LayerOne is an information security conference in LA which hosts one of the more enjoyable CTFs that I participate in. This is the first in a series of a few post I am writing which goes over the solution of some of the CTF challenges.
The Challenges
This first write-up will deal with getting some points I definitely didn’t deserve on team winterf3ll. I’ll be doing several write-ups on the various categories from this event. This first one deals with the ‘Blockchain’ category. Thanks to the @LayerOneCTF guys for putting together this great event and @Layer_One for running such an outstanding conference!
The first category I’ll go over is the ‘Blockchain’ category which consists of four challenges, listed below:
- Founder’s Folly
100
One of the founding members of PwnziChain has made a disastrous mistake, and threw away a large portion of his hard-earned PwnziCoin fortune!
https://dashboard.pwnzichain.com/#connect
- Needle in a Blockchain
200
Some people say our illustrious PwnziChain founder had gone mad, because he kept claiming to see secret messages appearing in the blockchain.
https://dashboard.pwnzichain.com/#connect
- PwnziKeeper 1
PwnziKeeper 1
200
PwnziChain is proud to introduce a new smart contract for storing secrets on the blockchain! Now, the same central authority you already trust to keep your valuable coins safe can also keep your passwords and other private information safe as well. Check it out today!
Address: 0xee9ab0511bc475f732f9068a276fe793bfc20a3d
https://dashboard.pwnzichain.com/#connect
- PwnziKeeper 2
350
