The Conference
The LayerOne conference has been a highlight for me each year since I started hacking and doing security things. I highly recommend it for anyone interested in security, electronics, radio, computers, or anything to do with hacking. It tends to emphasize getting hands on and learning through experience and from a phenomenal group of attendees. Check out their site at https://layerone.org and try to attend if you get a chance!
This years conference was was my first time back in person since 2019 and I was able to spend about some time on the CTF with a few other friends.
The CTF
The CTF had around 50 challenges and Psychoholics won (again) with 4890 points. This write-up will cover solutions I was a part of or which were shared after the event ended. Feel free to share solutions not covered here; I will try to include files of challenges where it makes sense.
Here’s the leader board fromthe end of the event:
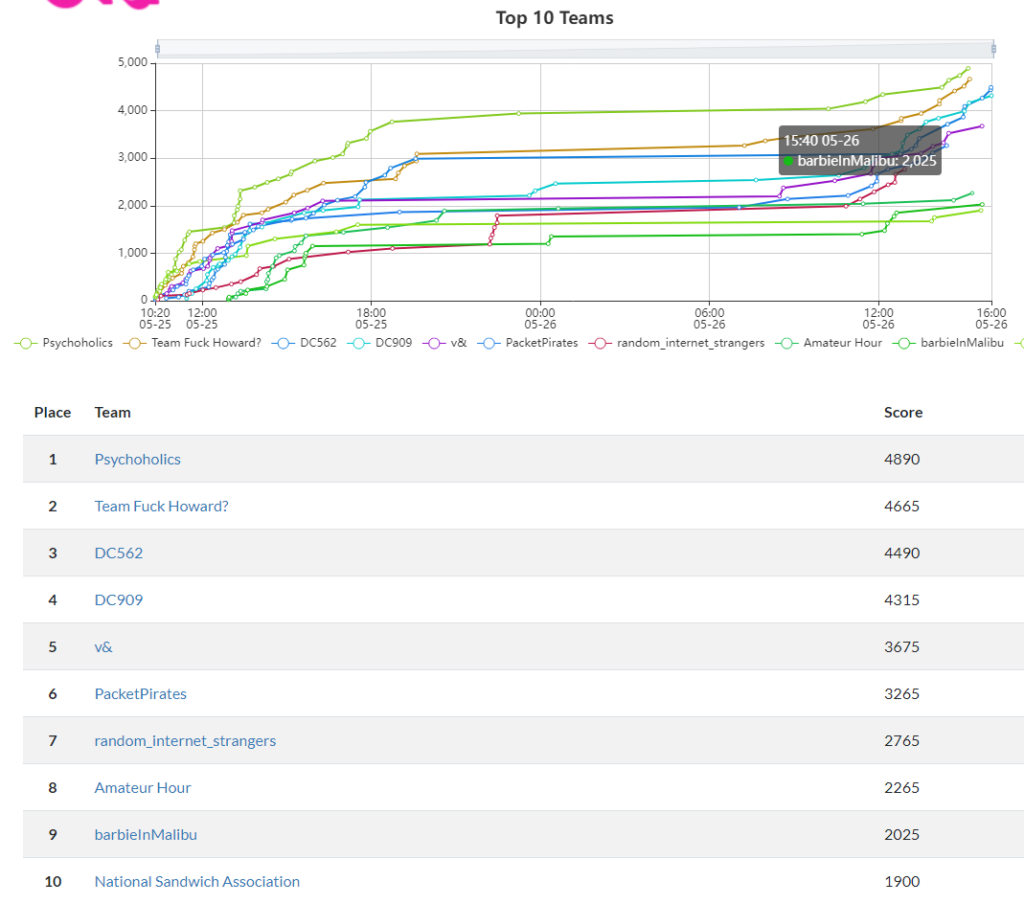
There were a good variety of challenges across a wide set of categories, use this table to navigate to the challenges you’re interested in. Here’s an archive of the challenge files if you want to follow along or try before reading!
- Reversing
- Web
- Exploitation
- Barbie’s Dream Card
- Decoding
- Cryptography
- Physical
- OSINT
- Networking
- Misc
- Datagram’s Challenge
- Forensics
- Cracking
Reversing
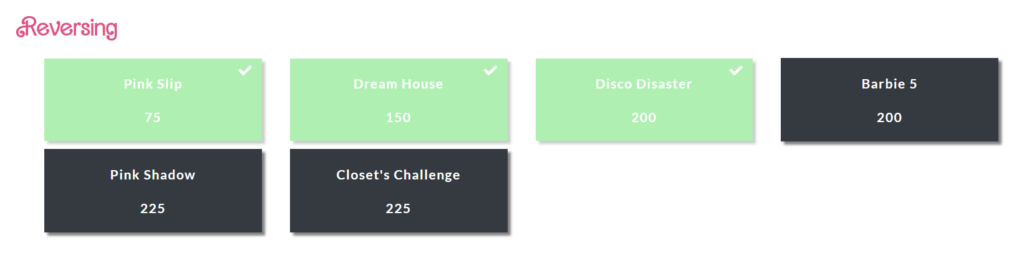
These challenges revolved around reversing binaries to find the flag.
Pink Slip – 75
“Pink Slip” was the first binary in the group, it simply displayed a fancy ASCII barbie when it ran followed by some text and a random-looking string.
Before going too deep into it, I just ran strings on the binary to see what I could find out. As one might expect from the first reversing challenge, the flag was right in the text! Never underestimate strings.
