018
I wanted to add a bit of a personal flair to the site. One of my hobbies is reading and listening to audiobooks so I figured I’d throw down mini-reviews of each book I read throughout the year and leave them here. This is mostly an exercise for me to…
1 CommentLayerOne 2018 CTF – Forensics Challenges
LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I’ve participated in. This is the third in a series of a few post I am writing which goes over the solution of some of the CTF challenges. This post covers some forensics…
Leave a CommentLayerOne 2018 CTF – Web Category
LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I’ve participated in. This is the third in a series of a few post I am writing which goes over the solution of some of the CTF challenges. This post covers Web challenges.…
Leave a CommentLayerOne 2018 CTF – Cyber Kill Chain Category
LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I participate in. This is the second in a series of a few post I am writing which goes over the solution of some of the CTF challenges. These challenge emphasize the importance…
Leave a CommentLayerOne 2018 CTF – Blockchain Challenge Category
LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I participate in. This is the first in a series of a few post I am writing which goes over the solution of some of the CTF challenges. The Challenges This first write-up…
Leave a Comment