PwnziChain is pleased to announce our new and improved version of the PwnziKeeper smart contract! We’ve heard from you about your security concerns with the previous version of PwnziKeeper, and have added additional security to this new version by implementing our proprietary obfuSCATe™ technology. Try it out today!
Address: 0x509f1d9a781a5909a4df83b45701d65d2d896a2e
https://dashboard.pwnzichain.com/#connect
All of the following challenges ended up being solved the same way – I do not believe this is how they were intended to be solved. This is not a going to teach you much about using geth or anything else about the blockchain. Instead, the only thing to take away from this writeup is that enumeration and investigation is important.
Solving the Challenges
Founder’s Folly (the first challenge) is one of the first challenges I looked at since I thought the blockchain category would be interesting. I clicked the link and landed on this page:
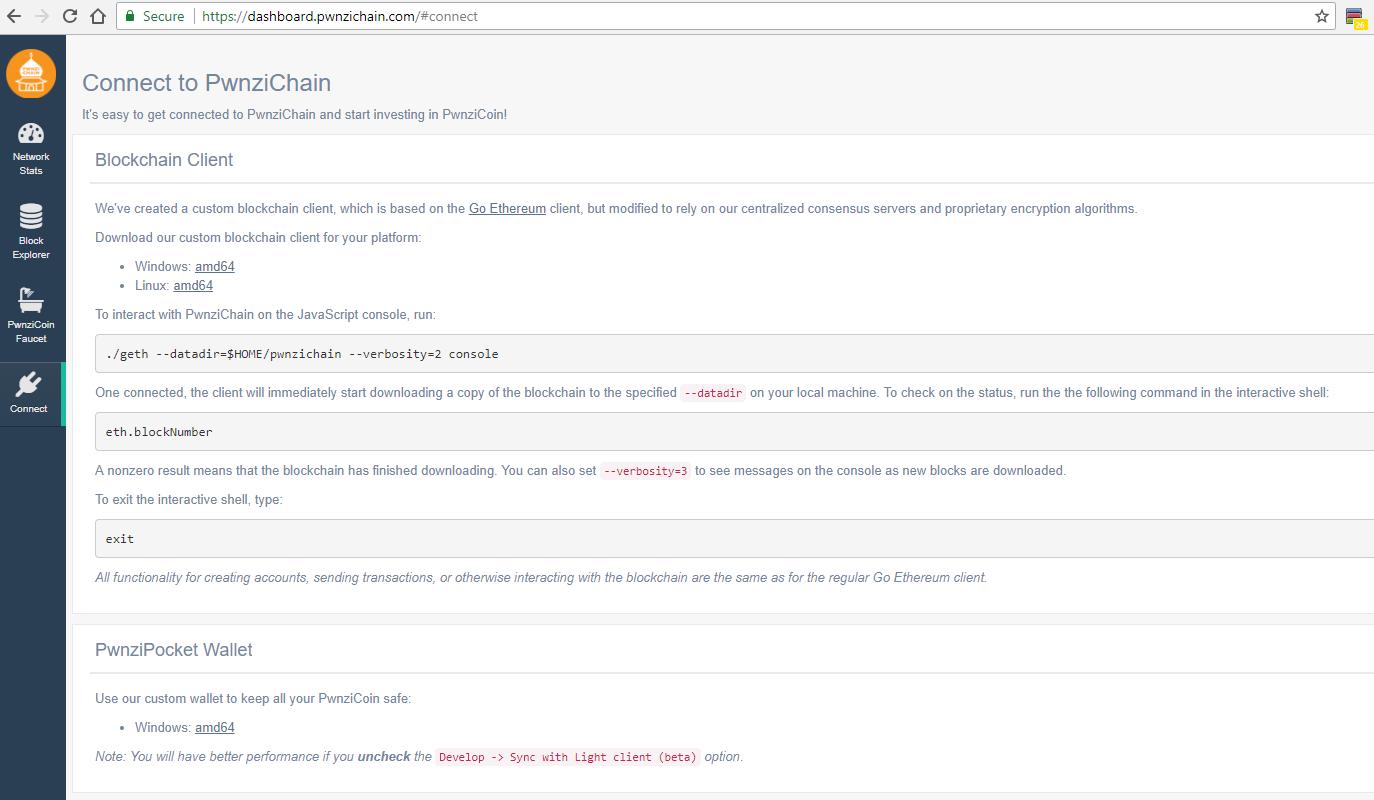
I went ahead and decided to run the blockchain client and ran the recommended ./geth command. ./geth --datadir=D:/L1/blockchain --verbosity=2 console
Once it ran I saw something like this:
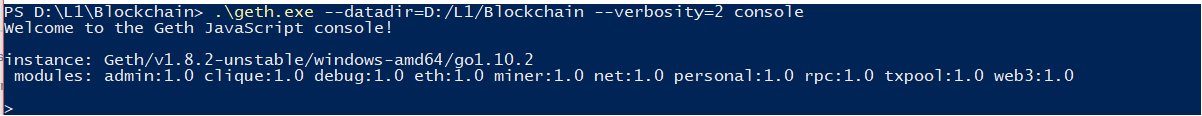
Next I looked up “Go ethereum” and saw it was a well maintained project. I started running some of the commands I saw on different sites (main geth client, here: https://github.com/ethereum/go-ethereum)
I tried doing some actions in the console and saw the following:
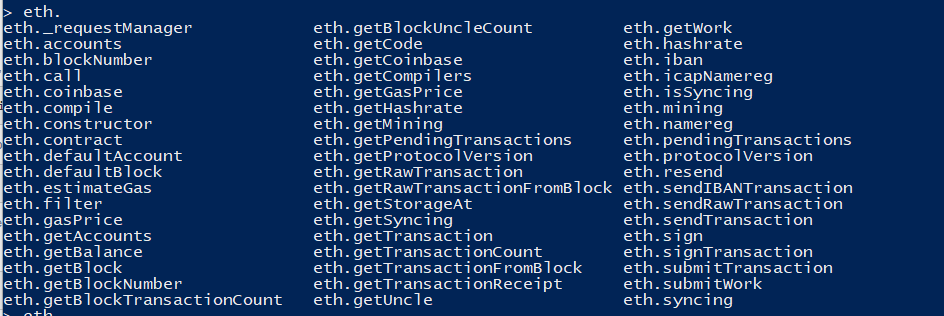
The above appear to be various commands I can run from the geth client. Most returned an ‘undefined’ or ‘[]’ response but a few spit out data, one of the more verbose was here:
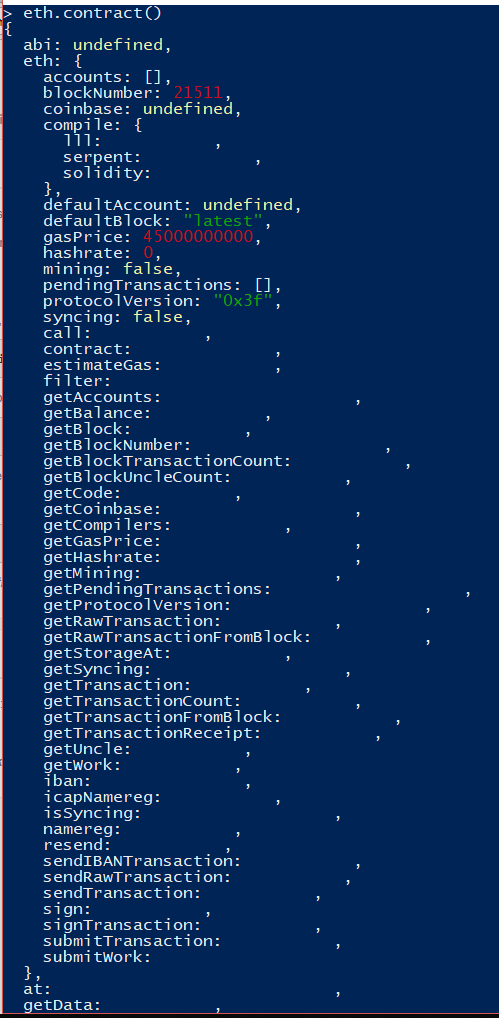
Finding the flags!
