Hackvent is a 24 day CTF which started on December 1. Each day they release a new challenge. I’ll document my solutions for each of the challenges here. The challenges have a flag in the form of HV19{...} This is part of a series of posts on CTFs, more posts from other CTFs can be found here. I unfortunately kept up for the first week or so before getting distracted and not continuing with the challenges. Here are the ones I got through.
Hackvent – HV19.01 – Censored
Description: I got this little image, but it looks like the best part got censored on the way. Even the tiny preview icon looks clearer than this! Maybe they missed something that would let you restore the original content?

Strategy: Based on the description it seems like there is a higher quality version of the image in the thumbnail part of the jpeg. I used exiftool with this command string in order to extract the thumbnail as a separate file so I could open it in GIMP (I’m sure there’s some way to naively open it there but…oh well.) exiftool -b -ThumbnailImage ../f182d5f0-1d10-4f0f-a0c1-7cba0981b6da.jpg > derp.jpg
This image looks more like a QR code. I zoomed in and scanned it with my phone to get the flag!

Solution: HV19{just-4-PREview!}
HV19.02 – Triangulation
Description: Today we give away decorations for your Christmas tree. But be careful and do not break it.
Strategy: It came with a .zip file which contained a file called ‘triangulations.stl’ I tried to open this and found that it is a stencil file. I ran binwalk and exiftool just to check if anything obvious popped up but nothing did. After that failed, I switched to an online stl viewer and it rendered an object lika Christmas ornament with a History channel logo on it. (Viewer located at: https://viewstl.com)
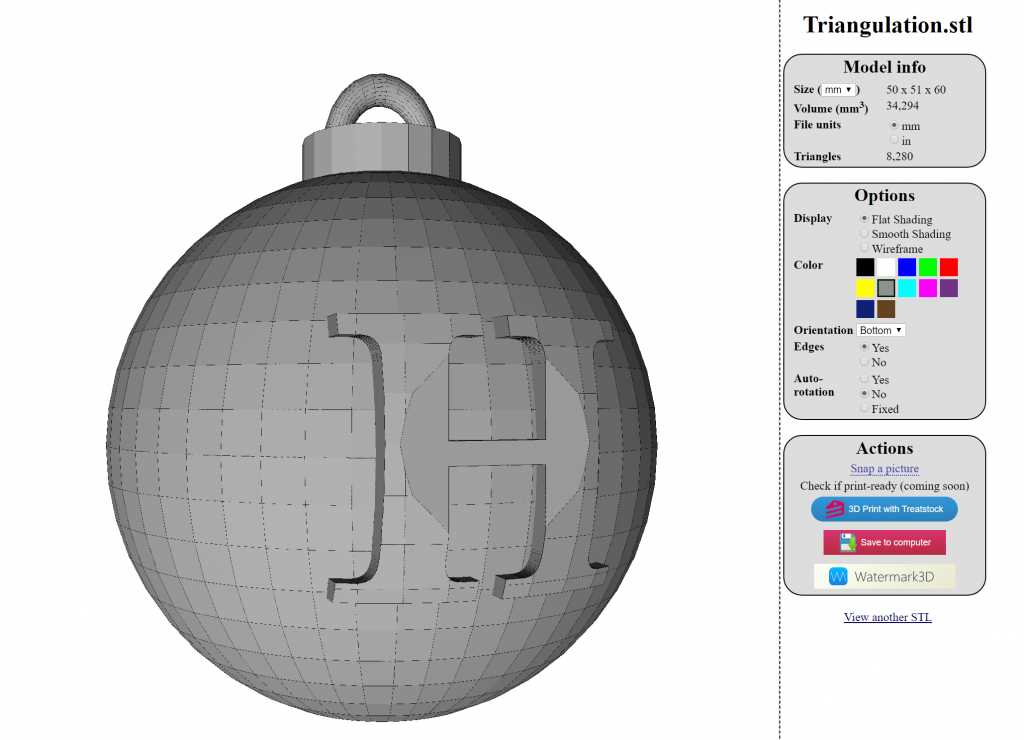
I switched it to ‘wireframe’ after nothing obvious showed up. This rendered another sphere inside of the stencil with some data possibly written out in it.
