LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I’ve participated in. This is the third in a series of a few post I am writing which goes over the solution of some of the CTF challenges. This post covers some forensics challenges.
The Challenges
This category consisted of two challenges
LayerOne – Wallet Recovery – (200)
The description for this challenge is: “I backed up my keystore but it got deleted. Can you recover it from this disk dump?”
This link downloaded a 2gb .zip file which extracted to a ‘.raw’ file. Running the file command provides the following information:

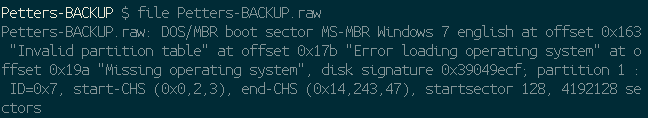
This leads me to believe that the disk might be part of a windows image. I downloaded a windows disk mounting program (osfmount – https://www.osforensics.com/tools/mount-disk-images.html) I installed the program and then mounted the disk:
Once mounted I navigated over to see what was on the disk!
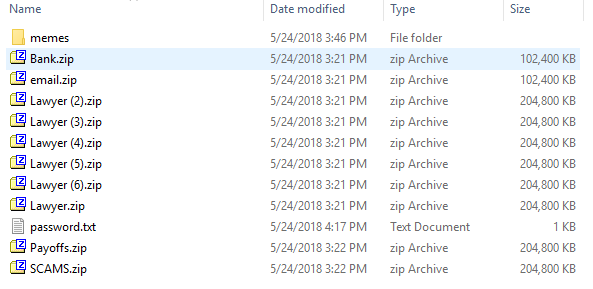
password.txt included the following data:
PWNZICHAINPONZISCHEME
This was, however, not the flag. Many of the archives did not appear to open so I decided to go with the tip provided and checked to view hidden files and OS files. This showed me two me folders:
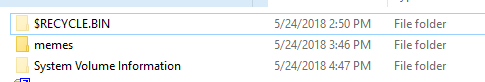
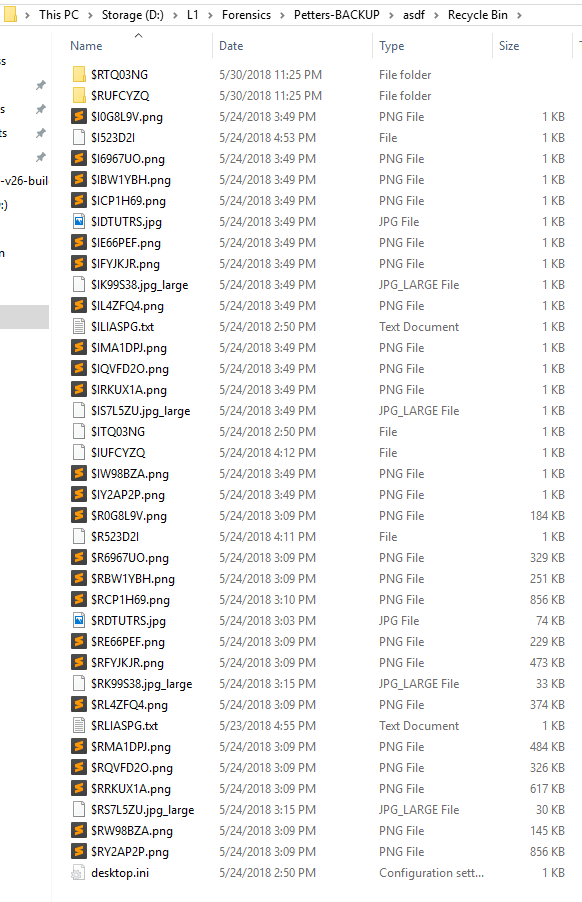
I tried to go in to the folder and saw a UID directory but was unable to access it. Since it was mounted as read only, I
decided to copy the entire directory to a disk I owned and that appeared to work.