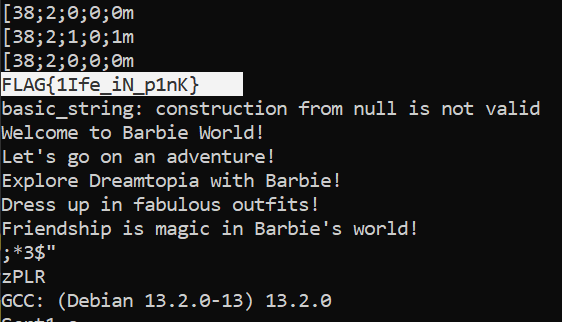
Flag: FLAG{1Ife_iN_p1nK}
Dream House – 150
The second reversing challenge was dream house, which, when run will show an ASCII house with a prompt to input a door code:
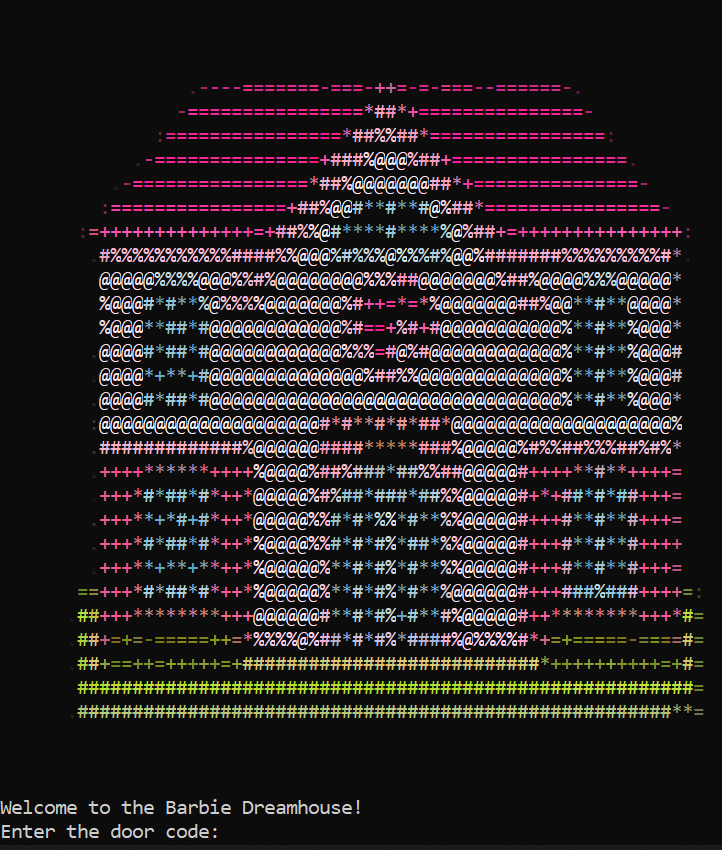
A wrong answer will get you a classic ‘Access Denied.’ message:
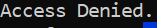
This time around, strings did not do the trick so the next step was to open it up in radare and see if we can make sense of it. I opened the binary with radare, ran aaa to analyze the file then ran afl to list the functions:
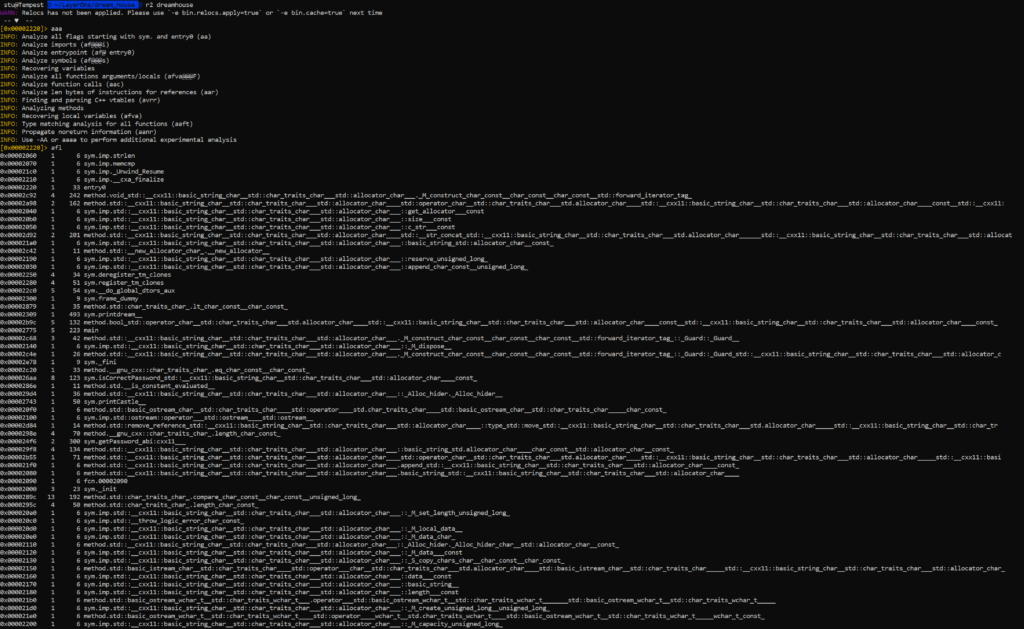
The function I was most interested in was the getPassword function so I decided to analyze it with s sym.getPassword_abi:cxx11___ followed by pdf to display the function breakdown. I was able to see this:
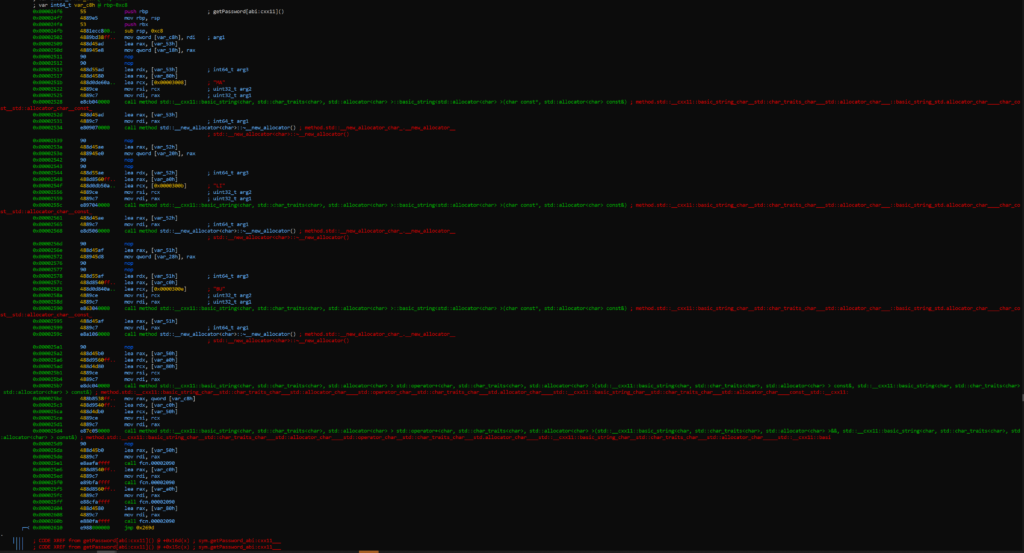
From here a teammate put together that MALIBU’ was probably the password so we threw it in and got the flag!

