Summary This was a really cool CTF! It was put on by HouSecCon (Hou.Sec.Con) and Idaho National labs. A few things I really liked about it: Final scores! Huge congrats to CoB for a late night rally and taking the win! Challenges There were upwards of 100 challenges in the…
Leave a CommentCategory: Security
LayerOne 2024 CTF
The Conference The LayerOne conference has been a highlight for me each year since I started hacking and doing security things. I highly recommend it for anyone interested in security, electronics, radio, computers, or anything to do with hacking. It tends to emphasize getting hands on and learning through experience…
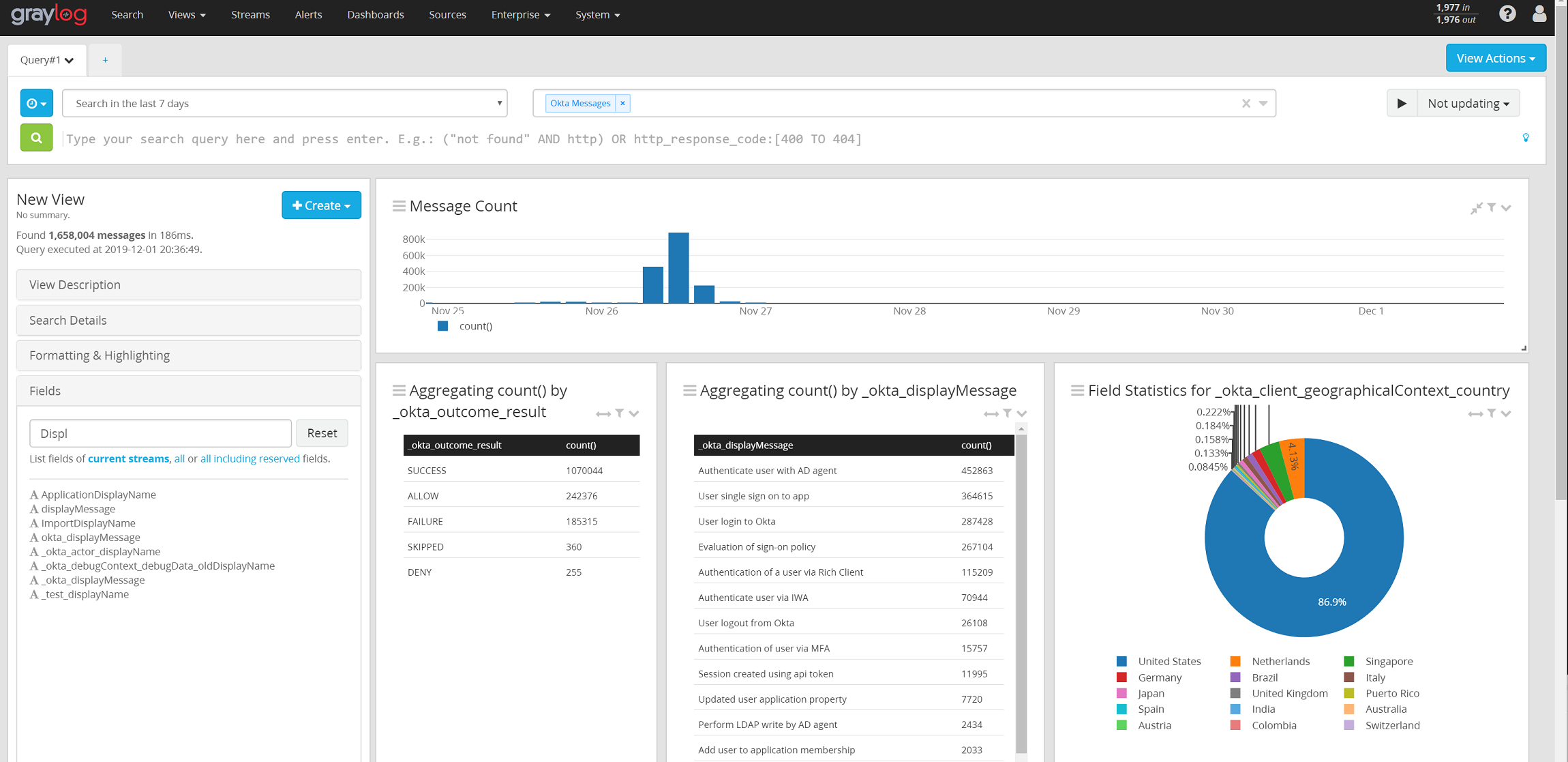
Leave a CommentGraylog & Okta – Integration Walkthrough
Okta is a Single Sign-On identity provider with a lot of nice features to do advanced identity management. This post covers how to integrate the System Log from Okta, which contains all of it’s audit events, and connect it to a Graylog system. This is part of a series of…
10 CommentsIntroducing Neith
A project I’ve worked on for the past month is now online – Introducing Project Neith! About a year ago I while surfing the web, I came across a tool called ‘PowerShell UniversalDashboard’ made by Adam Driscoll. (https://github.com/adamdriscoll) It makes creating webapps with PowerShell not only possible, but very easy.…
Leave a CommentPhish Yourself! – A practical guide to running an internal phishing campaign.
Social engineering, in particular through the medium of email, is very likely the greatest threat to an average organization. While 0-days do come around and pose real threats to organizations and many of them do not implement strong patch management programs, phishing is simply easier and more effective for the…
1 CommentRecon Part 4 – theHarvester and Recon-ng
TheHarvester I’m going to present this tool in two ways to show simultaneously how cool this utility is and the slightly less impressive way it is actually done: What appears to happen: Type in a username, receive a list of sites that user exists as a member. Type in a…
Leave a CommentBattalion – Automating Recon
Introducing Battalion Over the past 2.5 months a friend – @eidolonpg – and I have been working on a tool which was spawned from the previous articles written here. If you’ve read the past few posts have been about ‘Reconnaissance’ and, lately, chaining various recon tools together you’ll understand how this…
Leave a CommentRecon Part 3.5 – HaveIBeenPwned?
This is a quick write-up on the amazing HaveIBeenPwned Database maintained by Troy Hunt. https://haveibeenpwned.com. If you haven’t seen it, check it out! I recently discovered there isa public API to query the breach databases and decided I wanted to notify employees at my company if their account was involved…
Leave a CommentRecon Part 3 – Gobuster and EyeWitness
Gobuster TheColonial wrote a really cool tool called Gobuster which is similar to fierce but programmed in Go. I wanted to include it here because I tend to have better performance using this tool than fierce, by a LOT. Gobuster can be found on github here. There are a few issues to…
Leave a CommentRecon Part 2 – Fierce, nslookup, and dig
Fierce Fierce is a DNS brute-force scanner which comes bundled with the Kali Linux distro. Since we’re not using Kali let’s get and configure fierce from the github project’s page: https://github.com/davidpepper/fierce-domain-scanner First, let’s create a ‘Recon’ folder where we will put our tools. Now that we’ve created our recon folder, let’s…
Leave a Comment