Introducing Battalion
Over the past 2.5 months a friend – @eidolonpg – and I have been working on a tool which was spawned from the previous articles written here. If you’ve read the past few posts have been about ‘Reconnaissance’ and, lately, chaining various recon tools together you’ll understand how this came to be. Battalion is the product of those experiments. If you just want to try it out go here: https://github.com/theabraxas/battalion
Battalion will, in short, allow the pentester or sysadmin to input a company name and website, wait a few minutes, and be presented with a practical, clear, and in-depth report. Some of the data gathered by Battalion will include:
- Users at the company involved in breaches
- Thorough DNS enumeration, IPs, and zone-transfer status along with valuable included data such as record types (including TXT and SPF & associated service) and more
- Shodan queries on each IP and subdomain to return used technologies, open ports, detected vulnerabilities and more
- A beautiful EyeWitness report allowing for quick scanning of banners and http/s pages
- A list of high-probability employee email addresses
- Whois data for most domains
- Registrar data
- Predicted, company-owned, netblocks
- Much, much, more
How it works
Battalion is, essentially, a series of inputs and outputs fed through a series of tools which, ultimately, generate a large set of data. This data is then manipulated, extracted, and combined to provide an easy to and utilize report. The utility itself has two primary phases: User-Scanning and Domain-Scanning.
User-Scanning
This process takes one of the two initial inputs – ‘Company Name’ – and runs a few operations and tools on it. First, Battalion uses the tool known as ‘TheHarvester’ in order to extract current and past employee names from LinkedIn via a ‘Google Dork’. These names are then manipulated in to probable email addresses (ie. [email protected], [email protected], [email protected] – and so on). Battalion generates 14 variations of email addresses. Once generated, Battalion tests to determine the idiom the target uses. In particular, the HaveIBeenPwned API is utilized to test addresses and find proper matches.
After a matching format is found the process moves to the next stage. Breach detection occurs after the ‘bad’ addresses are removed and consists, again, of using the HIBP API to check each email address. This will, ultimately, output a list of email addresses with associated breaches, if any were detected. So far this process has been highly reliable and efficient!
At the time of writing, this is essentially the end of the ‘User-Scan’
Here’s a diagram of a bit of what happens

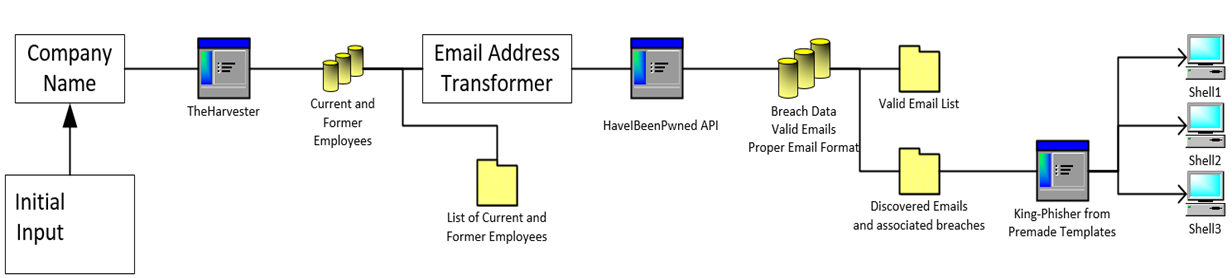
Domain-Scanning
This is a more complex process than the former and relies on the ‘website’ input provided initially. The first step is to kick off a sub-domain brute force scan and extract some other information. The goal of this first stage is to get a list of DNS records as well as info such as ‘Who is’ data.
Once enumeration completes, a series of tools is kicked off in parallel. These tools include EyeWitness, Shodan API, WhatWeb, nmap, and a few others. Just prior to those tools kicking off we have custom parsers and processes to format inputs for each tool as well as test to make sure only things like HTTP/HTTPS sites are fed in to EyeWitness.
Here’s a diagram of a bit of what happens in this process

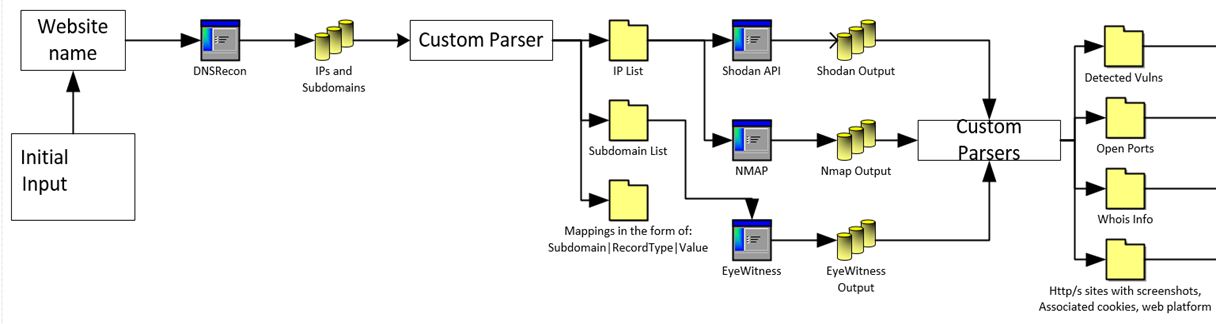
Reporting
One of the largest goals we hoped to bring in to Battalion was to create useful and time-saving outputs. Many of the files are immediately usable by pentesters and the report should be useful both to the pentester for reporting, blue-team for quickly finding and closing their largest gaps, and others – such as C-levels – to quickly glimpse the status of the reconnaissance. This will be our immediate development focus as we want to improve this and standardize on a format before we continue adding more features.
Future Development
More tools! More depth (auto-exploitation, anyone?!?) and more detail!
Toorcon!
Thanks to everyone who attended the Toorcon talk where I presented Battalion! I’m especially grateful for the awesome feedback, I hope to keep developing this with @eidolonpg and build in more of the features you request!