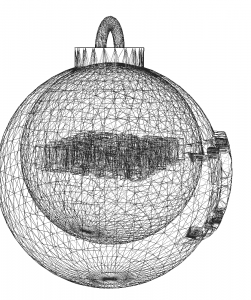
I decided I’d better get a stencil editor to see if I could remove the outer layers. For this task I used “FreeCAD” which is pretty cool from what I can tell. The inside layer looks like a grid with maybe another QR code inside of it when viewed from the top. There is too much noise to extract it manually.
I was able to make a few layers transparent and then fill in the remaining internally layers to get this view. It almost looks like a QR Code.
QR codes have the squares in the corners but this does not. I looked up image encoding similar to QR codes and it turns out that this is an ‘Aztec Code’. The next step was to turn the grey and red colors black and turn the background white. Once completed, we can scan the code!
I took a screenshot with Paint 3D to remove all the background colors and replace the grey and red with black. The end result is the image below which I was able to scan for the flag!

Flag: HV19{Cr4ck_Th3_B411!}
Hackvent – HV19.03 – Hodor.Hodor.Hodor
Description:

$HODOR: hhodor. Hodor. Hodor!? = `hodor?!? HODOR!? hodor? Hodor oHodor. hodor? , HODOR!?! ohodor!? dhodor? hodor odhodor? d HodorHodor Hodor!? HODOR HODOR? hodor! hodor!? HODOR hodor! hodor? !
hodor?!? Hodor Hodor Hodor? Hodor HODOR rhodor? HODOR Hodor!? h4Hodor?!? Hodor?!? 0r hhodor? Hodor!? oHodor?! hodor? Hodor Hodor! HODOR Hodor hodor? 64 HODOR Hodor HODOR!? hodor? Hodor!? Hodor!? .
HODOR?!? hodor- hodorHoOodoOor Hodor?!? OHoOodoOorHooodorrHODOR hodor. oHODOR... Dhodor- hodor?! HooodorrHODOR HoOodoOorHooodorrHODOR RoHODOR... HODOR!?! 1hodor?! HODOR... DHODOR- HODOR!?! HooodorrHODOR Hodor- HODORHoOodoOor HODOR!?! HODOR... DHODORHoOodoOor hodor. Hodor! HoOodoOorHodor HODORHoOodoOor 0Hooodorrhodor HoOodoOorHooodorrHODOR 0=`;
hodor.hod(hhodor. Hodor. Hodor!? );
So…this is an interesting one. Not really sure how to approach it.
HV19{}
HV19.04 password policy circumvention
Description:
Santa released a new password policy (more than 40 characters, upper, lower, digit, special). The elves can’t remember such long passwords, so they found a way to continue to use their old (bad) password:
merry christmas geeksSolution: The zip file contains a file ending with .ahk which, when opened in a text editor reads:
::merry::
FormatTime , x,, MM MMMM yyyy
SendInput, %x%{left 4}{del 2}+{right 2}^c{end}{home}^v{home}V{right 2}{ASC 00123}
return
::christmas::
SendInput HV19-pass-w0rd
return
:*?:is::
Send - {del}{right}4h
:*?:as::
Send {left 8}rmmbr{end}{ASC 00125}{home}{right 10}
return
:*?:ee::
Send {left}{left}{del}{del}{left},{right}e{right}3{right 2}e{right}{del 5}{home}H{right 4}
return
:*?:ks::
Send {del}R3{right}e{right 2}3{right 2} {right 8} {right} the{right 3}t{right} 0f{right 3}{del}c{end}{left 5}{del 4}
return
::xmas::
SendInput, -Hack-Vent-Xmas
return
::geeks::
Send -1337-hack
return
.ahk files are a type of script AutoHotkeys, a macro and scripting tool for Windows. When we launch the script with that tool it modifies the keys we type. By typing merry christmas geeks into a text file while the script is running, our text is transformed into the answer.