Disco Disaster – 200
This was the last one I was able to solve in this category. This was another binary like the last which seemed solvable in a similar way but actually had more going on.
When you launch the binary it ask if you want to restart the music server. Looking at the binary it looked like ‘y’ or ‘Y’ were sufficient to do this but no matter what you put in, it wouldn’t actually branch to the function you wanted called ‘playMusic’.
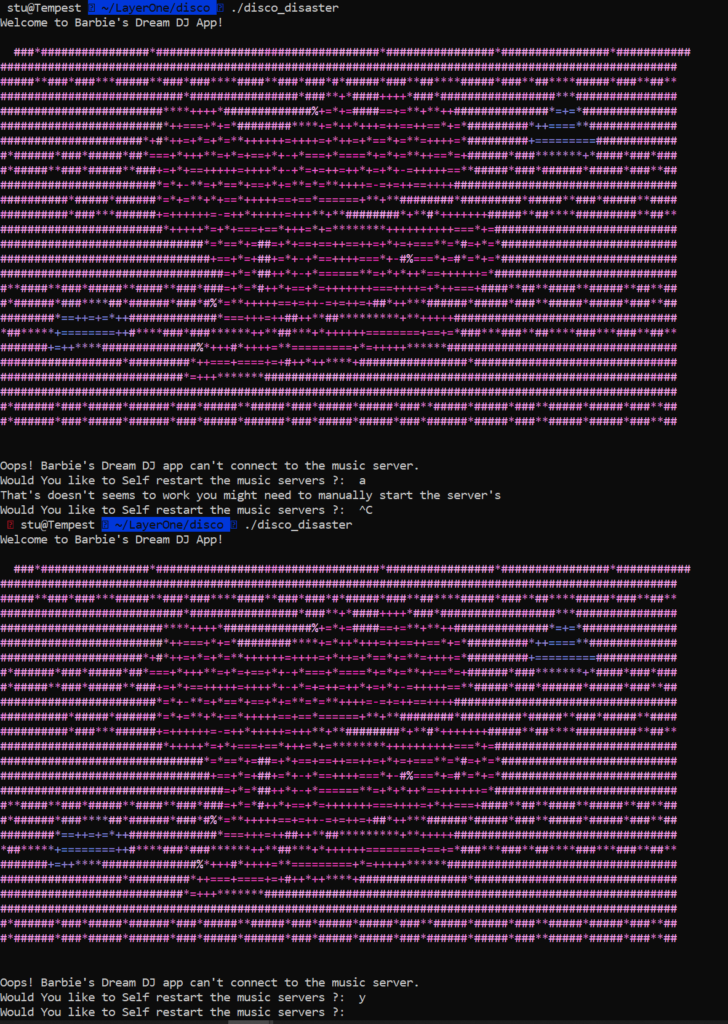
In order to solve this one we had to patch the binary to bypass the check on the input and go to the function we wanted. I used chatGPT to write some exploit code (since they love when you ask it to do that) and got this nice script:
from pwn import ELF, p32
# Load the binary
binary = ELF('disco_disaster')
# Address of the start of the main function
main_base = 0x00002502 # Start of main
# Address of play_music
play_music_addr = 0x00002637
# The point where we insert our jump to play_music
# Replace the prompt and input logic that starts at 0x00002554 (the call to basic_string constructor)
insertion_point = 0x00002554 - main_base # Relative offset from start of main
# Calculate the relative jump offset from the insertion point to play_music
# The offset needs to account for the size of the JMP instruction itself, which is 5 bytes
relative_offset = play_music_addr - (main_base + insertion_point + 5)
# Create the JMP instruction with the calculated offset
jmp_instruction = b'\xE9' + p32(relative_offset & 0xFFFFFFFF) # 32-bit relative offset
# Write the JMP instruction at the calculated insertion point
binary.write(main_base + insertion_point, jmp_instruction)
# Fill the remaining bytes up to the original call to play_music with NOPs to prevent any accidental execution of half-overwritten instructions
nop_fill_size = 0x2637 - (main_base + insertion_point + 5)
binary.write(main_base + insertion_point + 5, b'\x90' * nop_fill_size)
# Save the patched binary
binary.save('patched_binary')
from pwn import ELF, p32
# Load the binary
binary = ELF('disco_disaster')
# Address of the start of the main function
main_base = 0x00002502 # Start of main
# Address of play_music
play_music_addr = 0x00002637
# The point where we insert our jump to play_music
# Replace the prompt and input logic that starts at 0x00002554 (the call to basic_string constructor)
insertion_point = 0x00002554 - main_base # Relative offset from start of main
# Calculate the relative jump offset from the insertion point to play_music
# The offset needs to account for the size of the JMP instruction itself, which is 5 bytes
relative_offset = play_music_addr - (main_base + insertion_point + 5)