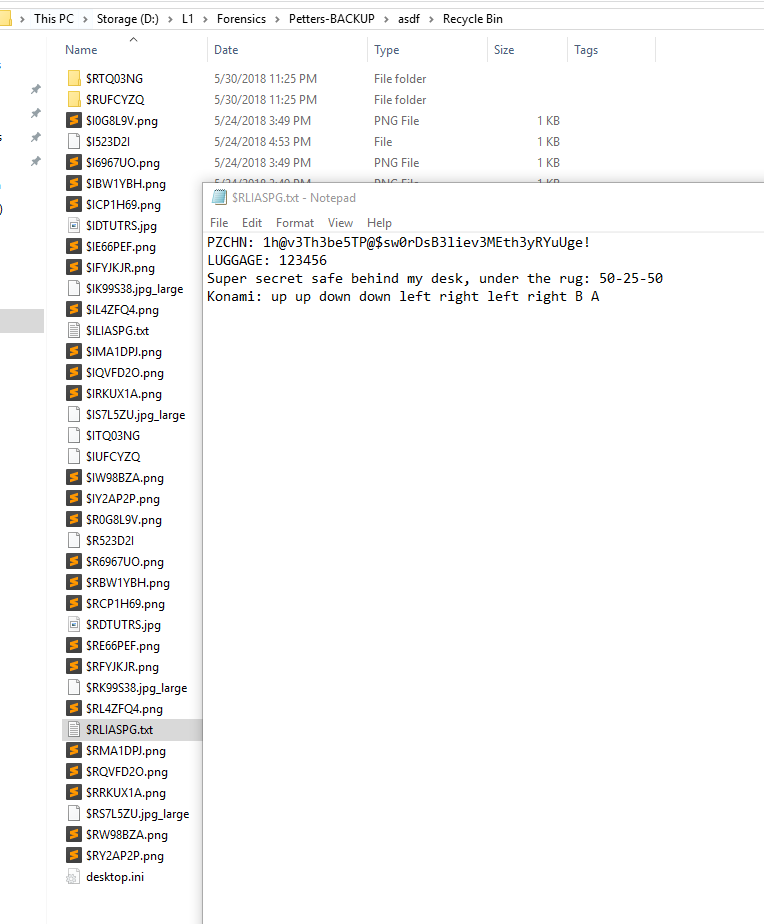
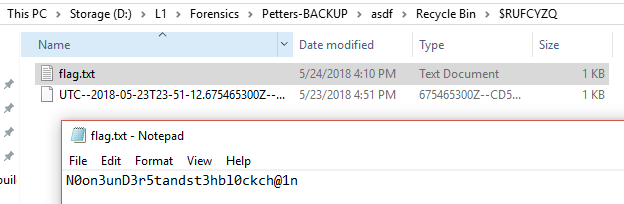
I found this flag in one of the text files:
On to the next LayerOne Challenge!
LayerOne – Wallet Password Recovery – (300)
BUT WAIT, THERE’S MORE!!!
Instead of just ending here, I wanted to take a minute to actually do these challenges in a more interesting way using a kickass tool called volatility which is amazing to use for forensics and forensics challenges and which has been useful in past LayerOne CTFs!
I decided to take the memory image provided and load it up in volatility to see if there were any running processes:
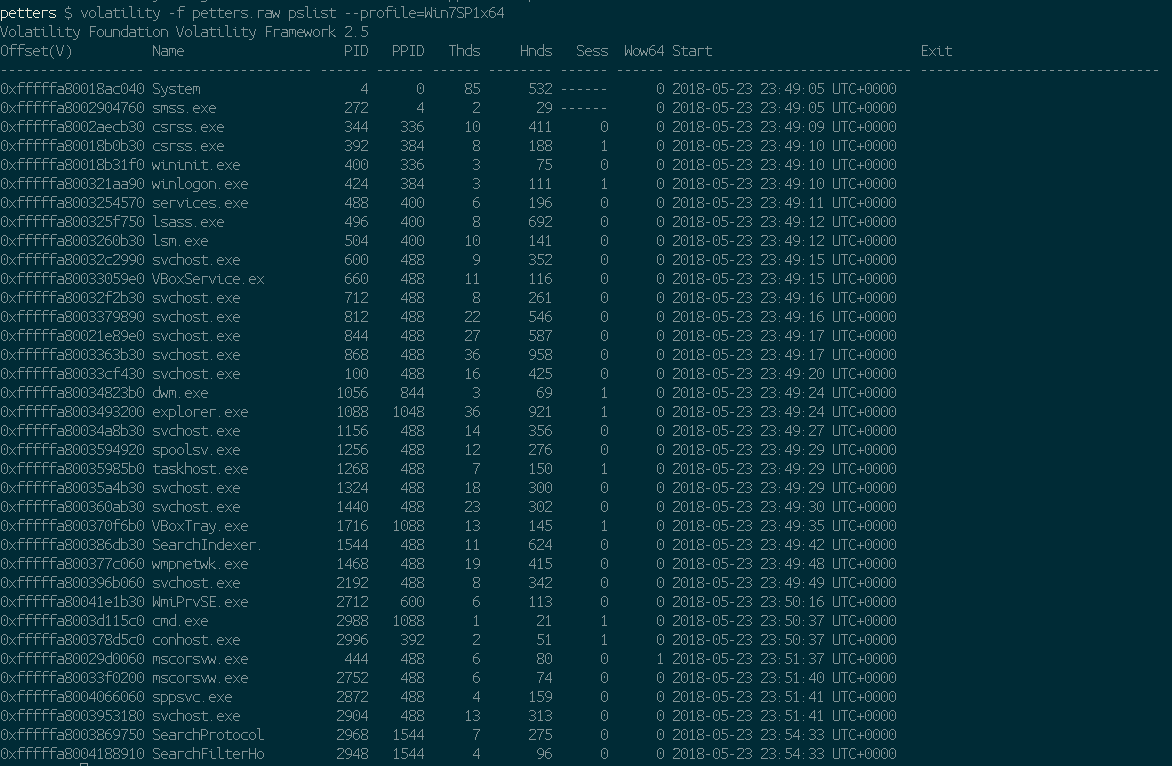
The --profile flag is used to declare the type of memory image we are giving volatility, the command pslist gives it the instruction to identify running processes. I was hoping to see something like ‘notepad.exe’ or similar which would allow us to easily find the memory of a given text file which may have the flag. This didn’t work.
