LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I participate in. This is the second in a series of a few post I am writing which goes over the solution of some of the CTF challenges. These challenge emphasize the importance of reconnaissance!
The Challenges
Unlike the previous post, this post goes over 3 separate challenges and actually solves them as intended. The category is “Cyber Kill Chain lvl 1” and it consists of the following three challenge:
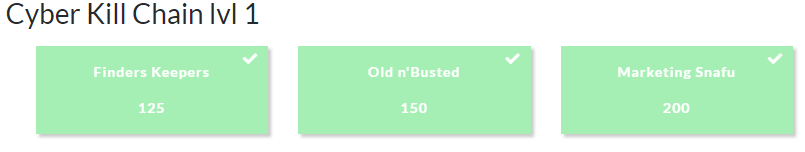
This write-up tackles all three of the challenges in order and these three challenges are great illustrations of some of the initial reconnaissance objectives performed on most external penetration tests or red team engagements.
Finders Keepers
Description for this challenge is “OH at pwnzichain sales mtg: “No one’s going to find that site anyway””
Some other challenges in this series referenced the ‘www.pwnzichain.com’ website. This sounds like an enumeration challenge and my preferred dns enumeration tool is dnsrecon. I loaded up dnsrecon with the following: python dnsrecon.py -d pwnzichain.com -D subdomains-top1mil-5000.txt -t brt
This command tells the script to bruteforce (-t brt) the domain pwnzichain.com (-d pwnzichain.com) using the wordlist with the 5000 most common subdomains (-D subdomains-top1mil-5000.txt).
root@AttackVM:/home/abraxas/Battalion/tools/dnsrecon# python dnsrecon.py -d pwnzichain.com -D subdomains-top1mil-5000.txt -t brt
[*] Performing host and subdomain brute force against pwnzichain.com
[*] A dev.pwnzichain.com 34.220.204.142
[*] CNAME www.pwnzichain.com d1bbtdllso51tg.cloudfront.net
[*] A d1bbtdllso51tg.cloudfront.net 52.84.235.215
…………….
[*] A d1bbtdllso51tg.cloudfront.net 52.84.235.94
[*] CNAME www.pwnzichain.com d1bbtdllso51tg.cloudfront.net
[*] CNAME stats.pwnzichain.com master.pwnzichain.com
[*] A master.pwnzichain.com 54.186.241.167
[*] A master.pwnzichain.com 54.186.241.167
[*] A partners.pwnzichain.com 34.220.204.142
[*] CNAME dashboard.pwnzichain.com master.pwnzichain.com
[*] A master.pwnzichain.com 54.186.241.167
[*] CNAME WWW.pwnzichain.com d1bbtdllso51tg.cloudfront.net
[*] A d1bbtdllso51tg.cloudfront.net 52.84.235.49
…………….
[*] A d1bbtdllso51tg.cloudfront.net 52.84.235.215
[*] CNAME WWW.pwnzichain.com d1bbtdllso51tg.cloudfront.net
[*] 35 Records Found
A few of these I had seen from other challenges but two were new to me:
partners.pwnzichain.com and dev.pwnzichain.com
dev.pwnzichain.com appeared to be empty but partners.pwnzichain.com had something which looked like the flag!
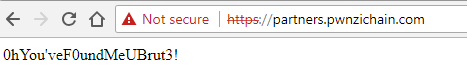
I entered this as the flag and picked up the points!
Old n’Busted
The description for this challenge is:
#####
Someone left an broken dev server up but it seems that there’s nothing of interest there…or is there?
http://dev.pwnzichain.com
######
When going to http://dev.pwnzichain.com you get redirected to the https site but it is completely empty. I tried to use tools like dirbuster to enumerate pages, ran a separate DNS enumeration on the entire dev.pwnzichain.com domain, checked wayback machine and google for cached versions of the site and had no luck with any of these attempts.
After looking around the various other sites and still coming up with nothing I started looking at the https certificate. In the certificate viewer once I scrolled down I saw something interesting a SAN name!
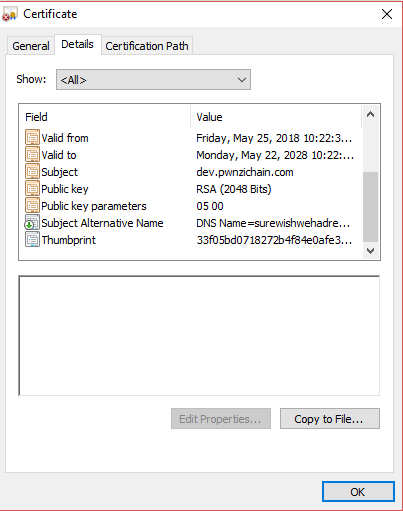
The full value of the SAN name was: surewishwehadrememberedtoturnthisoff.pwnzichain.com
On accessing this site the flag was listed right away. Two down and one to go!
Marketing Snafu
I, unfortunately, can’t say I had anything to do with the solution of this one apart from possibly causing some gears to turn by mentioning that the SSL cert had been the key to the second challenge. The description of this challenge is:
########
Pwnzichain marketing team has lost track of one of their secure web properties, can you help them find their missing site?