# Create the JMP instruction with the calculated offset
jmp_instruction = b'\xE9' + p32(relative_offset & 0xFFFFFFFF) # 32-bit relative offset
# Write the JMP instruction at the calculated insertion point
binary.write(main_base + insertion_point, jmp_instruction)
# Fill the remaining bytes up to the original call to play_music with NOPs to prevent any accidental execution of half-overwritten instructions
nop_fill_size = 0x2637 - (main_base + insertion_point + 5)
binary.write(main_base + insertion_point + 5, b'\x90' * nop_fill_size)
# Save the patched binary
binary.save('patched_binary')Running the script outputs a patched binary which we can run and which gets the following results:
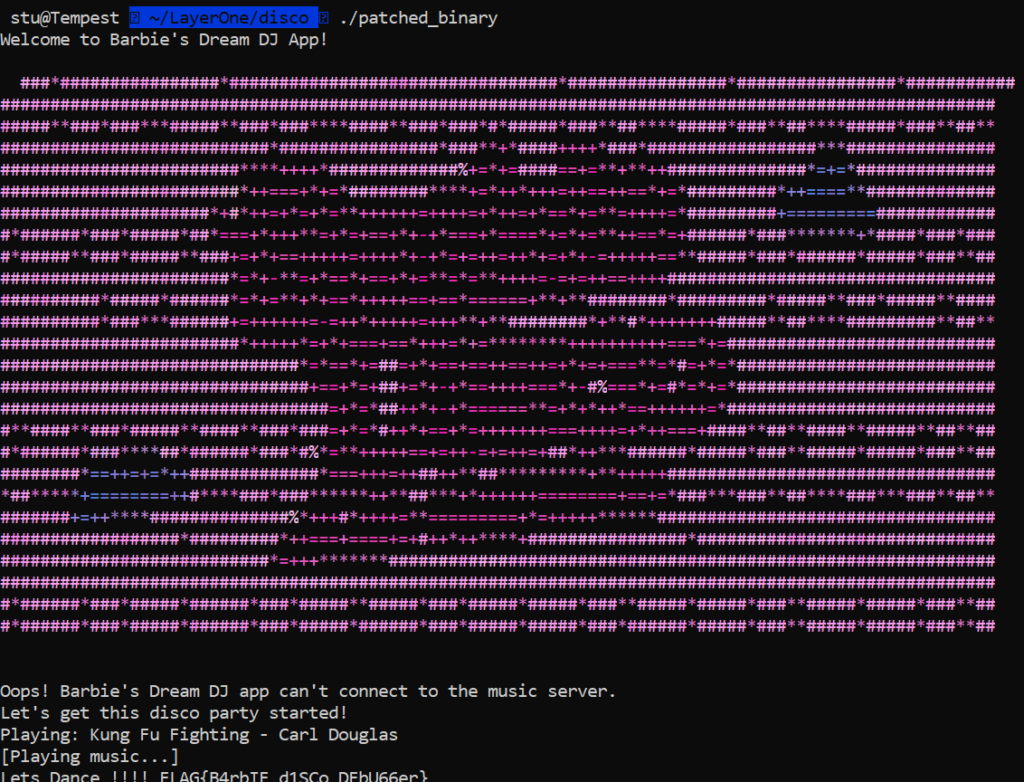
Barbie 5 – 200 (Unsolved by us)
Pink Shadow – 225 (Unsolved by us)
Closet’s Challenge – 225 (Unsolved by us)
Web
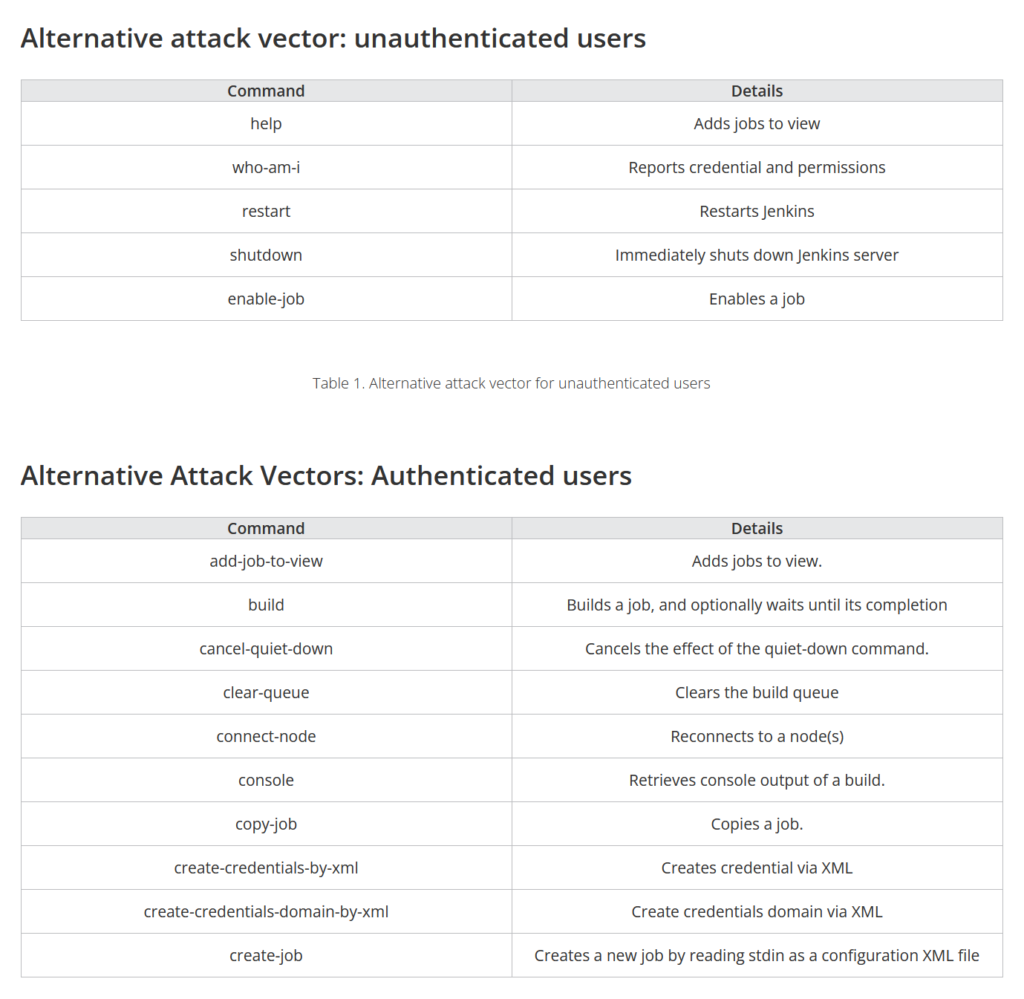
The web section was really fun this year. A lot of it was based around a vulnerable Jenkins instance. I based most of my solves off of this article: https://www.trendmicro.com/en_us/research/24/c/cve-2024-23897.html . I installed a local Jenkins (Local only, of course. You’ve gotta be careful at these CTFs) to get jenkins-cli.jar which I then used on the remaining challenges. The below commands let you, when specifying a file, read the first few lines while unauthenticated or the whole file when authenticated:
CI/CD 1 – 90
To solve this first challenge, we have to read ‘flag.txt’. Based on the description it makes sense to try to read ‘flag.txt’ at: /var/jenkins_home/flag.txt.
If we run the jenkins CLI with @/var/jenkins_home/flag.txt we get the flag!
Spill the Tea – 100
Unattended Install 1 – 100
This one was similar to CI/CD-1 except that instead of finding the flag at /var/jenkins_home/flag.txt, you check the ‘default’ location for the admin credential on a new setup which is located here:
/var/jenkins_home/secrets/initialAdminPassword
This lets you log into the Jenkins server. From there we are able to create jobs/builds. Doing things like ‘ls’ and ‘find’ and things of this nature let us find the flag file in the jenkins home directory.
Barbie’s Dream Site 2 – 100
CI/CD 2 – 125
Using the same CVE as the first CI/CD challenge, we are able to look around. We still don’t have credentials to log into the server though. My initial thought was to try to read some data from places like ‘credentials.xml’, ‘/root/flag.txt’, and other locations but that didn’t yield too much. However, a good thing to know for CTFs (especially LayerOne?) is that each running process has its own nice place in /proc where we can get up to some fun. Specifically, by going to /proc/self/env we can see the environment variables associated with the running process. Doing this led to finding the admin credentials to the server AND a nice flag! 🎉🎉