Seeing this and all of the various articles written about the tool I decided to look in the ‘datadir’ which was generated with the script. There was a ‘geth’ directory and a ‘keystore’ directory. The keystore was empty but ‘geth’ had a number of files and a directory called ‘chaindata’.
chaindata sounded interesting but appeared to be empty:
However, Windows sometimes won’t show information about a file until it is written to disk in entirety or the data is otherwise requested. Investigating further, I ran some more commands, my first guess was to try to grep for the flag:
![]()
Not the output I was hoping for but it indicated something in the file did match flag so I decided to dig deeper. The next idea (and where all 4 challenges should have been immediately been solved) was to run the ‘strings’ command against the log. Strings pulls out common ascii-renderable characters from a file much like cat. It can be useful in CTFs when the designers may have hidden comments or other data in binary files or other objects. When I initially ran it I got a whole bunch of data so I then decided to pipe it in to less and saw the following:
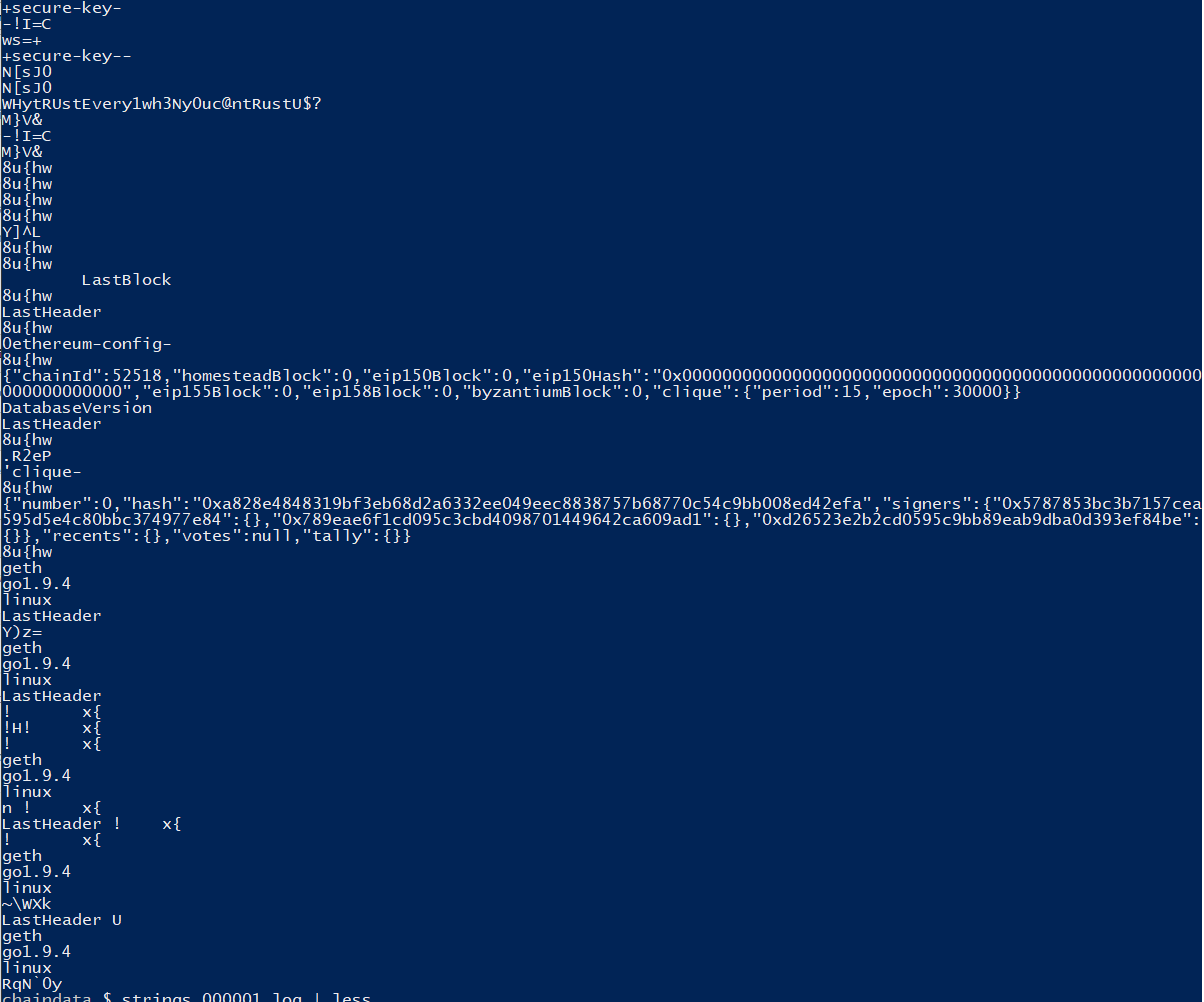
Sure enough, the first flag was right there! I submitted it and saw that the next one appeared to require more diving in to the blockchain so I promptly moved on to look for challenges that I was more familiar with (the challenges in the ‘web’ category which I will write about in the next post).
This concludes the section on ‘Founders Folly‘
At some point over the next day or so the second challenge was solved by someone on our team (#winterf3ll for lyfe!). When I sought out some challenges to work on I teamed up to work with @eidolon. He was looking at the the 3rd in this series of challenges.
This challenge provides an ‘.abi’ file which is loaded with eth and which then provides additional commands. However, those commands must be executed by the owner of the contract (or they should need to be executed that way). After getting frustrated trying to grasp wtf the structure of ethereum was I decided to return to the logs!
This time, instead of doing a raw strings command I ran it as follows: strings -n 15 filename and received the following data ( this is the top of the file, it actually produced multiple pages so I did not see the flags which are visible here.)
