My first CTF challenge was Ernst Echidna which is a simple web page (here) which had a register page. After inspecting the requests when interacting on the site and by checking the robots.txt file, we were able to determine that there is a /admin page which you attempt to arrive at but are not allowed to access.
Here’s what those pages look like:
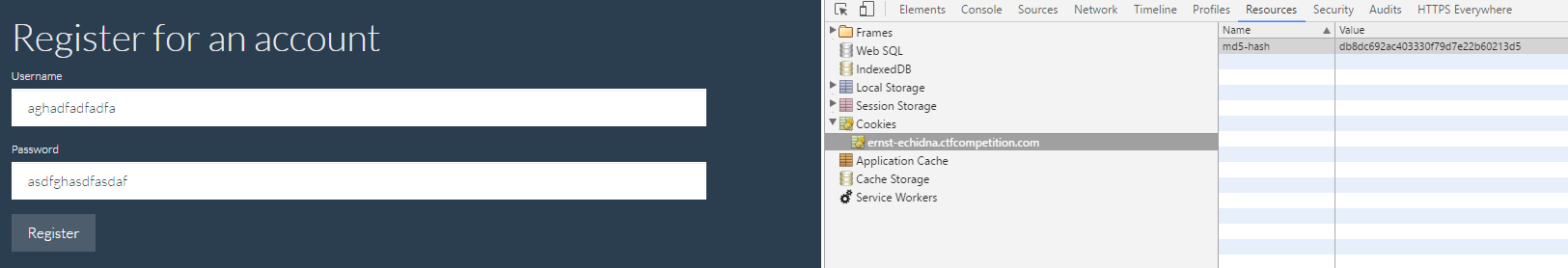
By submitting a username and password to the register page we get a new cookie called ‘md5-hash’. The hash is an md5 of the username we pass it which I determined by quickly using python:
asdf = md5.new("aghadfadfadfa")
asdf.hexdigest()
'db8dc692ac403330f79d7e22b60213d5'
This matches what happens when I put that gibberish username in the resulting cookie
Knowing what we do now, we can try to impersonate the ‘admin’ cookie by generating the hash and then submitting it with curl. If it works we will then be able to access the admin page.
The follow curl requests will send the correct information to get access to /admin which then presents us with the flag!
curl -D https://ernst-echidna.ctfcompetition.com/admin --cookie md5-hash=21232f297a57a5a743894a0e4a801fc3
And that is how to solve Ernst Echidna.
As this was my first CTF and one of my first challenges, there are some takeaways I’d like to suggest for any other beginners.
- Learn curl. It can do so much stuff. Following redirects, viewing/changing cookies, return lots of data, etc. Curl is full of useful things.
- Check robots.txt – there were a few challenges which were made much more do-able by checking this.
- Learn to recognize or have guesses at the different kinds of hashes and encoding (md5, sha, base64, etc.) It will help data, which may otherwise look like gibberish, stand out.