CI/CD 3 – 75
This is the first CI/CD challenge since we’ve found admin credentials! With this access I looked around the interface and saw a separate account which might have a password to use but eventually made my way to the build management part of Jenkins. From here, we are able to run Jenkins builds as the Jenkins user which gives us a lot more freedom than before.
I ran builds with various commands like:
pwd
whoami
ls /var/jenkins_home/
ls /var/jenkins_home/secrets
cat /var/jenkins_home/credentials.xml
cat /var/jenkins_home/secrets/secret.key
cat /var/jenkins_home/secrets/master.key
I’m honestly unsure where the 3rd flag came from but it came out as a result of commands like that and exploring the system with the access we had. The secrets & master key files were helpful for the next challenge!
CI/CD 4 – 150
As mentioned in CI/CD 3 we found a secret and master key file. We were also able to read the credentials.xml file. The credentials.xml file contained a password to decode. The results of one of my jobs captured all of this:
cat credentials.xml
<?xml version='1.1' encoding='UTF-8'?>
<com.cloudbees.plugins.credentials.SystemCredentialsProvider plugin="[email protected]_d7b_c7b_c9f">
<domainCredentialsMap class="hudson.util.CopyOnWriteMap$Hash">
<entry>
<com.cloudbees.plugins.credentials.domains.Domain>
<specifications/>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
<scope>GLOBAL</scope>
<id>Flag4IsMyPassword</id>
<description>Decrypt my password for Flag4</description>
<username>Flag4User</username>
<password>{AQAAABAAAAAge8Er4K8ki5nC14jtCYtjwUX5WWBTWGUYH1ktBIrxx7x/R8ffNng8Qr1Ip8Zcs8FL}</password>
<usernameSecret>false</usernameSecret>
</com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
</java.util.concurrent.CopyOnWriteArrayList>
</entry>
</domainCredentialsMap>
</com.cloudbees.plugins.credentials.SystemCredentialsProvider>+
cat secret.key
1821502021c42d3fdb0e44eea2b93fa0a66512a8858ec03c5b0b0b0c11cac547+
cat master.key
6a11ea78b2903fe85eb43818a2f6d9b75cd632789d387749ca5a121f16cad4a52e76acd4aa8e2b07540cf88be640b1603db727143af4d09d9509908756de8d71a386fce99ac019481205f94aa154c73507704f9f644617ada9299fc353300350a15f1c602073f862387e369b910fd59f56a48884f9d9935481da2fefb1e1cc32+
After I found this info, I looked in to how to decode Jenkins keys and a teammate decrypted the password and got the flag: Flag4.DecryptedJenkinsPass9$5
Unattended Install 2 – 150
This is the same Jenkins as in the earlier Unattended Install challenge. Similar to Unattended Install 1 we can use our admin credentials to log in to the server and then get up to mischief. Using a command like find / -iname "flag" 2>/dev/null in a build led to us finding the other flag!