########
I tried a far more comprehensive DNS brute force, some google dorks for known subdomains of pwnzichain.com, used dnstwist to look for typosquatted domains which were similar (letter mutations, etc.) to pwnzichain.com and had no luck with any of it. I was stepping away from this problem as I knew another teammate on winterf3ll was looking at it. It turned out the key was certificate transparency.
My teammate tried to compile a bunch of custom tools to dig around with cert transparency but did not have any luck. Eventually he found this handy website: https://crt.sh This turned out to be the key to solving the challenge.
Essentially, by looking through certificate transparency logs for a domain, you can find the fingerprints and other information about certificates registered for those domains. crt.sh has a handy feature which allows you to insert a wildcard. Our search looked like the following:
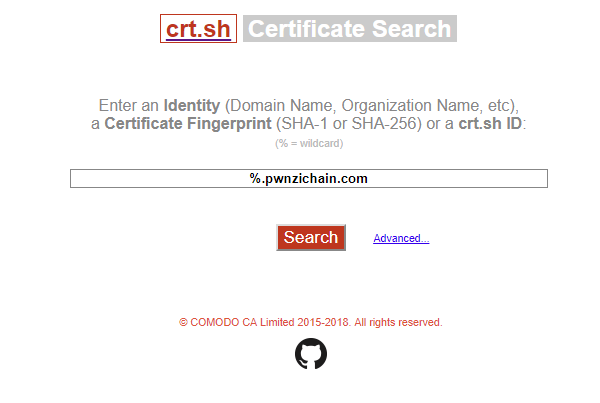
This handy search showed a lot of certs including a few with weird names:
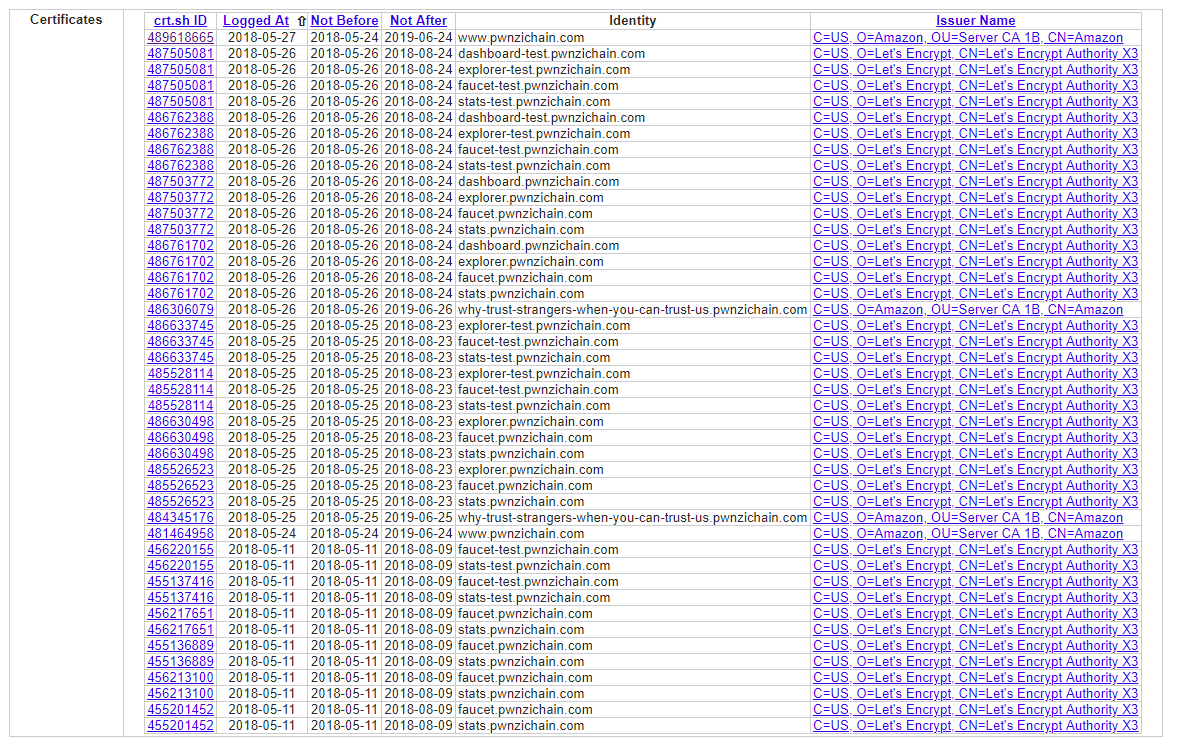
The really long one of course turned out to be the subdomain we searched for. The flag was located at: why-trust-strangers-when-you-can-trust-us.pwnzichain.com
Takeaways
All three of these challenges were based on reconnaissance. The first, and some of the web challenges, were typical enumeration and reconnaissance tasks. Find stuff in dns, find robots.txt, search for key files on webservers, etc. However, the latter two challenges included tasks which I think aren’t performed as often in penetration testing. digging through certificate data in this case proved more useful than searching through whois records or other things typically scanned.
The takeaway, as it often is in these CTFs, is to enumerate harder!