My next thought was to try to list .txt files. I used the following command: `volatility -f petters.raw filescan –profile=Win7SP1x64 | grep “.txt” | grep -v “\Windows\”` which will search for ‘files’ in the memory dump that include ‘.txt’ in the name but which also do not include “\Windows\” in the path (excludes most system files).
This returned a far more interesting result:
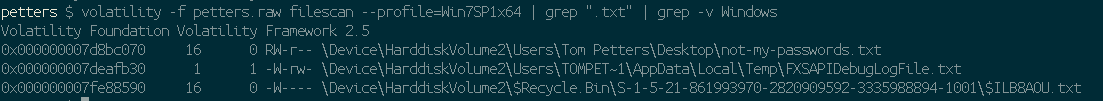
The first and the last results look pretty interesting here, I’m going to trust they’re not lying and ignore the first line and instead look for the file on the last line. The value on the left which starts with 0x000 is a memory address of where the file is.
Another awesome feature volatility offers is the ability to extract files from a memory dump. You can do this en masse but there shouldn’t be a need for that in this instance. Since we know the address of the file we’re looking for I’m just going to try to snag that file.
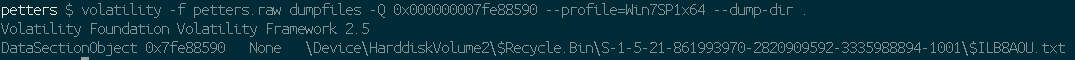
There we go! the dumpfiles -Q <start_of_file_address> and the --dumpdir . specify which file to target and where to extract it.
Did it work?
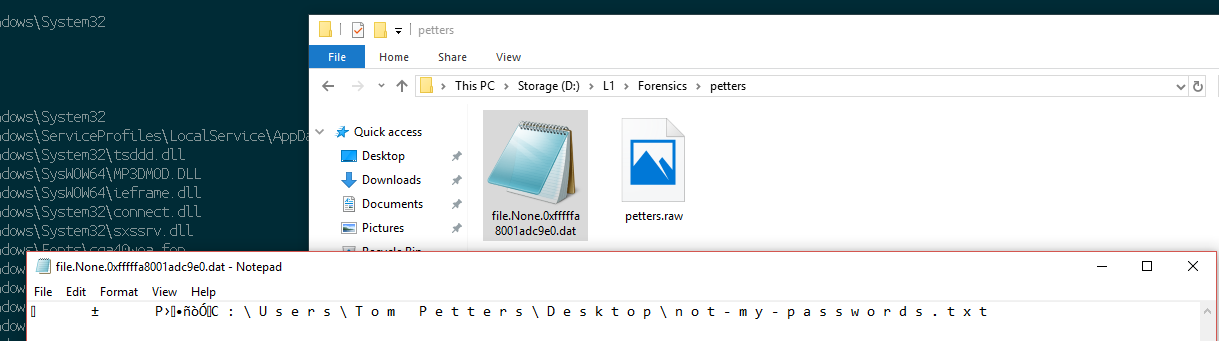
Nope 🙁
We still have another viable option! Let’s try the memory address of the first file – the not-my-passwords.txt file.