Barbie’s Dream Site 3 – 150
We did not solve this one.
Barbie’s Dream Site 1 – 200
We did not solve this one.
Exploitation
DreamPool License Activation – 175
We did not solve this one.
Barbie’s Dream card
Barbie’s Dream Card 1
This one drove me mad. Solved it after the CTF and can write it up here. The CTF had a fun element this year where each team was given a card to swipe for some challenges. The first challenge was based entirely around finding the flag on this card:

So, the numbers all look like they are in the ASCII range and the result of transforming the 16 numbers into 8 characters is: JQYUGVCG However, this is as far as I was able to get 🙁
I was too preoccupied looking for secret things in the background (I thought maybe ‘Barbie’ was a keyword to use in a keyword shift cipher, I thought maybe the values should be divided by 8 or 32 or otherwise messed with. It never entered my head that the 0B wasn’t an 08 and that the 0b might mean ‘base’.
To solve the challenge, convert the JQYUGVCG string to base32 and you get L1CTF which was the flag.
Barbie’s Dream Card 2
Unlike the last one, this one was way easier! The CTF had a card scanner we could use to swipe the card. Swiping the card while it was connected to a notepad program or terminal resulted in the data printing to the screen.
This is the resulting data:%L7481898571866771^JQYUGVCGPNGTIR2TG5JDCUBTKNPUCUSSL5JVIMKMJRPVEM2MGNLDITSUPU======?;7481898571866771=3211=8468706886698961?+DESIGNED BY KAJER FOR THE 2024 LAYERONE CTF ^ HTTPS://SOMUCH.BEER/KAJER/L1CTF?
The block of text after the ^ looked interested so we messed with it and it decoded as base32: L1CTF{M4GS7R1P3S_ARR_ST1LL_R3L3V4NT}
Barbie’s Dream Card 3
The prior challenge included a URL. At this URL there was a transactions sqlite file. Presumably the flag is in there somewhere. It’s also possible the spot after the base32 and before the URL contained some flag information.
Decoding
Ken’s Challenge – 50
I am kenough to decode this cipher
This is a pigpen cipher and one of the guys on the team promptly decoded it. Even if you don’t know that it’s a pigpen cipher, as it’s a substitution cipher you can transcribe each unique symbol to a unique character and put those characters in the order they appear and try to decode with a substitution cipher such as https://quipqiup.com/
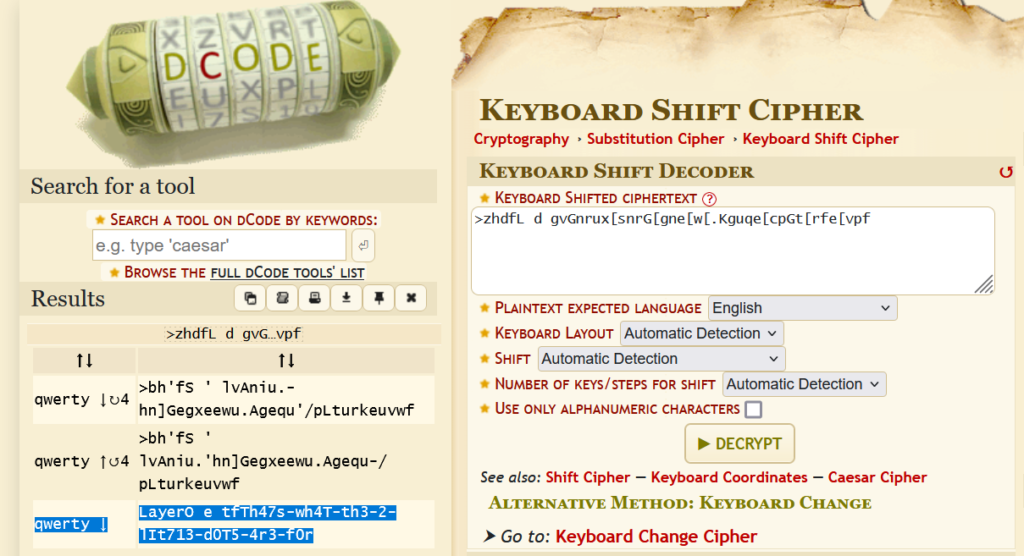
Barbie 2 – 100
The flag.txt file here contains a weird looking string:
>zhdfL d gv{Gnrux[snrG[gne[w[.Kguqe[cpGt[rfe[vpf}
They also note the {} characters are not part of the cipher. I dropped it into some online solvers and shiftciphers and things like that but had no luck. As we didn’t see any obvious clues it made sense to manually look at it. Looking at the string, we can try some analysis by looking before the { character to see if there are any familiar patterns. By taking the first part of the string, >zhdfL d gv (right before the {) we can see if we can find any patterns. Eventually someone got the idea that maybe the eye mask in the picture was a hint that they were typing without looking at the keyboard.
Knowing that some of the flags start with LayerOnectf{ or ctf{ or flag{, we looked at the text and noticed that, for the last part of the string before {, the ” ” key is below ‘c’, the ‘g’ key is below ‘t’, and the ‘v’ key is below ‘f’. Essentially, by moving our hand up one row on a querty keyboard, we get ‘ctf’. From here we can go to dcode.fr and drop it in a keyboard shift cipher and, sure enough, the 3rd one looks pretty close! We can fill in the blanks and get LayerOnectf{Th46s-wh4T-th3-2-lIt713-d0TS-4r3-f0r}
Barbisaurus – 150
a
Barbie 3 – 175
Barbie 4 – 175
Cryptography

A Glamorous Quest – 175
Welcome to Barbie’s world, where dreams come true, In this cryptographic challenge, the spotlight’s on you. Barbie needs your help to crack the code’s spell, And unlock the secret hidden oh so well.