Flag:HV19{R3memb3r, rem3mber - the 24th 0f December}
HV19.06 bacon and eggs
Description: Below is the challenge text as it was provided.
Francis Bacon was an English philosopher and statesman who served as Attorney General and as Lord Chancellor of England. His works are credited with developing the scientific method and remained influential through the scientific revolution. Bacon has been called the father of empiricism. His works argued for the possibility of scientific knowledge based only upon inductive reasoning and careful observation of events in nature.
Most importantly, he argued science could be achieved by use of a sceptical and methodical approach whereby scientists aim to avoid misleading themselves. Although his practical ideas about such a method, the Baconian method, did not have a long-lasting influence, the general idea of the importance and possibility of a sceptical methodology makes Bacon the father of the scientific method.
Solution:
After googling and looking through various ciphers, I found the “Bacon Cipher” which encodes ascii data in 5-character patterns. For instance, five standard ascii characters are interpreted as aaaaa, four standard ascii characters and an italicized character or bold character is rendered as aaaab. aaaaa is translated as A, aaaab is translated as B, and so on.
I manually wrote out the mapping of regular and italicized characters to a‘s and b‘s. After mapping those to their Bacon-cipher character mappings and got this code:
SANTA LIKES HIS BACON BUT ALSO THIS BACON.
THE PASSWORD IS HVXBACONCIPHERISSIMPLEBUTCOOLX
REPLACE X WITH BRACKETS AND USE UPPERCASE
Flag: HV19{BACONCIPHERISSIMPLEBUTCOOL}
HV19.07 Santa Rider
Description: Santa is prototyping a new gadget for his sledge. Unfortunately it still has some glitches, but look for yourself.
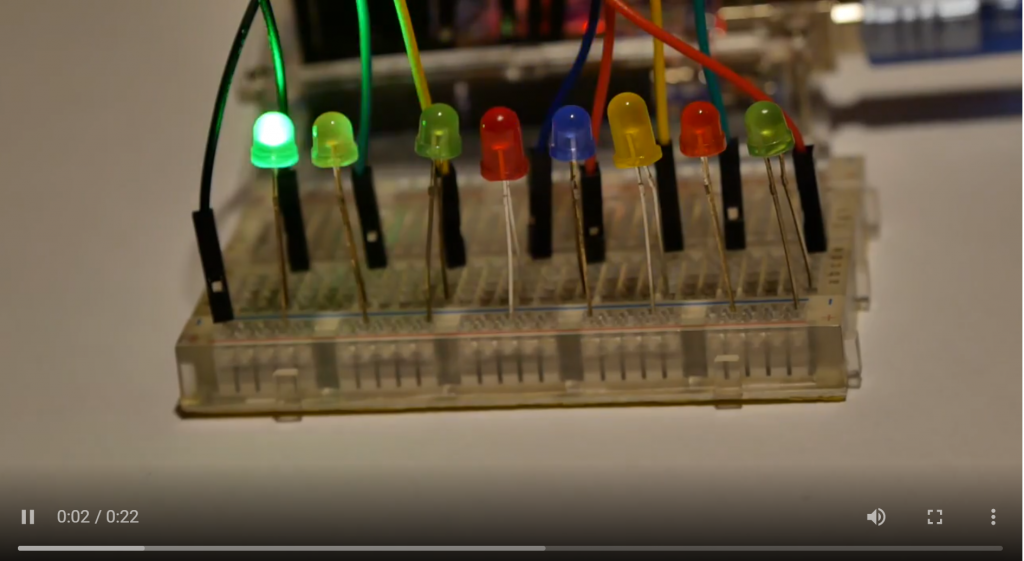
Solution:
This challenge is a bit tedious. We are given a video of a series of 8 LEDs flashing in a seemingly random pattern. The eight lights immediately corresponded with the concept of 8 bits in a byte. I went frame-by-frame through the video and wrote out the binary for each frame. This ultimately provided a list of ASCII characters which provided the correct flag.
Flag: HV19{1m_als0_w0rk1ng_0n_a_r3m0t3_c0ntr0l}