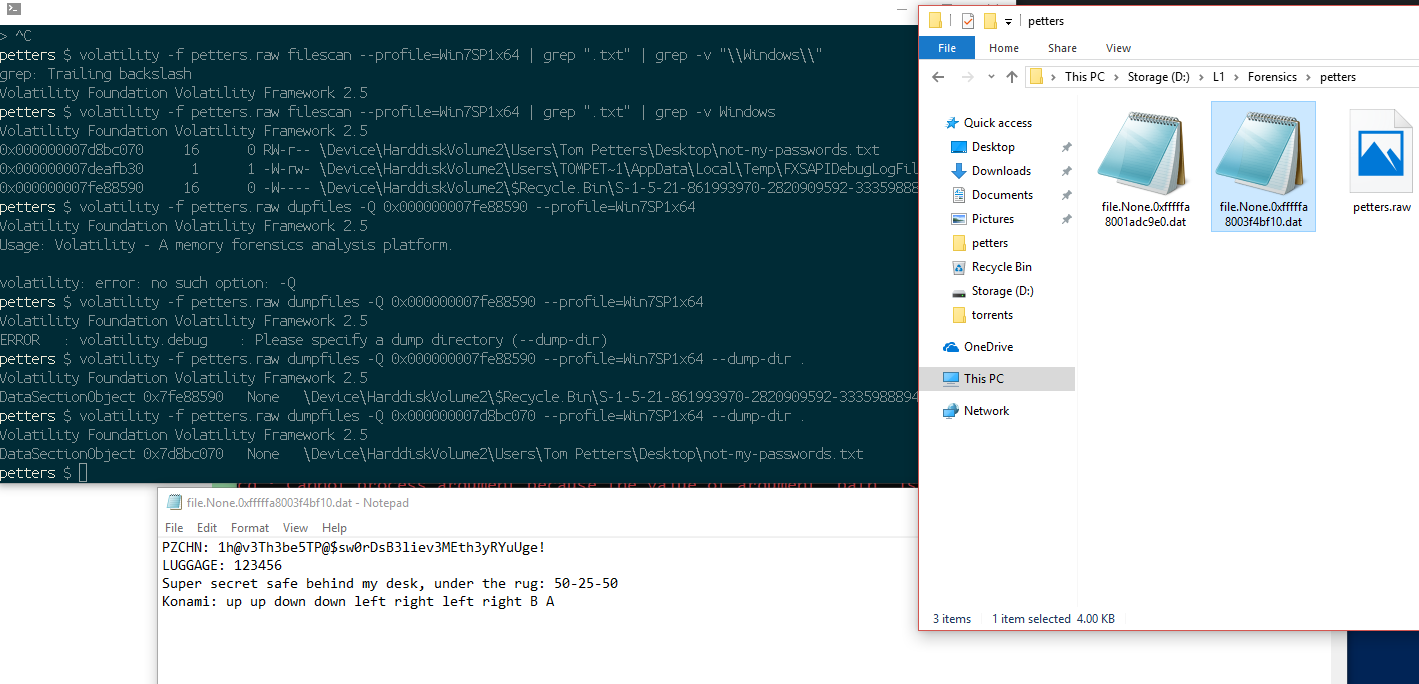
And there we go! That’s the file we found earlier and the flag we wanted.
That’s all for this tutorial! 500 points for some pretty fun forensics challenges!
If you’re interested in doing CTFs feel free to message me on twitter @AbraxasSC2 or to check out https://ctftime.org as there are almost always great events going on! Thanks to LayerOne for such an awesome event!
Thanks for reading!