In the world of Barbie, you should easily see, Signatures need to be decoded, using a public key. Once you find the hash, it’s Barbie’s delight, A glamorous victory, shining so bright.
So grab your tiara, and your code in hand, Join Barbie’s quest, in her dreamy land. Unlock the secret, with style and flair, And celebrate your win, beyond compare!
RSA Signature:
0x10d80b1894975a3b439a6a0706e94577c189ac6fb918590cb011d7aa3ba5953187bcac9332d88c2b53f3f3d032eb85bc5629838a7c3b6cc5305ab03a823ff6bb3059177d86e88363a584ea6a8398ec79b399f1470e32fa2526ab9a78c61cd1dc3e6d9bd7fc514c2781a66e3d8a8753a23866f84da4b58afa24dde4ce0424650cd88b346509e5b9660a831b5278b163b5853538247ff66cff8a65e85b59a17da0a9c920c9ee20242894c073f9eeab4f3e7040e4c2b54c2e4c34663b3ac3dfc49c6887d17c06f48338394af5b7bfb85a738965dde0842d782f03501c5df9b191b7a47bc9f50c316e8a810ee75c2f4b427d9eed6845c3785bbd40bd0f2956ceb03c
Public Key Modulus (n):
0xC2A68ABA10A3195E26497131B4B0562155427BFDA828AE25787E890C014D31B4911D44A64EF4896A41A184087430CC4E21ED2932E24BBDCE9E78C2CE48670273C38AF92E8C22398E80C31BA9450AB0398A6A939582950F596CB4426B6A8F9ADB8AC4E30D02B3517E2459092052DCB8F70C08125AB9C2EE9C1FF8D20CB84F7C5EF9C36F4AACEB18AA511BED8169F5B25082A7D57ECF44904DEA9C3D6F273FA154309046129C9BE253A1AD6DBD0F205DF2A2CCEFE5B27CF939053FDF806C48350498BD22899CBD6DB97DBB52FCA0AB7A3B0EA62E861C1628F93E779BC021B5EAF1D91EA5385EED0C57C63E94940944CEA77CD55E3221F63FC0017FB146E1AF9067
Public Key exponent (e):
0x10001
Hints:
- RSA signature schemes typically involve the use of a private key for signing and a public key for verification.
- Remember that the public key is known to all and can be used to recover the hash.
- Research how RSA signatures are generated and verified to understand how the hash might be involved.
- Pay attention to the specific properties of the RSA algorithm and its mathematical operations.
- This can be done in Python with 1 RSA math operation.
- If you get a result that begins with 0x1ffffffffffffffffffff…, you have the correct result…you just need to parse to get the answer.
The flag is the hash you uncover.
Physical
Barbie’s Door Lock – 50
Clearly the 1,5,9,0 and # symbols have been used. Flag was: 0915#
Barbie’s Secret Locks 1 – 75
Had to pick the lock, not too hard.
Barbie’s Secret Locks 2 – 100
We didn’t solve this flag.
Barbie’s Secret Locks 3 – 150
We didn’t solve this flag.
Barbie’s Secret Locks 4 – 150
Solved this one with the process here: https://samy.pl/master/master.html
Barbie’s Re-pin Adventure – 150
We didn’t solve this one.
OSINT
Barbie’s Vacation City? – 50
Exif viewer found this to be ‘Palo Alto’
Mountain View
Barbie’s Hiking Location – 50

Google image search the file to find out it matches with Mt Rainier
Ken’s Beach Hideout – 125
We are San Diego locals so knew this was Coronado Beach. Not sure on the intended solve path.
Cyber Sleuth Adventures – 150
Networking
This appears to contain a lot of ICMP traffic, possibly data in the data byte on the ICMP packets. Looking at the ‘data’ field on the ICMP packets we can see there is a 1-byte value. Maybe if we put all the 1-byte values together we’ll get something.
This is the data when extracting the ‘data’ field on the ICMP traffic:
stu@Tempest ~/LayerOne/network_150 cat decoder.py
import re
import base64
from scapy.all import rdpcap, ICMP, IP
def extract_icmp_data(pcap_file):
packets = rdpcap(pcap_file)
ip_data = {}
for packet in packets:
if ICMP in packet and IP in packet:
icmp_packet = packet[ICMP]
ip_src = packet[IP].src
if hasattr(icmp_packet, 'payload'):
data = bytes(icmp_packet.payload)
if ip_src not in ip_data:
ip_data[ip_src] = ""
for byte in data:
if 32 <= byte <= 126: # Printable ASCII range
ip_data[ip_src] += chr(byte)
return ip_data
def clean_extracted_data(data):
# Remove non-Base64 characters
data = re.sub(r'[^A-Za-z0-9+/=]', '', data)
# Remove duplicate consecutive characters
cleaned_data = re.sub(r'(.)\1+', r'\1', data)
return cleaned_data
def decode_base64(encoded_data):
try:
decoded_data = base64.b64decode(encoded_data).decode('utf-8')
return decoded_data
except Exception as e:
return str(e)
pcap_file = 'data_exfil.pcapng' # Replace with your pcap file name
ip_data = extract_icmp_data(pcap_file)
for ip, data in ip_data.items():
cleaned_data = clean_extracted_data(data)
decoded_data = decode_base64(cleaned_data)
print(f"IP Address: {ip}")
print("Extracted Data:", data)
print("Cleaned Data:", cleaned_data)
print("Decoded Data:", decoded_data)
print("-" * 50)Running the script, we get:
stu@Tempest ~/LayerOne/network_150 python3 decoder.py
IP Address: 192.168.29.149
Extracted Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiWell well well ... you got me ...abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghinow another step is to get the flag ....aW1jcF9kYXRhX2V4ZmlsCg==
Cleaned Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiWelwelwelyougotmeabcdefghijklm
nopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghinowanotherstepistogetheflagaW1jcF9kYXRhX2V4ZmlsCg=
Decoded Data: Incorrect padding
-------------------------------------------------
IP Address: 192.168.29.107
Extracted Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghi to get the flag ....