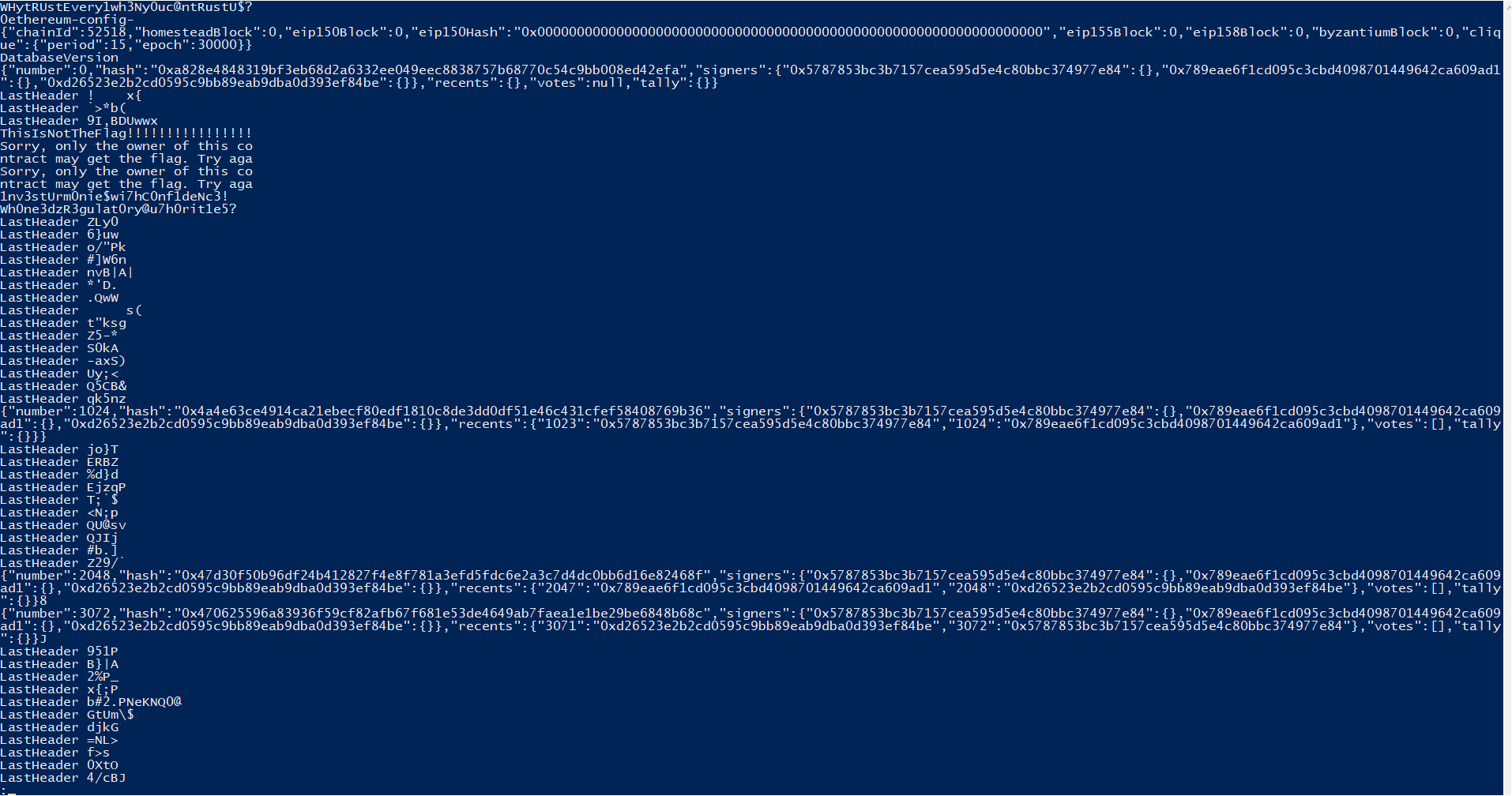

The first thing to notice here is that there are multiple repeated phrases and things which are exclude-able with a grep. I decided to run the command with those exclusions and ended up with strings 000001.log -n15 | grep -v "LastHeader" | grep -v '{"n' which excludes the “lastheader” lines and lines which contain: {“n
This returned a single page response:
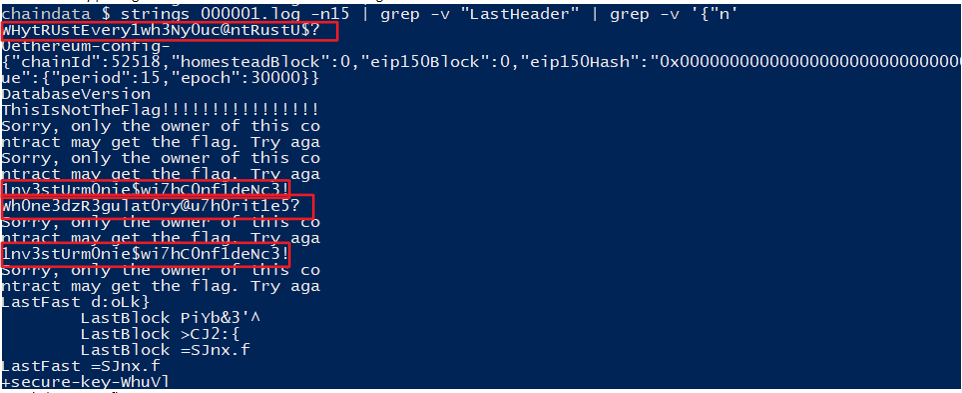
Sure enough there were multiple flags! The first one we already found in Founder’s Folly as well as, presumably, the one found for step two. @Eidolonpg and I submitted the 3rd and 4th flags to obtain the points and they registered successfully!
LayerOne Rocks!
I cannot recommend LayerOne enough! If you’re in Southern California grab your ticket early and make some time for this event! LayerOne draws outstanding speakers and provides some amazing villages – hardware hacking, lock picking, IoT, CTF, tamper evident and more! Experienced professionals and hobbiest from all parts of the industry are around. Go learn some stuff!