Cleaned Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghitogetheflag
Decoded Data: Incorrect padding
--------------------------------------------------
IP Address: 192.168.29.90
Extracted Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiWGe.>l=l[ t&wa>el-lj QwCe4lXl ).-..oY l y6ouE )Pgt cmet ?.qa..Na00W#11j/pDcFp9`XqkYPXRfh*X52V@4ZzmlEs]C8gi=wG=-8
Cleaned Data: abcdefghijklmnopqrstuvwabcdefghiabcdefghijklmnopqrstuvwabcdefghiWGel=ltwaeljQwCe4lXloYly6ouEPgtcmetqaNa0W1j/pDcFp9XqkYPXRfhX52V4ZzmlEsC8gi=wG=8
Decoded Data: 'utf-8' codec can't decode byte 0xb7 in position 1: invalid start byteBase64 decodes to: icmp_data_exfil
MISC
Read the Rules – 25 DONE
Find the flag in the rules.
Join Discord! – 25 DONE
Find the flag in discord.
Follow us for a Flag – 25 DONE
Follow them.
Barbie 1 – 75
This was a recursive compression challenge. It was zip, tar, and a format called ‘allegro’. Allegro was not a format we were familiar with and we didn’t get around to decoding it. It looks like to decompress the allegro files and continue on required something like using the allegro library to initialize, open, read, and close the file in some order to properly decompress.
Find the Missile – 100
This one was cool, it was a picture of a waveform which had to be decoded:

To decode it, we used a program called photosounder – it gave the result of /Area51_Nevada_US/ and we got the flag.
Help a Friend – 150
I really liked this one. To get the points you had to work with someone from another team, guide them through how to get a solution on a non-trivial challenge, and then you could get the points from this challenge.
Datagram’s Challenge
You Wear It Well Part 1 – 100
My first thoughts on this challenge were that it had something to do with the badge. I didn’t have time to look at the badge but the next day I saw the shirt for the con and realized that the string on the outside of it might be a code for this challenge.

Transcribing this string gives us this:
54484953204953204E4F54205448452054485245414420594F552053484F554C4420535441525420574954482C2042555420594F5520444F204E4545442049542068747470733A2F2F7777772E6C617965726F6E652E6F72672F70756C6C5F7468655F72696768745F746872656164
Since there were hex values there and a lot of 6X and 7X characters, I though it might be ASCII. Dropping the string in to quipquip is all it takes to decode it!
Going to the website provided gave us the flag. It also gave us the start of steps to get to the second flag. The staff at the con were supposed to have a shirt with a different code but something didn’t work out. They provided the second flag shirt image here:

The website also contained this text:
9ec259e7bfe5e8ce4dcbcde11614431296a094e6fa7214de850501956ee84a901720cc52870b58413b1ee5f70c59a0
aef104abb62d36887ba0b2de004cf5bd773a15416ab1632a681711695729cf3e74abfc0a928fc56f52289b782532ae
bb4e69ad4f2003b78ffc77ba4fa8ab5dc9e63a28bc35f916e9b7eec92f13c51f8f3f19d0afa4868482a2d2fb3010ff
07c66f8669023b37bf1c3b26a5df33c57bf6f32453f106ffe1c43e92ac4b98936e47a2493b496883e5ae64138236a5
5e1d4dcd852c1007916c5c51112a09e8785956cfbe603494267ba6ee6206523d1387a5f75f032046ddc51283dbbeb6
b8770a8e68d5b1528cc1753d0c5f88ae1cb84e0eb8610da8775668327e76638a0fc39848a46dc8535c5d96068e36ae
ab42be95da9812126743b472d04bcbc31de7c40299817d0be46aa32172fb806cd03f249cdb6a4da336fad4ab90eeed
c765744ffdd8529d963eb4ceb30a9c8729b3bd933b1a35e6f5448a745ffed398fce75b907d69bdb9599930beb4b533
0cc25b74cbd8fb53dc9b5b27b19b1f61b8b56f99c11d4adc943ad1b9c99a82c79107286821d215297c8c47f6c78ad6
901ed2a4ea7940dc16d09832fe73a4ed36da3471656a39de55f990c97e42b2f2ee287198815266d6488d9262c5a67e
2a43587719f7db2e047f3ca9c5aadd9a930bd679dbfca3bf4ba8a64f188f99327edc83508b658fcd4cbd61018ebb3a
9706e905b4220b3fa2c930d907f01129784a6545d3cf45dd615c24aac58a05b48d3a0af9344b5364553f
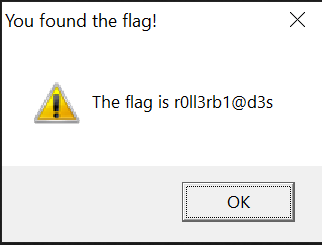
We did not complete this one but it’s based on the prior information.
Forensics
Barbie’s Vacation set – 75
This one was just a matter of looking at the file and seeing it’s an exe and running it.
Barbie’s Date – 75

This one was a photo which had some geolocation data. Fortunately, our team is from San Diego and knew this was Hinotez. The geolocation was for Coronado which is maybe 20 minutes away from where this was. You could probably also get it from image search and/or filtering San Diego for Japanese places.
Cracking
Crack iOS – 50
And that is that, thank you for reading and I hope this helps with future CTF challenges!